Insights Into the Twitter Bitcoin Scam
On July 15th, 2020, several verified, high-profile cryptocurrency Twitter accounts were being leveraged to send users to a phishing site. Subsequently, multiple high-profile verified users – including Bill Gates, Elon Musk, and Barack Obama – were compromised and began posting tweets calling for money to be sent to a bitcoin wallet address (bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh) and double would be sent back in turn. All in all, over $100,000 was sent to the address mentioned in one of the most successful of these types of scams. Later, cybersecurity firm RiskIQ released a list of almost 400 domains that through on-page similarities they tied to the phishing domain originally mentioned. Between those domains and the original tweets, the DomainTools Security Research Team used both the Iris Investigate platform and OSINT sources to gain insights into the infrastructure, trends, and financials behind these scams.
Follow the History
The earliest domains in this data set were registered in 2018. Many of the domains cluster around specific email addresses, TLS certificates, and other registration details. With the spread of hosting providers, registrars, and infrastructure fingerprints behind all of these domains we can say with high confidence that the domains in this data set belong to multiple sets of scams and likely multiple actors.
Expanding on historical email addresses associated with these domain’s registration data, we can expand the list to just under 600 domains and clusters begin to appear.
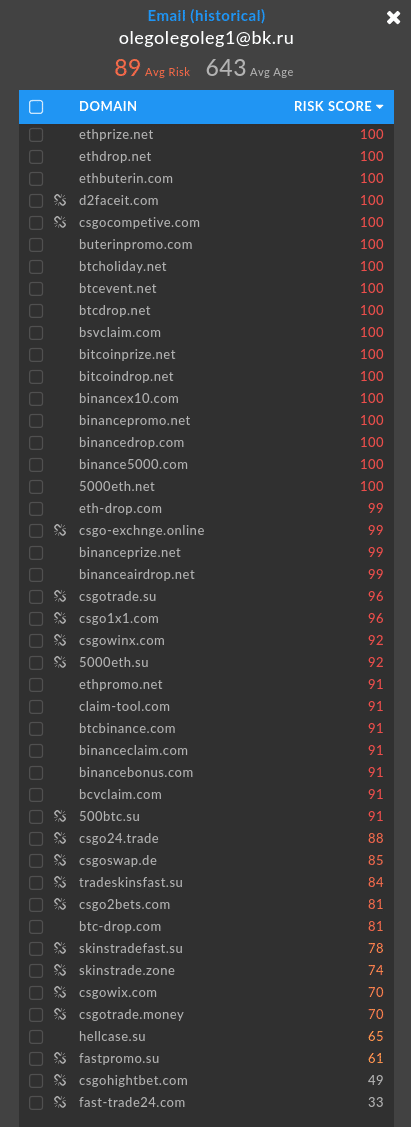
One early cluster tied to an email address (olegolegoleg1@bk[.]ru) crops up older CS:GO (a popular FPS game) container key resale scams which Valve, the company behind CS:GO, disabled in 2019 as the majority of the traffic they were seeing was to launder money through the game.
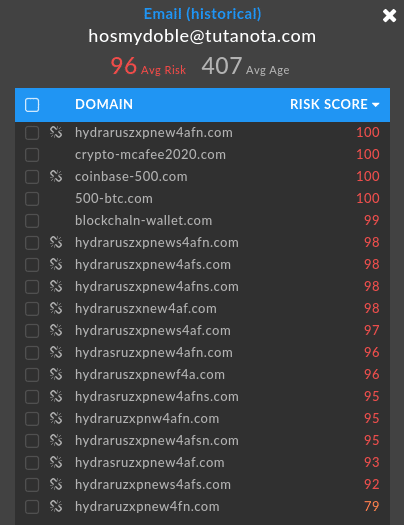
Another cluster ties the actor behind it to several known blocklisted phishing domains that have gone offline in 2019.
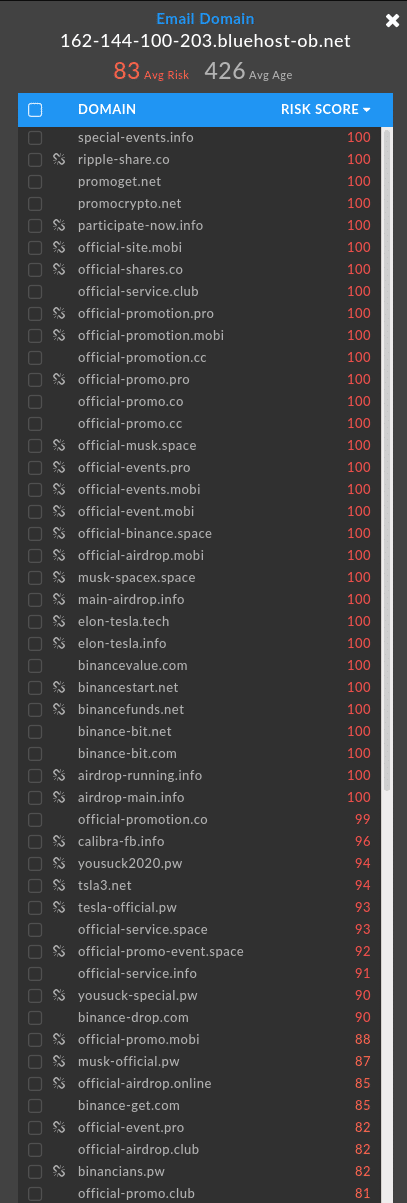
While yet another cluster links back 82 domains to almost two years of these exact kinds of bitcoin scams leveraging Elon Musk and Tesla lures.
With the prevalence and ease of these scams it comes as no surprise that there are dozens of clusterings of likely independent actors and a history of these low-hanging fruit scams targeting cryptocurrency.
Follow the Naming Patterns
After running the list of domain names released by RiskIQ through a probabilistic-based word splitter, we can figure out what words were used most by the people that registered these domains. Below is the list of words from the dataset, sorted by their frequency of use.
| Coinbase | 58 |
| Btc | 57 |
| Binance | 43 |
| Give | 29 |
| Promo | 28 |
| Gates | 28 |
| Mcafee | 27 |
| Elon Must | 25 |
| Linux | 21 |
| Crypto | 20 |
| Coin(s) | 18 |
| Must | 16 |
| Drop(s) | 15 |
| Space | 12 |
| Pro | 11 |
| Bit | 10 |
| Bonus | 10 |
| Event | 10 |
| Gift | 10 |
| Bill | 9 |
| Giveaway | 9 |
| Tesla | 9 |
| Eth | 7 |
| Christmas | 6 |
| Free | 6 |
| XRP | 6 |
| Gemini | 5 |
| Participate | 5 |
| 5 | |
| Airdrop | 4 |
| Apple | 4 |
| April | 4 |
| Bezos | 4 |
| Get | 4 |
| Gives | 4 |
| Join | 4 |
| Present | 4 |
| Prize | 4 |
| Promotion | 4 |
| Woz | 3 |
| Bch | 3 |
| Help | 3 |
| Now | 3 |
| Prob | 3 |
| Bin | 2 |
| Brad | 2 |
| Campaign | 2 |
| Comp | 2 |
| Deals | 2 |
| Extravaganz | 2 |
| A | 2 |
| Force | 2 |
| Funds | 2 |
| Giving | 2 |
| Live | 2 |
| Market | 2 |
| Robert | 2 |
| Start | 2 |
| Super | 2 |
| Today | 2 |
| Token | 2 |
| Top | 2 |
| Walmart | 2 |
| Win | 2 |
| Xmas | 2 |
When looking across this list there are terms that are obviously related to each other
- Apple related: airdrop (4), woz (3), apple (4)
- Bill Gates: bill (9), gates (28)
- Elon Musk: elon (25), musk (16), tesla (9), space (12), x (17)
I decided to pick one of the more popular, but less obvious words to investigate deeper; mcafee which occurred 27 times. The theory is that people who register multiple domains based on a single term will use some of the same registration/infrastructure patterns.
Mcafee domain patterns
Most of the mcafee domains are registered anonymously through “regprivate.ru” or “reg.ru”
Many domains that are not registered via a russian registrar, have russian sounding names: Vyach Kapustin, Igor Smirnov, John Vladimir (found 5 domains from John)
One registrant, Masis069 Arutunyan, links to the domain binance-cryptovaganza.org, which isn’t part of the mcafee set of domains. But the naming pattern is similar to other domains in the RiskIQ dataset; “binance” occurring 52 times and “ganza” occurring 4 times. So including all “ganza” domains into the list of “mcafee” domains.
Using the registrant Masis069 Arutunyan, and the terms “mcafee” and “ganza” to expand the list of domains, another name surfaced; “John Vladimir”, which is associated with 3 domains in the RiskIQ dataset.
Another strong pattern among the mcafee domains is the registrar Hostinger. Looking back at the full list of RiskIQ domains, the majority of them that were registered by Hostinger were registered around 260 and 360 days ago.
13 of the 27 mcafee domains have their own mail server configured.
This investigation into the mcafee domains pulled together around 40 domains from the RiskIQ dataset that were highly related to each other.
I then dove into the “elon musk” related domains and was able to find a group of domains that were highly related to each other as well. But what was interesting is that the mcafee domain set had no connections to the registration or infrastructure patterns of the elon musk domains.
Follow the Money
Diving into the known associated Bitcoin wallet addresses associated with the Twitter compromise, let’s establish a baseline for our investigation.
| Wallet Address | Number of Transactions | Total Balance |
|---|---|---|
| 38qyALcxSnfzaFFTnt46xHMTN3GCGanKXC | 0 | 0 |
| Bc1q0kznuxzk6d82e27p7gplwl68zkv40swyy4d24x | 15 | $1,622.60 |
| Bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh | 390 | $117,200.70 |
Investigating on the Bitcoin wallet with the most transactions (390) and with the total received balance being over $117K USD, let’s dig into any interesting transactions that have occurred. Walletexplorer.com helps us highlight these wallet transactions, specifically with observing how much Bitcoin was transferred, when it was transferred and to which wallets.
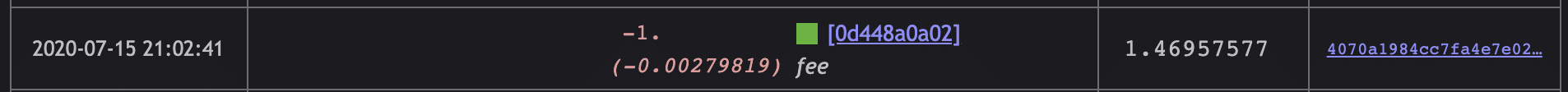
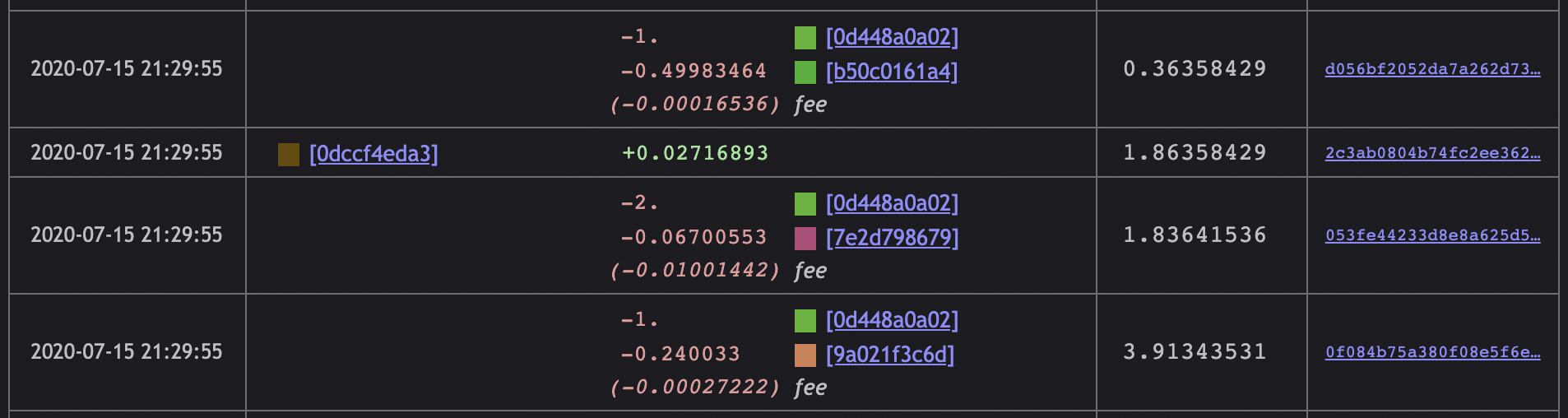
We can see a total of 4 transactions of Bitcoin transfer for multiple values to multiple wallets.
The timestamps for these transfers all occur within the same window of time, generally, July 15th 2020 21:02 to July 15th 2020 21:29. That’s about 17 minutes.
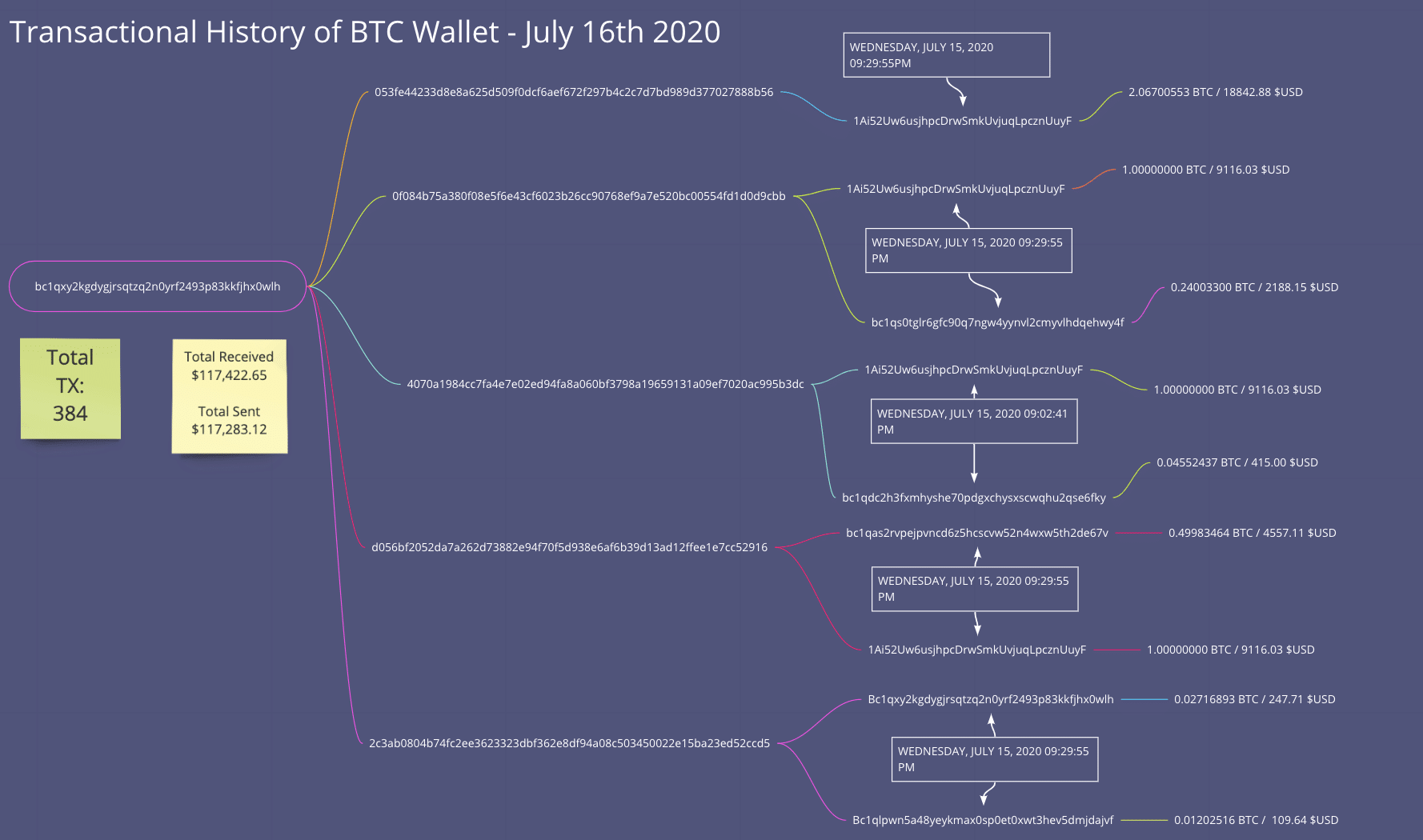
One possible theory behind the transactions is that they are paying off those involved with the incident from an attacker’s perspective. This attack was likely not conducted by a single individual. There could have been an initial threat group that compromised Twitter and then sold the access off to another bidder who leveraged that access to conduct the cryptocurrency scam. There are theories that an insider threat was involved in providing internal access to systems/tools to the attackers, and this could be a possible documentation of the payments received for that to happen. Cybercriminals are rarely just a single threat actor, and there are several running theories behind this attack.
| Associated TX Bitcoin Wallets to Bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh |
|---|
| 1Ai52Uw6usjhpcDrwSmkUvjuqLpcznUuyF |
| bc1qs0tglr6gfc90q7ngw4yynvl2cmyvlhdqehwy4f |
| bc1qdc2h3fxmhyshe70pdgxchysxscwqhu2qse6fky |
| bc1qas2rvpejpvncd6z5hcscvw52n4wxw5th2de67v |
| 3ChjurNXe6eJrgvF3Hz4Hw4rEgSRkkCeN5 |
| 32xPzGc8FRFdfbVj4ocFAEhe7dPkn8r5sA |
| 3BoE6NhfyWXZAZWtihDe8s7bHHKHMQHWM3 |
| bc1q8ahum0gzw7dqmtyyy63fdqkhd8aynyllpuxhcz |
| 3DA2babKUhP74pKitfzoXaoFNnpH38TqWQ |
The money is moving pretty fast, and we can see that in some high value transfers from the originating wallet to other associated wallets all associated with the threat group behind the Twitter attack.
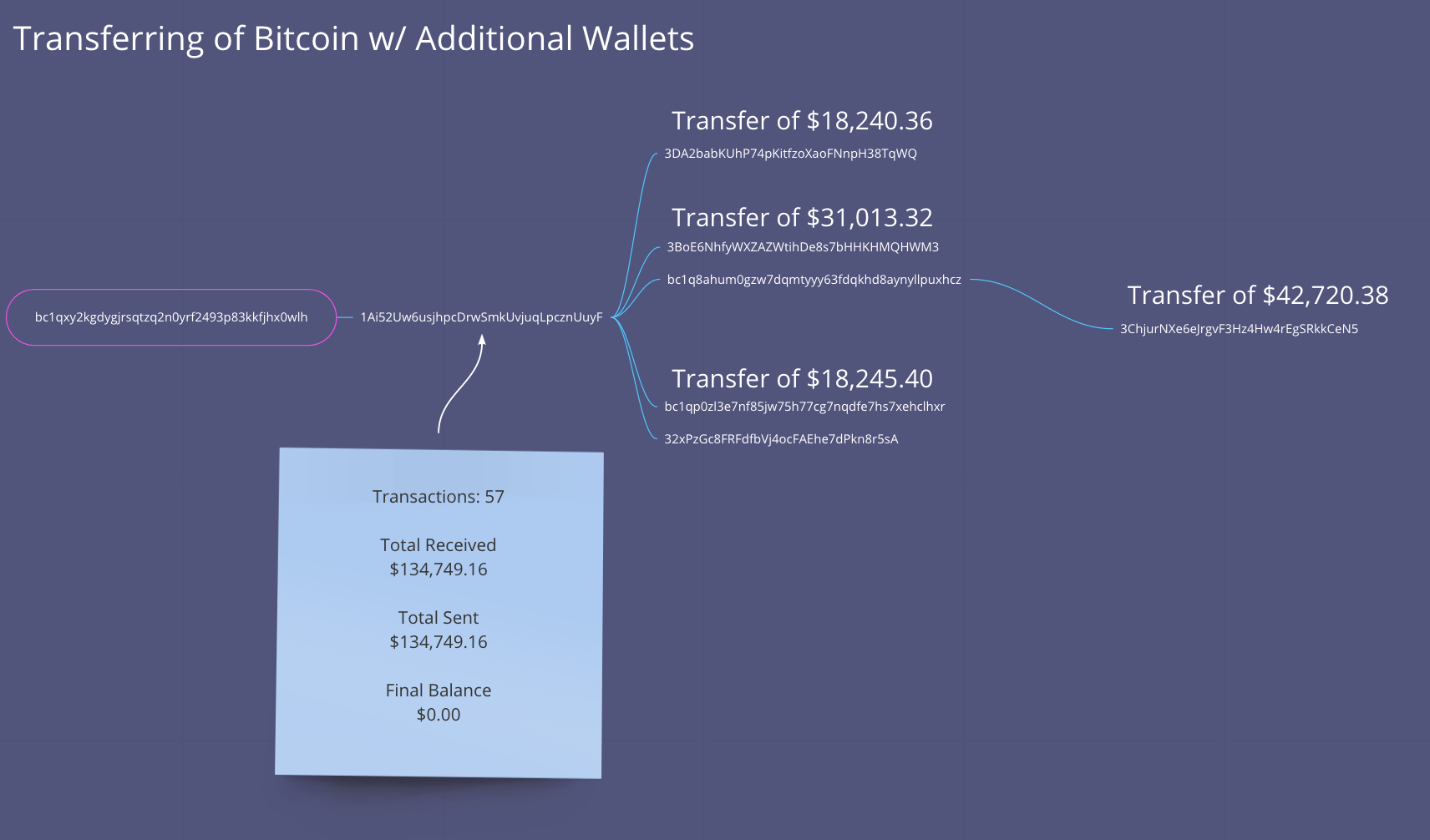
We have uncovered several additional IOCs and insights into this prolific attack against Twitter and its users. Stay tuned for further information as we uncover it.