DomainTools 101: I found this creepy domain, now what?
Part 1 of a series of blog posts to help you be more effective in your investigations
One of the many things criminals will do is buy up or register domains that have been allowed to expire. Many times companies will close shop and allow the domains they owned to expire. In these instances, nefarious individuals will pick up those domains and re-register them. This is mostly done so that they can benefit from the goodwill of the company that let them expire.
Here’s a great report from SpiderLabs that covers an example of such techniques used to spread malvertising. In the article, SpiderLabs does a great job of showing how a threat actor was able to take over ownership of the expired domain, and to use that domain to begin spreading malware via a malvertising campaign.
What More Can I Learn from DomainTools Whois History?
From Whois History, you’ll be able to discover changes in ownership, the exact date a domain went behind privacy protection, and changes in resources used by the domain. For example, you can find that this domain was allowed to expire and was then picked up by a new actor. Using DomainTools Iris, you can also leverage the details (i.e. name servers, MX servers, IP address, Google Analytics code etc.) to pivot out and find other connected infrastructure and domains. This allows you to find all of the connected domains and infrastructure used by an actor.
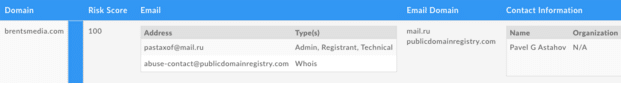
Doing Reverse Whois inside of Iris From the domain mentioned in the report we can find that brentsmedia[.]com is registered currently by pastaxof[@]mail[.]ru. When you pivot out on this email, you uncover other domains registered with that email address.
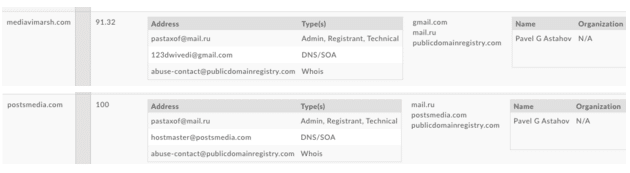
- Mediavimarsh[.]com
- Postsmedia[.]com
Of the three domains registered to this actor, we learn that two of the domains have a Risk Score of 100, meaning that they are already on an existing industry list of bad domains, and it’s clear this guy is up to no good. More about this in my next post.
One of those domains also has another email address that is revealed as part of the DNS records. 123dwivedi[@]gmail[.]com that allows us to pivot out to yet another domain sanjaydwivedi[.]com
But the point of Iris is not to go down as many rabbit holes as possible, although that can be fun if you have the time. Most SOC and IR professionals don’t have time on their side. This is why the speed at which Iris can uncover connected resources is so valuable, allowing security teams to take action on the full actor footprint more quickly and effectively. Down the road Iris will have built-in enrichment functions, making your work even more efficient.
In our next post of this series, you’ll learn how to use DomainTools Iris to get ahead of the criminals by discovering all of the domains owned by them and proactively blocking them from accessing your network, more about risk score/reputation engine, and other interesting pivots to uncover badness.




