SEATTLE, May 3, 2017 /PRNewswire/ — DomainTools, the leader in domain name and DNS-based cyber threat intelligence, today released the names of the top U.S.-based retail companies whose brands are frequently abused by criminals creating look-alike domains for phishing. The research surfaced multiple malicious domains each day spoofing Amazon, Apple, Gap, Nike, and Walmart.
Hackers have become adept at creating websites and emails that closely resemble the actual brand, tricking consumers into thinking they are on a legitimate website or receiving a message from their preferred retailer. One of the more popular ways to generate phishing domains is to add certain words (called affixes) like “account,” “login,” “online,” or countless others to the domain names of legitimate organizations, in order to make the victims believe they are either visiting the legitimate site or receiving a trusted email. Victims then often submit sensitive information, such as passwords and credit card numbers, to these websites. For example, it has been reported that a phishing email led to the stolen personal and financial data of more than 110 million Target shoppers.
“Top brands such as Amazon and Apple are typically targeted because of the amount of traffic going to those sites. In addition, they are highly reputable companies, making it easier for consumers to fall victim. Using PhishEye, we are able to identify the look-alike domains that are spoofing these top brands on the day that they are created,” said Kyle Wilhoit, senior security researcher at DomainTools. “A brand with this information could block the spoofed domain and investigate the perpetrator behind it – potentially saving millions of dollars. The more we profile this malicious behavior, the better we can defend against it.”
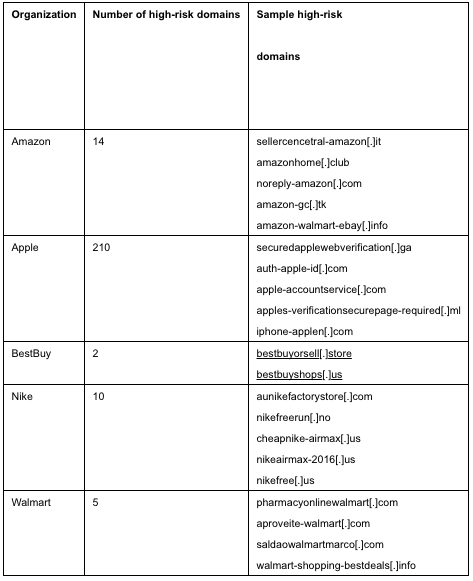
A snapshot of a PhishEye report shows how many high-risk domains (domains who scored 70 or higher according to DomainTools’ reputation score) were created between March 27-31, 2017 to spoof well-known online retailers. High-risk domains are defined as either already on a commercially-available blocklist or having a strong correlation to known blocklisted domains.
To review the full PhishEye report, and to review tips on how consumers and organizations can protect themselves, visit: http://blog.domaintools.com/2017/05/up-to-your-gills-in-phishing-attacks-this-research-may-help..
About DomainTools
DomainTools helps security analysts turn threat data into threat intelligence. We take indicators from your network, including domains and IPs, and connect them with nearly every active domain on the Internet. Those connections inform risk assessments, help profile attackers, guide online fraud investigations, and map cyber activity to attacker infrastructure. Fortune 1000 companies, global government agencies, and leading security solution vendors use the DomainTools platform as a critical ingredient in their threat investigation and mitigation work. Learn more about how to connect the dots on malicious activity at https://www.domaintools.com or follow us on Twitter:@domaintools
