DomainTools 101: Simple Strategies to Tackle Phishing in Your Organization
The other day I ran across a great blog post by Execute Malware that talked about the efforts he went through to find and identify new phishing domains. The one thing he didn’t mention was that he was mostly looking for free tools. I have to admit, the amount of detail and work he went through to find these newly created domains was significant. One of my favorite quotes from the post is “The next step is still tedious but it’s more interesting.” There is no question that this type of data is more interesting and critical to any investigation; however, there are techniques to help enable quick wins and ensure the process is no longer grossly tedious.
This blog post highlights techniques that provide quick wins when looking for this same data to surface critical information with either DomainTools Iris, or by using our API calls to automate this process. There are several examples of threat actors leveraging well-known brands for phishing expeditions, in this blog we will dive into PayPal.
To set up an efficient hunt with the objective of surfacing phishing domains, I simply started by searching PayPal in DomainTools Iris. Next, I removed domains registered legitimately by PayPal (by filtering out domains registered by @paypal.com email addresses). I also wanted to focus on recent domain registrations, so I narrowed my search to domains registered since 09-01-2016. This search returned a list of 24 domains.
One of the 24 domains uncovered in the simple search above was one domain that was extra intriguing: (paypal-money-adder[.]com) was registered by Tulasirao Lanke under the email blog.dannyy[@]gmail[.]com. This email is another critical piece of information that is searchable in Iris. In fact, 6 other domains were registered under this particular email address. Drilling down even further, we notice that these domains use two distinct registrant names: Tulasirao Lanke and Blog Dannyy. Searching for “Blog Danny” uncovers an additional 169 domains and another email address (tulasiraolanke[@]gmail[.]com), which in turn leads to another 190 domains. As you can see, it is simple to take one small data point and discover a multitude of malicious or risky domains.
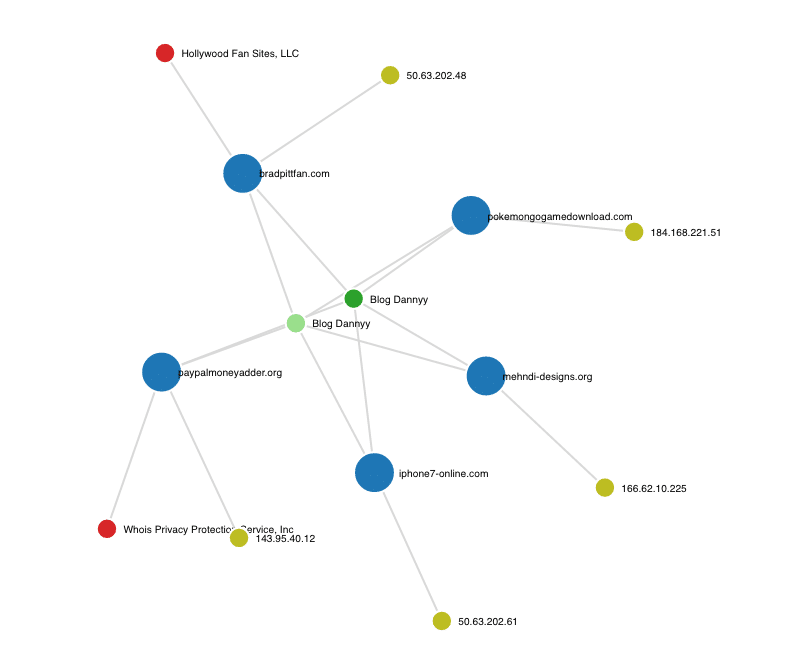
The takeaway here is your ability to quickly and accurately search for domains that might be used to phish your employees, or domains that were set up to spoof your domains for spear phishing attacks on your company. You can then export those results into a CSV file to be added to your blocked domain list that will be ingested by your DNS server or firewall. With our API, you could also create a quick call that would feed these same results directly into your firewall or DNS server and blocked.
Taking the next steps to get ahead of threat actors
At DomainTools we like to talk about being able to see threats coming and get ahead of threat actors. One of the ways you’re able to do that is by quickly performing investigations like these, and using the results set to proactively block those domains. I can now identify the email addresses used to register these domains and get alerts via email or API call when the actor registers new domains, and also proactively monitor the Name Servers they are using, and the IP addresses used for any changes.
This is where the power of DomainTools Iris really begins to emerge.
If you are interested in learning more about techniques for thwarting phishing and ransomware, join us for our upcoming webinar “Turn the Tide on Phishing and Ransomware”

Good luck while you’re hunting for phishing domains.




