Going Live with Splunk SIEM 5 and Doing More with Splunk SOAR
Share this entry
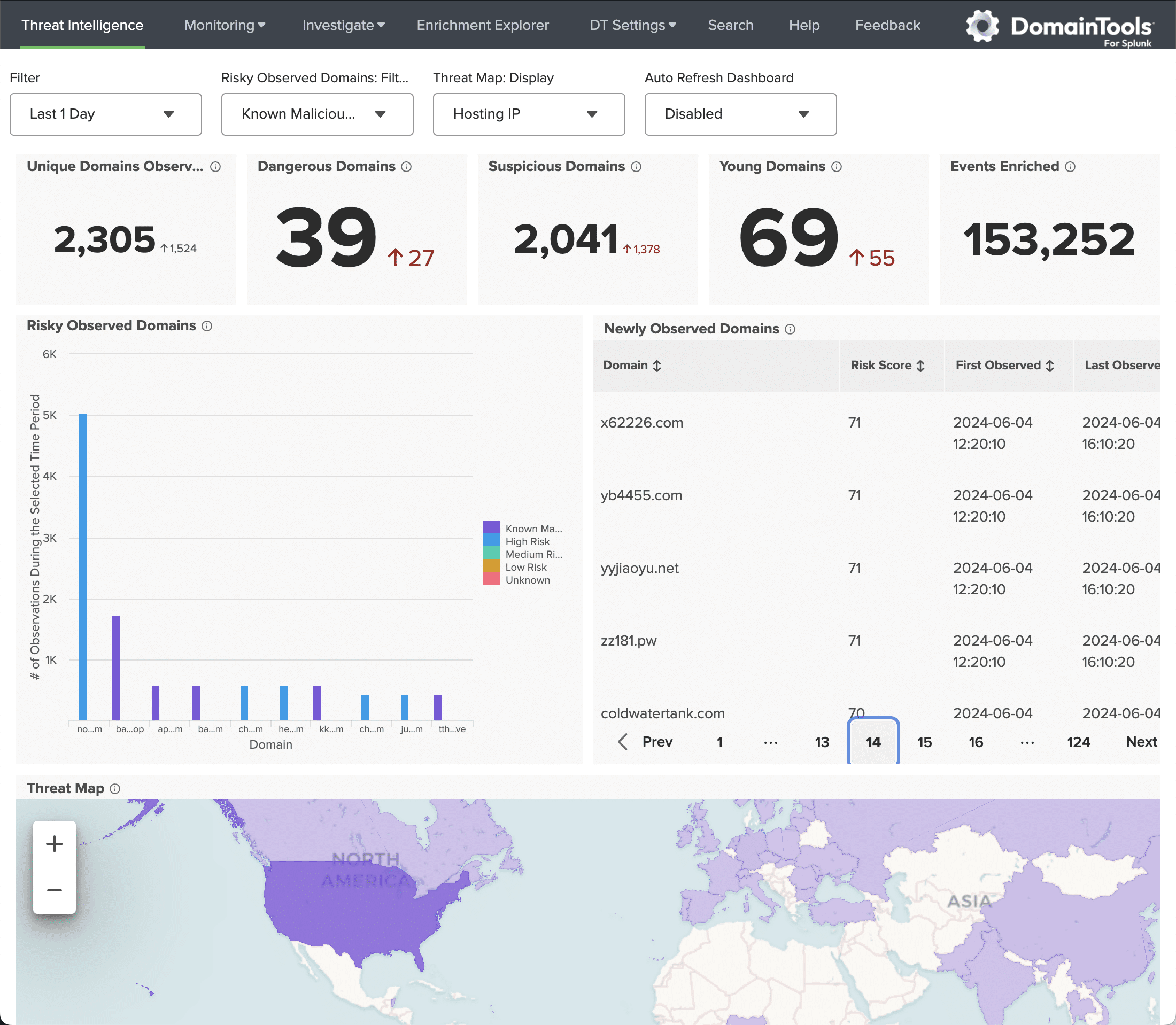
Enriched and Actionable Context for Malicious Connected Infrastructure
Threat actors have long abused DNS for the delivery of phishing campaigns. Using Large Language Models (LLMs) and targeting mobile users has allowed malicious activity to scale. These demands scaled contextual data in the SOC, giving SIEMs and other platforms more to manage. Executing high-volume queries with low latency can turn context into actionable intel.
Today, we’re thrilled to announce the latest DomainTools App for Splunk, Splunk Enterprise Security (ES) and Splunk Security Orchestration Automation and Response (SOAR). With these enhancements, Splunk users can use DomainTools to:
- Enhance investigations with the largest real-time historical Domain and DNS infrastructure database.
- Swiftly prioritize indicators of compromise (IOCs) to remediate effectively and improve security posture – reducing overall cost.
- Access pre-weaponized domains to reduce the threat of phishing, malware, and spam across the network.
While domain and DNS infrastructure intelligence is only one component of forensics, incident response, phishing, fraud prevention, threat hunting, and brand protection – the saying remains: it is always DNS. See how Splunk users can quickly enrich logged domains and mitigate the most prioritized threats directly within their application through:
- Iris Detect APIs for compiling phishing domains
- Native search commands for DomainTools Iris and Farsight DNSDB so they can more easily scale on their terms
- IPv4 information at scale from Farsight DNSDB built into workflows
- Additional domain attributes like SSL Durations, Website, and SSL Subject Alt Names for subdomains
- Earlier detection of phishing domains via Predictive Risk Scoring
- -search hash queries + “first seen within” parameters are used in Splunk SOAR to do hunting
Splunk & Splunk Enterprise Security
More contextual data can be uncovered in Splunk and Splunk ES by leveraging the Iris and DNSDB datasets for immediate access to dozens of attributes attached to every domain event in Splunk.
- Enhanced Alert Correlation: Allows users to link specific alert attributes (e.g., domain values) to relevant searches within the Splunk platform. This enhancement enables users to quickly pivot from alerts to related events, facilitating a more efficient investigation process.
- Alert Triggering: Enable Non_ES customers to configure and trigger alerts using the KV store. Users can define alerting conditions, thresholds, and actions within the KV store, allowing for seamless integration with external automation processes or alerting systems.
- Error Identification: Identify common issues customers face during the upgrade process, including known problems like INT-269 (duplicate saved password IDs) and INT-290 (app presence in indexer bundle). Collaborate closely with the development and quality assurance teams to understand the root causes of these issues.
- Historical Whois Lookups: Implement historical Whois lookup functionality within the system, allowing users access to past domain ownership information. This feature will enhance investigations by providing historical context to domain data.
- DNSDB Pivotable Data: Integrate DNSDB pivotable data into the system, enabling users to pivot from domain information to related DNS data. This helps in tracing domain-related activities and identifying potential threats more effectively.
- Iris Detect Alerts: Develop the capability to create Iris Detect alerts directly within the system. Users can define alerting conditions based on DomainTools data, enhancing their ability to detect and respond to potential security incidents promptly.
- Dashboard Creation: Develop comprehensive usage dashboards that provide real-time insights into various aspects of API usage. Dashboards should include metrics such as data retrieval rates, query performance, logging details, and query counts.
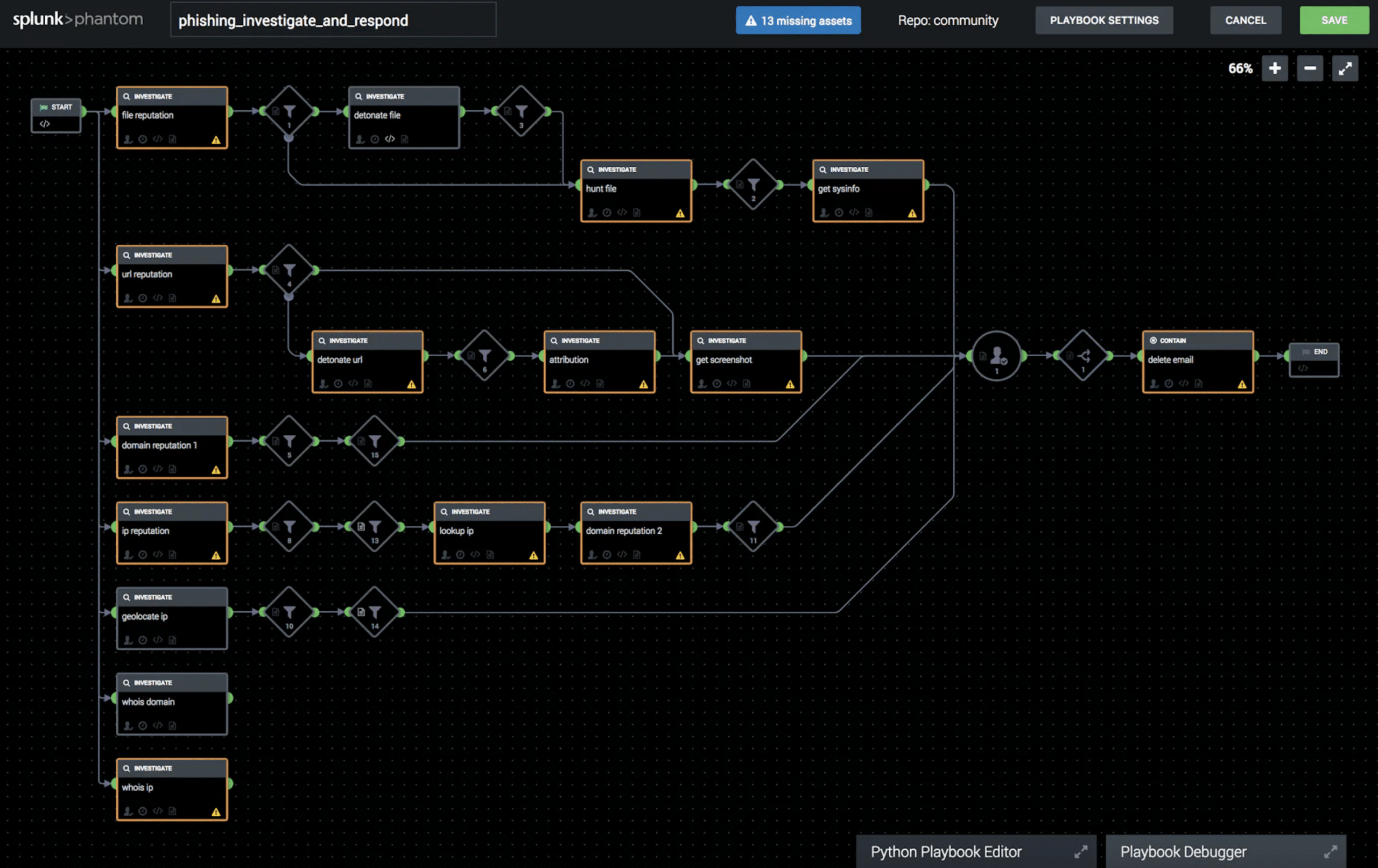
Splunk SOAR v1.5.1
Utilizing the power of DomainTools Threat Intelligence and data can be a great way to identify new and high-risk domains in Splunk and Splunk ES, but threat teams can take these capabilities a step further and automate response to malicious domains in Splunk SOAR.
- Test Connectivity: Validate the asset configuration for connectivity.
- Domain Reputation: Evaluate the risk of a given domain.
- Pivot Action: Find domains connected by any supported Iris Investigate search parameter.
- Reverse Domain: Extract IPs from a single domain response for further pivoting.
- Reverse IP: Find domains with web hosting IP, NS IP, or MX IP.
- Load Hash: Load or monitor Iris Investigate search results by Iris Investigate export hash.
- Reverse Email: Find domains with email in Whois, DNS SOA, or SSL certificate
- Lookup Domain: Get all Iris Investigate data for a domain using the Iris Investigate API endpoint (required).
- Enrich Domain: Get all Iris Investigate data for a domain except counts using the high volume Iris Enrich API endpoint (if provisioned).
- Configure Scheduled Playbooks: Run on initial setup to configure the optional monitoring playbooks. This action creates a custom list to manage the playbook scheduling and run status.
- On Poll: Execute scheduled playbooks based on the set interval(mins) in ‘domaintools_scheduled_playbooks’ custom list. Smaller intervals will result in more accurate schedules.
Splunk .conf 2024
These updates come at an exciting time as our team gets ready to head to Las Vegas for Splunk .conf next week. We’re not the only ones releasing some great feature updates; the team at Splunk will showcase several new updates to the platform as a whole, which is certain to enhance the experience of our DomainTools customers using the Splunk platform. There will also be some incredibly impactful sessions to look out for discussing the overall threat landscape and the hard work teams are doing to stop cybercrime in its tracks. Here are the sessions we’re most excited about:
AI, Financial Services and the Future of Financial Crime – Wednesday June 12 | 2-3pm PDT| Lido 3001B
There are so many use cases for Splunk in the financial services industry. The finance sector is among the highest-profile targets for cybercrime, intellectual property theft, extortion, fraud, and espionage. Splunk is making this sector a priority with a discussion led by Field CTO, Matt Swann, and Senior Vice President for Detection & Encryption for Global Payments Inc. Mickey Copeland. This session will focus on fostering collaboration between security, fraud, risk, IT, and engineering teams in the face of rising financial crime.
Be the Hacker and the Defender: Threat Simulation and Detection Engineering with Splunk | Thursday June 13 | 3:30 – 5:30 pm PDT | Marcello 4404
For experienced Splunk users, this advanced session will offer an interactive workshop that explores real scenarios through Splunk Attack Range. This platform will allow users to simulate attacks from the perspective of the hacker and then respond in the role of the defender. This session has limited attendees and won’t be recorded so get there early!
Blazing Fast Machine Learning Enabled Deep IoC Hunting with Splunk® Enterprise Security, Machine Learning Toolkit and SOAR | 11 – 11:45 am PDT | Marcello 4501
We love Splunk ES and Splunk SOAR, so it should be no surprise that this session caught our eye. But this talk serves as an incredible opportunity for those new to Splunk Security platforms to learn first hand how to recognize and act on Indicators of Compromise across a massive scale. This session will feature 2023 Splunkie award winner and L.A.M.E Creations (log analysis made easy) content creator, Troy Moore.
See More of Splunk SOAR and See Splunk SIEM 5 Live
If you’re attending Splunk .conf next week and interested in learning more about how we can we highly encourage you to stop by our booth #501 or schedule a conversation with our team to see these new features in action. And we realize attending shows like .conf means your pets are left at home, so when you book a brief meeting with us, you and your pet will receive matching t-shirts.







