Coming up this week on Breaking Badness. Today we discuss: An Annual ICS Report to Cut the Gordian OT, The Conti and the Restless, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
An Annual ICS Report to Cut the Gordian OT
- This past week, Dragos released their fifth annual edition of their ICS/OT report (looking back at 2021).
- Taking a step back to address some acronyms for those who are unfamiliar, ICS is Industrial Control Systems, and OT is Operational technology.
- Both terms refer to the network-connected control systems for physical facilities (power generation and distribution, utilities such as water and sewer, manufacturing plants, and more).
- That network is the OT environment.
- If you’re in Infosec, but haven’t worked in an ICS/OT environment, there’s an impulse to believe if the OT environment is air-gapped, everything should be fine, but that’s not the reality and it has nothing to do with the competency of folks running these facilities
- The reality is that there are places where there has to be some permeability in the boundary between the IT and OT environments, which we know can lead to problems, but it’s reality.
- To give a brief history of Dragos — Dragos is a sort of iconic company in the ICS security space. Its CEO, Robert M. Lee is known to most in this business, and for good reason.
- The team at Dragos has a deeper understanding of these control systems than sometimes manufacturers themselves do, and that goes a long way toward being able to make recommendations on how to secure them.
- What you see in this report is the output of their researchers, who focus on things like what vulnerabilities are being exploited.
- They also develop intel on actor groups, with a naming scheme derived from special alloys used in industrial manufacturing, so you see names like KOSTOVITE and KAMACITE.
- Some of the events highlighted in the timeline featured in the report (in no particular order) include the ones most people know about such as the Colonial Pipeline and JBS Foods ransomware events.
- The Oldsmar municipal water system breach is another folks may recall.
- There are notable others that are a little less well-known, such as a breach of Honeywell, which as many folks know is a significant manufacturer in the ICS space.
- Dragos has also tracked a number of new activities from existing actor groups as well as a few new ones.
- According to the report, some of the top challenges the ICS/OT industry needs to address include:
- The vulnerabilities in the ICS or OT space are a huge challenge, for a variety of reasons. There are many that don’t have patches available and when a patch is available, one of the things people may not realize is that in the OT world, you simply can’t apply the advice “patch early and often.” Applying patches in those environments can be VERY different from the IT world. A busted patch (and those can happen) can fully bring down an environment.
- Just shutting down systems to the patch is itself risky.
- There’s also the challenge of visibility into these environments—there can be tens or hundreds of thousands of devices, and some of them are in remote locations with extremely limited connectivity.
- There are a lot of OT environments that have connections to the IT side of the house, or directly to the Internet, so that’s a big challenge too.
- This report also covers security controls that are most effective for enhancing ICS/OT networks against threats (this part of the report will sound more familiar to those whose time is mainly or exclusively spent in IT rather than OT):
- Network segmentation.
- Strong authentication and security around remote access.
- Good password practices.
- Improved monitoring and asset viability.
- Practical management of vulnerabilities and patching.
- In terms of the impact this report will see for 2022 with the invasion of Ukraine, it’s hard to guess at this point.
- We saw less overt cyber warfare-type activity at the beginning of the invasion, and maybe that’s still true now (at the time of recording) than what people expected.
- Joe Slowik wrote a great analysis of this that is partly conjecture (which he acknowledges), but the essence of that was that the shifted timeline of the invasion (which came a few weeks later than a lot of intel assessments suggested) meant that some of the coordinated cyber+kinetic attacks that were expected were not able to be coordinated that way.
- There are a lot of potential events Russia could still launch, but is keeping in their back pocket for now.
- It’s also possible that their cyber capabilities are being mitigated and even degraded, possibly, by groups like the Ukraine IT Army and even Anonymous and other groups.
- A huge amount of what you’ll find in this report is helpful, even if you’re not in the OT world.
- The recommendations as mentioned above are in many ways applicable to those in IT.
- We will say we did find some of the stats around vulnerabilities a bit surprising (some of it in a good way).
- The percentage of vulnerabilities that don’t have any practical mitigation has gone down in the past two years. It was 76% in 2019, 64% in 2020, and 19% in 2021).
- It was also surprising to see the percentage of vulnerabilities that Dragos assessed as less severe than the public advisory was 97%.
- We know that while there are absolutely threats that are serious, there are also many ways in which we are less vulnerable than some of the hand-waving suggests.
- Last week, CISA (Cybersecurity and Infrastructure Security Agency) updated their alert on Conti ransomware to include IoCs used in malicious operations.
- Exciting news for CISA in the past week:
- Outside of this update, CISA received a significant funding boost ($2.6B) from 2021.
- In addition to that, there is legislation being passed for more mandatory reporting over breaches.
- This update comes from an ongoing report from CISA first published in September 2021 that is continually updated, with the most recent update coming this week regarding 98 domains owned and operated by the Conti ransomware gang.
- The original content featured in this alert from September 2021 began when an internal Conti ‘playbook” was made public by an angry affiliate.
- We discussed Conti last week in the context of the leaked chat logs, but to better understand/contextualize the IoCs (indicators of compromise) CISA shared in this alert, we believe it’s helpful to take more of a look at the behavioral indicators (e.g. with whom do people register their domains) including passive DNS from our friends at Farsight.
- In terms of patterns regarding the 98 domains in question, they do seem AI-generated on some level, but they are not complete gibberish and there are no numbers involved. They do appear to look like words.
- The initial reaction one might have to these 98 domain names is to block them, though they aren’t active and they’ve been exposed for fraud already.
- Organizations can use this list to build context clues for future questionable domains.
- As a note, CISA did not link all these domains to Conti — they indicated that they appear like they could be Conti.
- You could argue they have to be tied to Conti based on patterns and behaviors.
- Alerts such as these are always helpful for actionable threat intel as it’s better to have this information than not.
- This information can provide context clues from a behavioral perspective to understand what steps to take in the future.
- It’s also helpful to understand how this information intersects with your network.
The Conti and the Restless
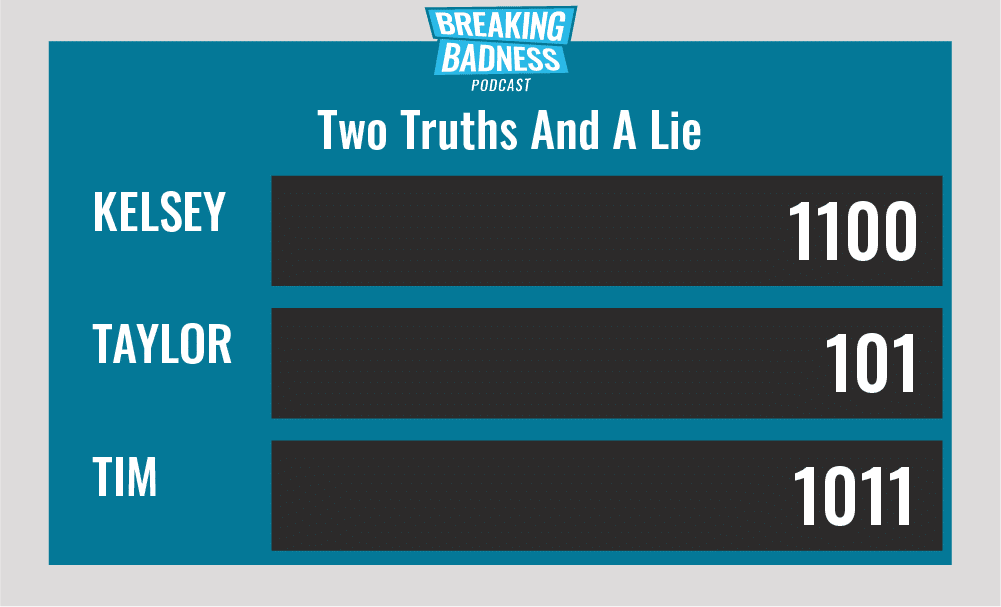
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
An Annual ICS Report to Cut the Gordian OT
[Taylor]: 4/10 Hoodies
[Tim]: 4/10 Hoodies
The Conti and the Restless
[Taylor]: 5/10 Goodies
[Tim]: 6.5/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!