Survey Report: The Value of Threat Intelligence
It likely does not come as a surprise to anyone in the cyber security industry that there are two types of companies: those who have discovered they have been breached, and those who have not yet discovered it yet. In fact, according to a recent survey performed by industry analyst Michael Osterman, two out of three organizations have been infiltrated with malware through email alone. The bottom line is that traditional security approaches are manifestly not adequate to protect an organization’s critical assets. With that purpose in mind, we teamed up with Michael Osterman to best understand how organizations purchase and apply threat intelligence. This survey unearthed some interesting trends in the cyber security Industry. Here, we’ll focus on a couple of the survey’s findings related to the prevalence of breaches and the use (or not) of threat intelligence products.

The Situation
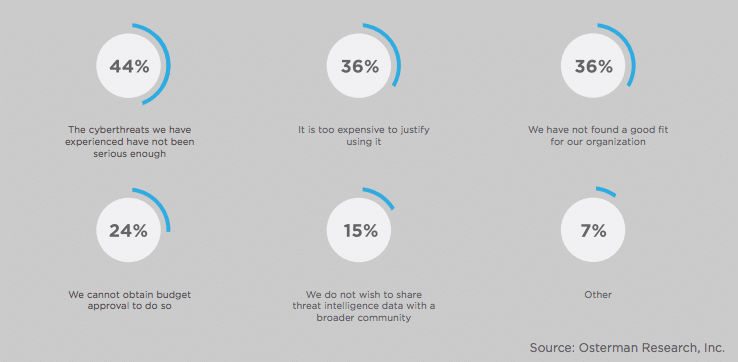
In our survey, we found that nearly half (46%) of the responders did not use a threat intelligence portal. This is concerning statistic given the prevalence and consistency of breaches. Cybercriminals are becoming more complex and targeted in their attacks. They have a wide range of weapons to attempt to infiltrate their potential victims, including phishing/spearphishing emails, spam, botnets, malware and social engineering. Below are a few examples of these types of threats:
- Threats delivered via email contain domain information in links and sometimes the source domain or IP from the email itself.
- Botnets will contact command and control IP addresses (and sometimes domains) used in attacks that can be discovered when analyzing logs for DNS lookups of nonsensical domain names.
- Malware can be reverse-engineered to extract relevant information like IP addresses or domain names.
How Threat Intelligence Can Help
A commonality among these types of threats is that virtually all of them contain domain and/or IP information that can form the basis for domain/DNS-based investigations. All online activity leaves a trail of information that involves IP addresses and domains. There is valuable and potent information that lie within these pieces of data that will allow organizations to improve their security posture such as:
- Information about the behavior of domains and IP addresses tied to threats can be used to develop information about individuals or entities that control the infrastructure, including intent, techniques, objectives and more
- The ability to expand the scope to investigate what these domains are connected to in the internet can reveal important information about the broader network of connected criminal infrastructure
- Ways to proactively monitor in order to discover and assess- or defend against new domains very shortly after they are registered
Learn More
To dive deeper into the survey data and gain insight into:
- The ability to pinpoint the identities of cyber attackers
- How these criminals operate
- Techniques used to predict and block future attacks




