Automated Discovery of Chenlun Domains - Splunk Enterprise Security
Share this entry
TL;DR
This technical blog explores a next step in this investigation on Chenlun by automating Splunk searches to gather domains using DomainTools, and share them using Splunk’s trigger actions. By integrating DomainTools with Splunk, you can streamline the identification of malicious domains, stay ahead of attackers, and optimize your security resources.
Using Passive DNS to Discover Newly Created Domains
Learn how I leveraged the DomainTools app for Splunk to automatically query Farsight DNSDB to discover newly created domains matching Chenlun’s domain generation algorithm (DGA).
Why Automating the Search Process is Important
When a critical search yields valuable results that are subject to change over time, automating the search process becomes essential. This automation not only ensures timely updates but also significantly reduces the manual effort required.
Once scheduled, I used Splunk’s trigger actions to send the results via email to myself and other team members for us to know when new Chenlun domains are observed in DNS.
Background
In November of 2024, I wrote an article discussing new developments in phishing attacks attributed to Chenlun/Sinkinto01. DomainTools data allowed us to identify a preference of using subdomains with short life-cycles on older apex-level domains. Both subdomains and apex-level domains used indicate the use of a DGA as a method of obfuscation.
Using Passive DNS in Splunk to Uncover Subdomains
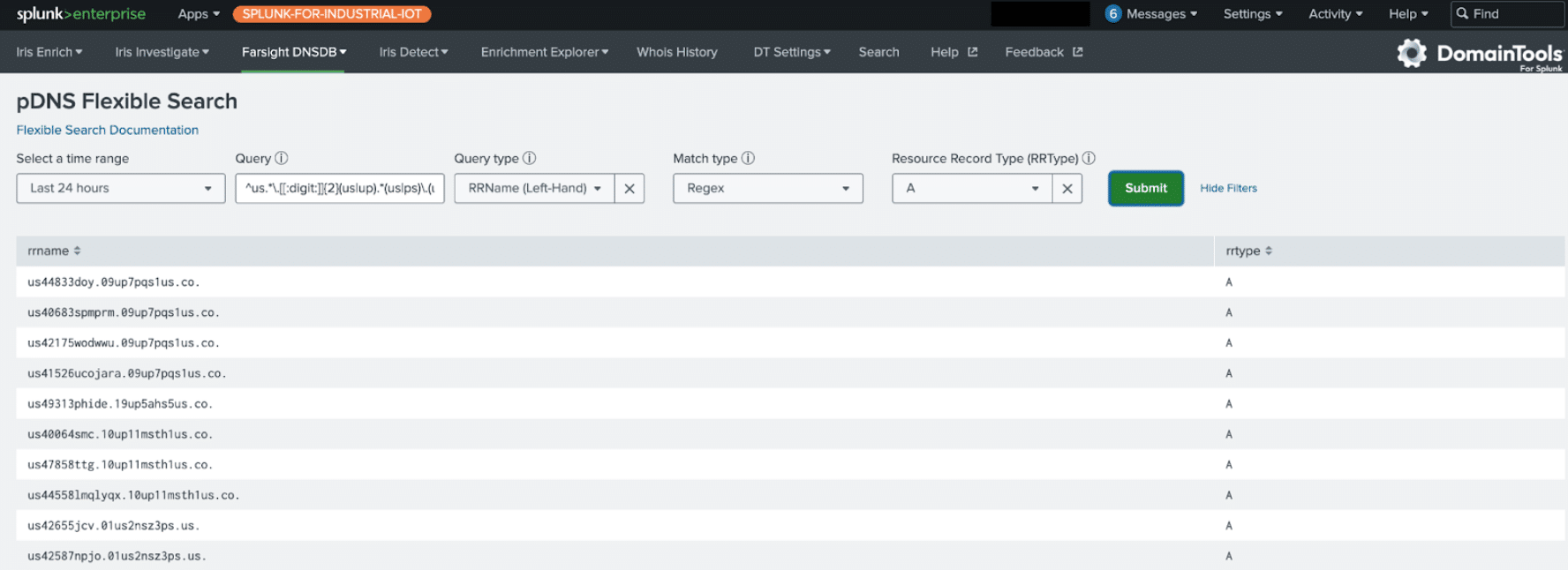
Using a regular expression to search for domains matching the identified patterns, I queried against our passive DNS database using the flexible search within our DomainTools app for Splunk and uncovered subdomains that were last observed in DNS within 24 hours from the time of the search. Below shows the output from regex pattern 1:
^us.*\.[[:digit:]]{2}(us|up).*(us|ps)\.(us|co)\.$
Splunk offers the ability to schedule a report based off of a search. In order to see the Splunk Processing Language (SPL) search equivalent of my query shown above I simply opened it up in search.

Clicking on “Open in Search” automatically showed me the SPL needed.

Saving this search as a report is key as it allows one to schedule it to run and gather fresh data from DNSDB’s passive DNS database at a regular interval.
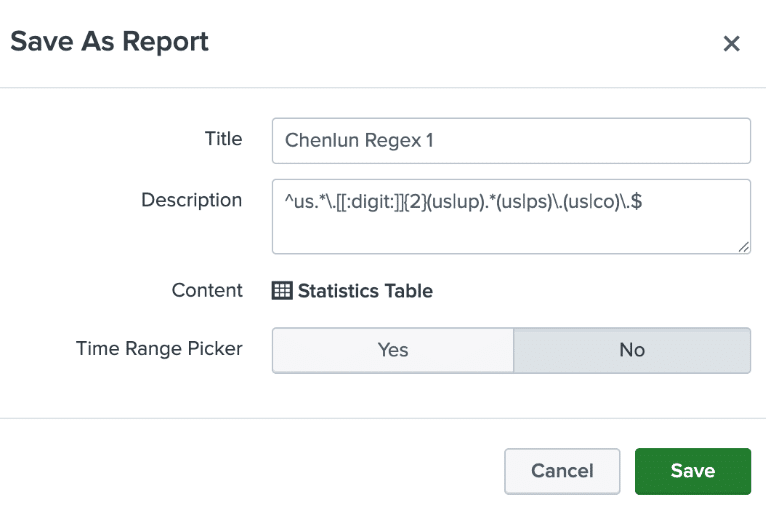
After saving the report, there is an option to schedule the report. I chose to have the search run every 8 hours as we have teams spread across different time zones across the globe.

Splunk offers the ability to add a trigger action to any scheduled report. Adding a trigger action is where one can determine what they’d like to do with the output from the results of the search. The image below shows the option of sending the results to email recipients with the option to include a CSV attachment of the results.

Other trigger actions include:
- Create a notable event for triaging in Enterprise Security
- Create an alert within an app like Slack using a webhook
- Run a specific Splunk SOAR playbook
- Execute a custom script
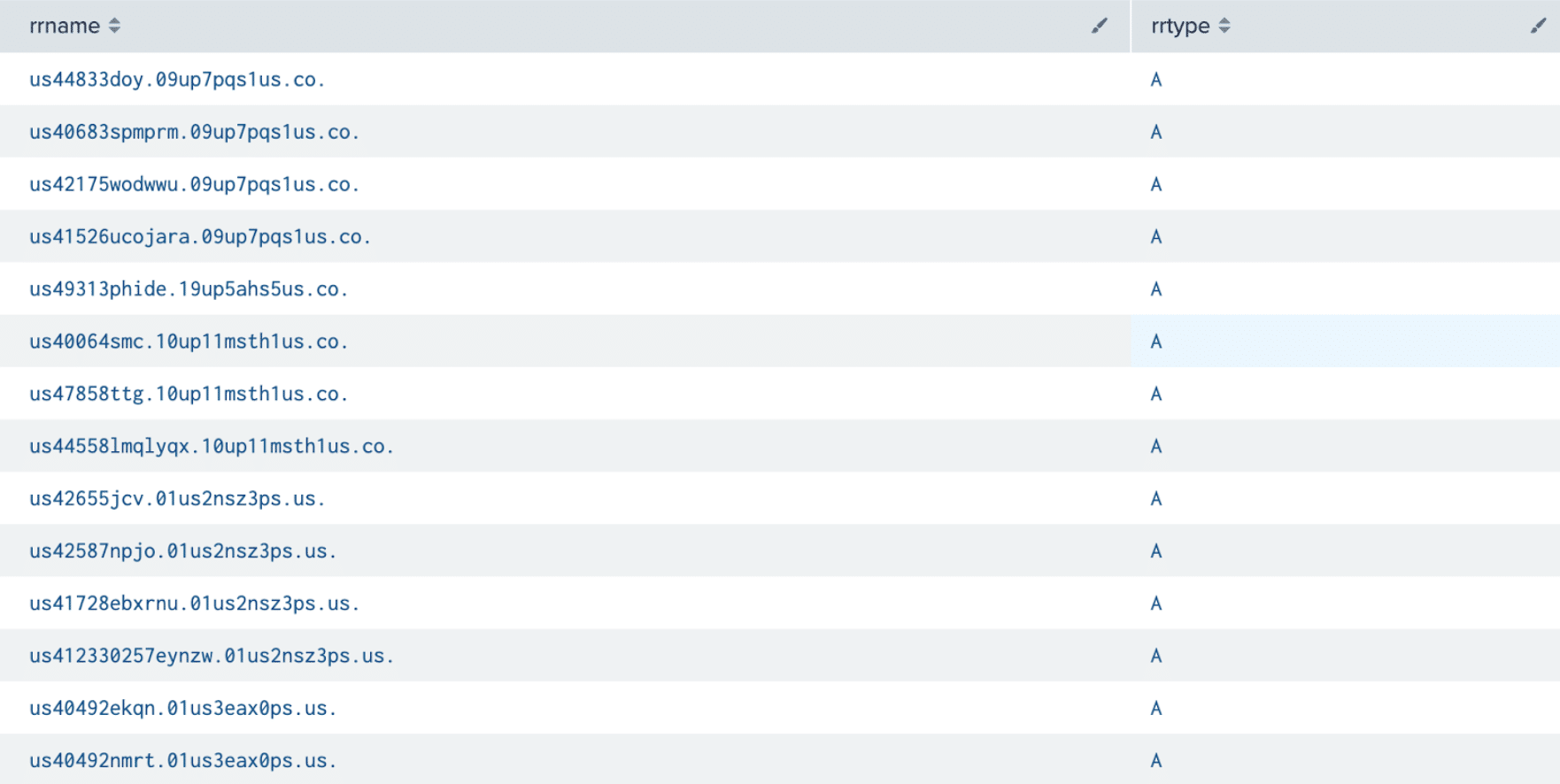
Now, every 8 hours, those added to the recipient list get an email including a CSV with the results from my DNSDB flexible search. Here is what the results would look like:
Conclusion
With the help of DomainTools DNSDB flexible search and Splunk’s scheduled reports, we now have a specific Chenlun domain intelligence feed allowing us to create alerts, inform investigations, and automate responses to certain threats.
Splunk’s capability of automating searches coupled with our domain-related data has also left me considering other use cases where this would be helpful such as:
- Discover domains using legitimate brands for phishing
- Discover domains matching a threat actor’s domain creation profile
- Discover domains being used in business email comprise campaigns
- Discover domains spoofing legitimate brands for credential harvesting
- Discover domains being used for malware distribution
The ability to create scheduled reports with this domain-related data allows one to stay ahead of emerging threats, automate security processes, and reduce the risk of bad outcomes.







