A Website Attacked
Share this entry
The following is a non-exhaustive investigation into a so-called “watering hole attack” on a U.S.-based apartment’s public facing website to deliver malware by spoofing a fake browser update. The investigation led to the identification of dozens of other compromised websites from health care providers, retail, hobbyist and other consumer websites.
Compromised websites were modified to load malicious scripts from external domains. Some scripts were found to utilize browser profilers to customize delivery and spoof content for Chrome, Mozilla, and Edge browser updates to deliver NetSupport malware, with examples provided below.
Starting Off
An apartment website was compromised and configured to load an iframe, an HTML element that was used to load another website into the currently displayed website, from an external domain. In this case, the iframe was used to load in a malicious website that was spoofed as a fake browser update.

The iframe loads index.php file from an external website uniquetouniquetechnicalservices[.]com , which contains code to spoof as a Chrome Update downloader, a common malware delivery technique.

<a href="blob:https[:]//uniquetouniquetechnicalservices[.]com/9b9eb4f1-46d8- 4985-8631-a40c174ff875" id="button" download="Update.js">Update Chrome</a>
Filename: Update.js
Sha256: 3a8592a08dbed49906e60b66747901fa530d435d1296f8e849097e69ebe026cc
Update.js drops several files including
Filename: CXCC.zip
Sha256 f4c80753adb721e3b55febeda133f9604e31ed19e234dca63be005e4bf2199a6
Looking For More
An additional domain resolves to the IP address and over 30 other similarly named files have been observed communicating to the IP
alberta-sl[.]com
route.alberta-sl[.]com

Several similar files and associated infrastructure could be linked to what appears to be a multi-year campaign of phishing and water-hole related malware delivery.
A similar executable that reaches out to “north-residence[.]com”, attempts to download and run NetSupport RAT and connect to 5.181.159.137 .
Looking for other recent samples associated to sha256:
18df68d1581c11130c139fa52abb74dfd098a9af698a250645d6a4a65efcbf2d
http://5[.]181[.]159[.]137:443/fakeurl[.]htm
http://5[.]181[.]156[.]60/fakeurl[.]htm
http://173[.]44[.]141[.]66/fakeurl[.]htm
http://dcnvahedforil31[.]com:3121
http://94[.]158[.]245[.]103/fakeurl[.]htm
https://estafetaofj[.]top/data[.]php?14979
http://5[.]181[.]159[.]28/fakeurl[.]htm
https://gxsicmj3l[.]top/cdn-vs/download[.]php?4372
http://94[.]158[.]245[.]103/fakeurl[.]htm
http://lilygovert91[.]top/data[.]php?6889
https://roadrunnersell[.]com/trade/fix[.]php?789
http://5[.]181[.]159[.]28:443/fakeurl[.]htm
https://gxsicmj3l[.]top/cdn-vs/download[.]php?4372
...
Expanding Scope
Commonalities in the domain registrations and presumably injected code into compromised websites are recorded by internet scanners. This allows for looking for websites that may be similarly compromised and employed to distribute the fake updater malware.
Example query:
http.html:"cdn-vs/original.js"
Sample Finding:

External domains serving fake updater malware:
ganharcomblog[.]com
theaeroescorts[.]com
Sample 2:

External domains serving fake updater malware:
ganharcomblog[.]com
Sample 3:

External domains serving fake updater malware:
chefspavilion[.]com
Sample 4:

External domains serving fake updater malware:
elbied[.]com
Pivoting From Similar Fake Update Files
Server Scan Data:
http.html:"linedloop[.]org"

Two suspicious URLs set as script sources
https://drilledgas[.]org/dpw79r1k
https://linedloop[.]org/HLgFVr7h
Server Scan Data:
http.html:"drilledgas.org"

Similar use of createElement script and multiple external URLs.
https://jsqur[.]com/LK2BnrDQ
https://drilledgas[.]org/dpw79r1k
https://dailytickyclock[.]org/Rz7kFbxJ
https://surelytheme[.]org/ZcqVjVQ1
https://greedyclowns[.]org/NTPm2fKs
https://quaryget[.]org/Gb7XTy3b
https://devqeury[.]org/PZyGWrXw
https://nowordshere[.]org/bjz1khVv
https://biggerfun[.]org/HQn5BKC3
https://bigbricks[.]org/cjpYRFns
https://greedyclowns[.]org/NTPm2fKs
https://lemonicecold[.]org/cd5fkZwv
https://climedballon[.]org/ytW8d9XY
https://jqueryh[.]org/7JHjvZgP
https://libertader[.]org/YMKhmHVC
https://lemonicecold[.]org/cd5fkZwv
https://neworderspath[.]org/k4WP6NP9
https://treegreeny[.]org/KDJnCSZn
https://waterlinesheet[.]org/bDrVdw9c
https://greenpapers[.]org/6gjyRhhQ
jsqur[.]com
drilledgas[.]org
dailytickyclock[.]org
surelytheme[.]org
greedyclowns[.]org
quaryget[.]org
devqeury[.]org
nowordshere[.]org
biggerfun[.]org
bigbricks[.]org
lemonicecold[.]org
climedballon[.]org
jqueryh[.]org
libertader[.]org
neworderspath[.]org
treegreeny[.]org
waterlinesheet[.]org
greenpapers[.]org
Attempts to place the external code into the website prior to loading
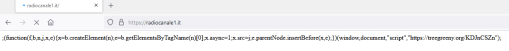
Over the course of the investigation, three methods for loading the malicious scripts into presumably compromised websites were identified.
- Use of iframes to load content from a malicious URL.
- Use of document createElement with a random variable string, which then sets its source from the malicious URLs.
- Use of a createElement and insertBefore to load the script from a malicious URL
Domain Registration Analysis
The actor utilized a range of domain registrars and VPS providers over the past year. Making regular changes. Volume and speed of operations appears to be prioritized over operational security for the actor.
- Registrars: RegRU, GoDaddy, NameCheap, Alibaba, Gname, Nicenic, Tucows, Dynadot
- ISP IPs: DigitalOcean, Trellian, Irako, CloudFlare, Servinga, Level 3, RegRu, Stark
- Nameservers: Cloudflare, AWS
alberta-sl.com
bigbricks.org
biggerfun.org
chefspavilion.com
climedballon.org
dailytickyclock.org
dcnvahedforil31.com
devqeury.org
drilledgas.org
estafetaofj.top
ganharcomblog.com
greedyclowns.org
greenpapers.org
gxsicmj3l.top
jqueryh.org
jsqur.com
lemonicecold.org
libertader.org
lilygovert91.top
mtpolice2030.com
neworderspath.org
north-residence.com
nowordshere.org
quaryget.org
roadrunnersell.com
robotprintmoney.com
service-f0.com
surelytheme.org
theaeroescorts.com
treegreeny.org
uniquetouniquetechnicalservices.com
waterlinesheet.org
Conclusion
Watering hole attacks take advantage of trusted, frequented websites to target users. The identified websites that were suspected to be compromised served a wide range of consumers in several countries in the U.S., Europe, Thailand, and Japan. The websites shared no particular configurations in common except that they were all likely owned or operated by small businesses or third parties. It is suspected the actor does not specifically target these small business sites but that they are more often not as well maintained, not able to support resilient security practices and are subsequently easier targets. For instance, nearly half of the suspected compromised websites used wordpress or plugins that may be vulnerable to exploitation.
Commonalities in malware use, the delivery methods and targeting suggest this activity may be associated with Socgholish.
Over the past several years, successful cyber attacks and data breaches have increased significantly year over year. The threat landscape continues to evolve and organizations and individuals alike must stay vigilant to protect themselves. With the prevalence of such widespread targeting ever on the rise, it takes a community to raise awareness and stay safe when using the internet such as alerting website owners and others to suspicious activity on websites.





