Coming up this week on Breaking Badness. Today we discuss: Adding Spool to the PrintNightmare Fire, No More SynAcks, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Adding Spool to the PrintNightmare Fire
- The Print Spooler is a Windows service that runs by default on all Windows machines. It’s what handles, well, spooling to the printer of course. Anyways, it does all of that printer management for attached and network printers. Because it does networked printers as well it listens and works with the network stack. This makes it possible to hit the service remotely which means attackers can exploit issues with the service. In the case of PrintNightmare this was a remote code execution flaw that was found, so attackers could run anything they wanted on a machine running the print spooler. Since printing is required for most businesses it wasn’t something Microsoft could just ask people to disable—even though they did—and their first set of patches didn’t fix the issue. I think in total now there have been 7 or so major bugs found in the spooler over the last month since people started paying attention.
- There is yet another Windows 10 print spooler bug. This one with functional exploit code in the wild. Though that’s becoming the case for all of the spooler bugs being found. Along with new bugs being found due to the incomplete updates earlier in July.
- This latest bug is an issue with whenever printers get added or deleted. What vulnerability researchers do is they’ll look for elevated file access privileges—so in this case when a user makes a change the spooler service runs something as administrator. If they can find a bug there, then have the spooler service run their own code with elevated privileges, they can run their code as administrator and it’s game over for that system. That’s exactly what happened here and why Microsoft has mitigated this by making it so by default user level accounts cannot add or remove printers anymore. This is an interesting precedent since normally Microsoft refuses to do these kinds of legacy, default changes, like for instance how security researchers have been asking them to disable XLM Macros, the macros used by 1990s Excel documents, by default for years.
- A researcher named Victor Mata, from Accenture, who luckily must not have to deal with their latest ransomware IR, found the bugs and reported them last December. Print Spooler bugs are rolling into Microsoft though as researchers have turned their eye on their service.
- I think it was BlackMatter, the new ransomware variant and affiliate program, that has been seen already exploiting the bugs. A full RCE with proof of concept code in the wild is a big concern and it’s only a matter of time before it’s leveraged by actors and tooling.
No More SynAcks
- One of the things SynAck they’re known for is not being known for a whole lot. They actually haven’t been one of the more active groups out there. Maybe it’s because their branding sucked? They must have hired some consultant who told them so. Anyway, they didn’t make a lot of waves on their own, and then they moved to the always-chic affiliate model, where they got more criminals involved in….not doing a whole lot.
- In July they decided to go with this new name that tested really well in their focus groups and abandon the SynAck branding. So they closed this chapter of their sordid little existence and moved into the brave world of “El_Cometa.”
- I think their consultant must have run the numbers and figured out that there aren’t enough outstanding ransom demands or something, or else they were going to be too busy ordering new branded trade show swag to get around to collecting ransoms that victims were trying to pay? Who knows? So they decided to just hand over the decryption keys, which they did, to the folks over at the Record (a good infosec news site run by Recorded Future).
- We have definitely seen a number of ransomware gangs hand out decryption keys previously, and in those cases as now, it basically coincided with a rebranding. So some examples of this are various groups a lot of listeners will have heard of, including Avaddon, TeslaCrypt, Crysis, AES-NI, Shade, FilesLocker, Ziggy, and FonixLocker, according to bleepingcomputer.
- The keys that SynAck/El_Cometa released do indeed appear to be authentic and viable, as confirmed by researcher Michael Gillespie, aka demonslay335. He tested and verified. The folks at The Record, who received the keys, are not going to just hand them out as-is, though, because without some technical help, some users might mis-implement them and actually make things worse. Instead, Emisoft is creating a utility which they’ll make available when it’s ready.
- It’s hard to say what this will mean for the RaaS and ransomware industry in the grand scheme of things. I don’t see anything especially innovative or more worrisome than ransomware already is, in these actions. El_Cometa is going to try to recruit more affiliates – in their SynAck days they only worked with two (was that because of their inferior branding?). So it’s just basically another day, another corporate rebranding for an outfit that may or may not ultimately be a big player.
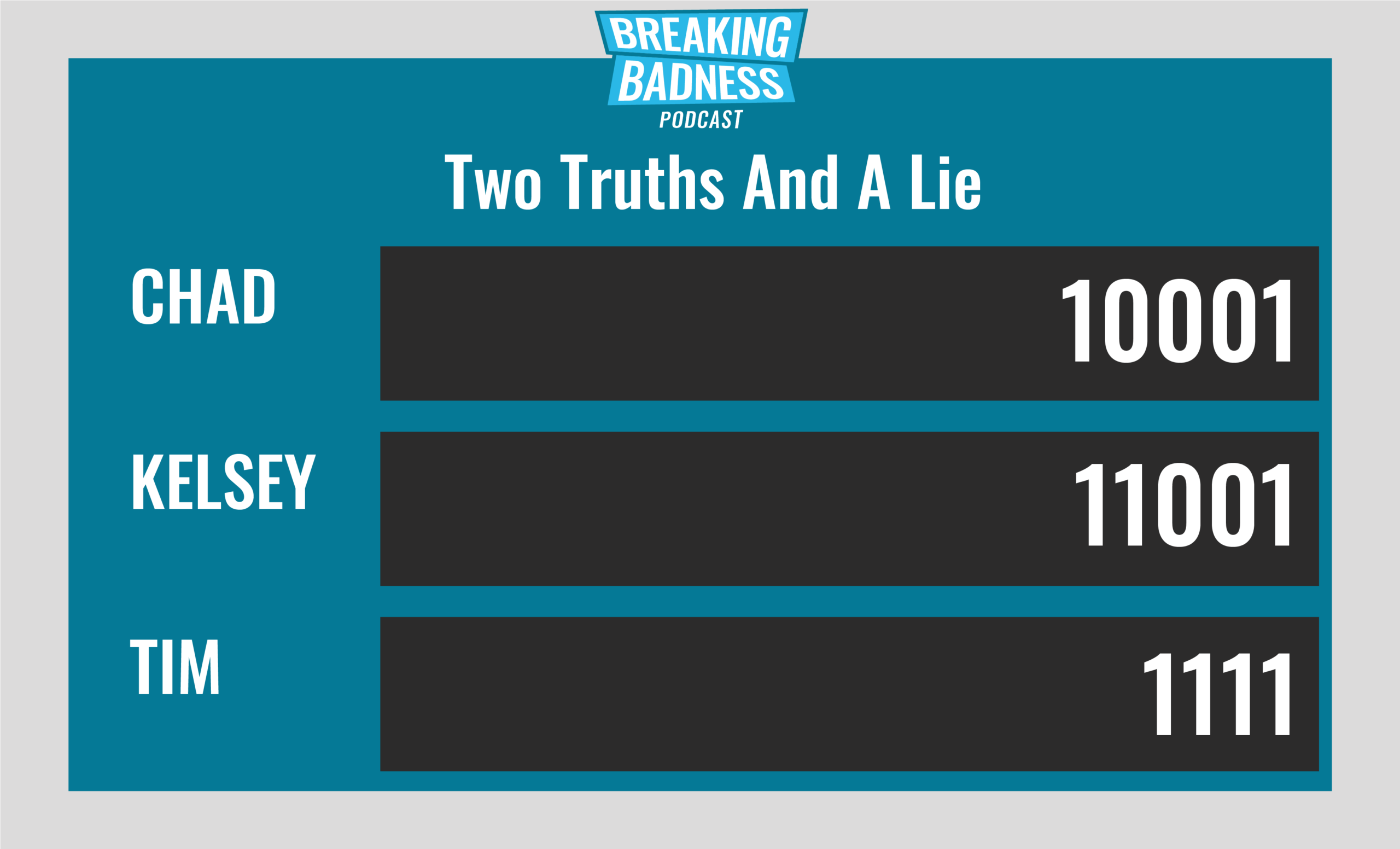
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Adding Spool to the PrintNightmare Fire
[Chad]: 8/10 Hoodies
[Tim]: 9/10 Hoodies
No More SynAcks
[Chad]: 3/10 Hoodies
[Tim]: 3/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!