DT Investigations - Security Research for the Community
Share this entry
Hello DTI Friends!
I should start by introducing myself, as that’s how all the best relationships start (or so I’m told).
If we haven’t yet had the opportunity to meet, I’m Daniel Schwalbe, CISO and Head of Investigations at DomainTools. I’ve spent the greater part of two decades tracking cybercriminals and nation-state actors in higher education, government, and large enterprises. I’m very passionate about sharing actionable insights with the community, which is what brings me to your feed today.
We launched DomainTools Investigations (DTI) on January 9 to turn our philosophy of supporting the community into reality. It’s a program with a coterie of researchers and analysts focussed on providing their expertise in investigating, mitigating, and preventing Domain- and DNS-based attacks. The goal is to do so on an ongoing basis, and we’ve already covered a bunch of ground since that announcement!
Let’s catch up on what we’ve shared so far:
HOT OFF THE PRESSES
You heard it here first! We JUST published a report examining the illicit market for aged and verified accounts across social media, email, and advertising platforms which represent a persistent and evolving threat.
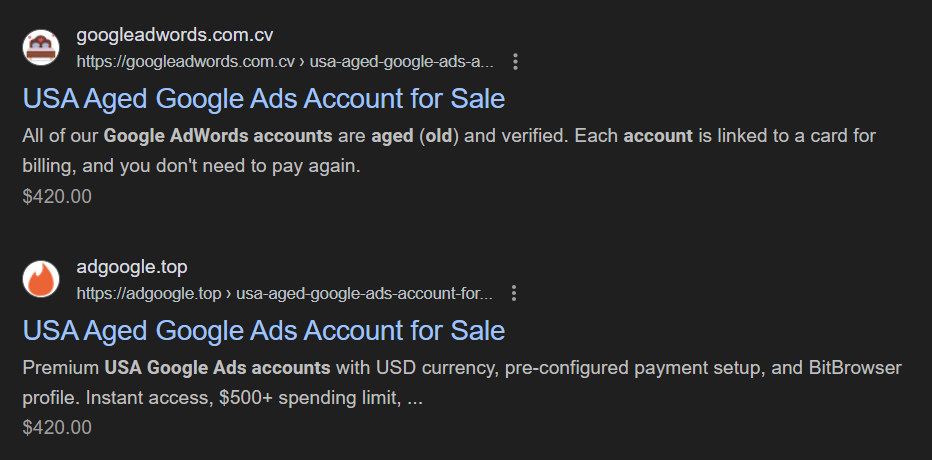
Why this is important: The activity highlights the urgent need for enhanced security measures, proactive threat intelligence, and increased awareness to combat the acquisition and exploitation of these compromised accounts.
Get the full scoop and IOCs here.
Where There’s One RAT, There’s A Nest
We recently shared details on Chinese malware delivery sites – hundreds of newly registered domains are actively targeting Chinese-speaking users with malware. Our report analyzes this activity, detailing the range of deceptive lures employed, including imitations of messengers, browsers, VPNs, email services, and Adobe software.
Why this is important: We’ve identified the involved malware families to include Gh0stRAT, ValleyRAT, RemKos RAT, LummaStealer, RedLine and others. As I’m sure you’re aware, understanding the patterns of these malware families can help practitioners develop more effective defenses.
Find the full write-up and list of IOCs here.
Cyber Criminals Playing the Long Game
Just prior to the announcement of DTI, we shared an overview on the Cyberhaven breach. In late December 2024, the technology company reported an unnamed actor replaced its Google Chrome extension on the Google Chrome Web Store with a malicious version.
The actor used a phishing email to compromise a developer’s account via authorizing a malicious third-party application. Our team reviewed publicly available information related to this incident and discovered that the Cyberhaven incident is part of a months-long campaign likely attempting to impact multiple companies primarily in the technology sector.
Why this is important: DTI looked at the IOCs shared by Cyberhaven and discovered a larger network of infrastructure likely used in similar attacks against other targets in the tech sector which is critical to share with others in our field so they may have the opportunity to prevent end users’ sensitive data from being compromised.
Find the full write-up and list of IOCs here.
[Secret Squirrel]
Our team periodically hosts Closed Door Sessions where we partner with other industry analysts and practitioners to share TLP:RED research. The next session will be in Seattle, WA on Wednesday, February 26.
You can request an invite here.
And not that you need any incentive other than super cool cutting edge research, but we’ve had pretty awesome t-shirts to give away at these sessions – You cannot get them anywhere else, must be present to wear. Seriously. They are fantastic conversation starters if you like having that attention.

Where We’ve Been/Where We’ll Be
My team has done (and will do) some traveling to various conferences. If you were lucky enough to get a ticket to the very last ShmooCon – I’m super jealous of you! If you couldn’t make it, be sure to catch Kali Fencl’s presentation – I’m Not Your Enemy: How Practitioners Can Empower Content, all about how practitioners’ training marketers can create content that’s beneficial to our audience and not at all “fluffy.”
And Malachi Walker will be presenting at the BIC Winter Conference on Friday, February 7 in Reston, VA. If you’re in the Beltway, I hope you can check out his session on how DNS Threat Intelligence could help you get your next promotion.
Final Thoughts
We’re very excited to share this research with you. I know some of you are probably still thinking “what’s the catch?” Many of us work for organizations with the main purpose of making money, so we get easily jaded when we read announcements that seem too good to be true. I’m making it my personal challenge to pleasantly surprise you, and I am expecting you to call me on it if we ever miss the mark. Check out my philosophy for DTI here. Maybe listen to Ben Folds’ Philosophy in the background while you read it.
If you found these excerpts and/or the full write-ups helpful, please forward it on to other folks you think would find it useful too – we’d greatly appreciate it!
This newsletter will be a monthly occurrence, so be sure to subscribe on LinkedIn to get early access to the newsletter content!
Thanks for reading – until next month!
Daniel