Current Events to Widespread Campaigns: Pivoting from Samples to Identify Activity
We would like to thank Black Lotus Labs at Lumen for their contributions and assistance in this analysis.
If you would prefer to listen to The DomainTools Research team discuss their analysis, it is featured in our recent episode of Breaking Badness, which is included at the bottom of this post.
Introduction
Cyber Threat Intelligence (CTI) practitioners can gain insight into adversary operations by tracking conflicts or geopolitical tensions. Similar to a “follow the money” approach in criminal investigations, looking at conflict zones can reveal cyber capabilities deployed as part of events —either by the parties to the conflict itself, or third parties interested in monitoring events for their own purposes.
The above theory is supported by historical incidents linked to geopolitical tensions:
- Russia’s invasion of Ukrainian territory leading to, among other events, the 2015 and 2016 Ukraine power incidents, the 2017 NotPetya event, and continuing operations to the present.
- Tensions in the Arabian/Persian Gulf region leading to multiple rounds of wiper malware as well as providing possible “cover” for the 2017 Triton/TRISIS incident.
- Continuing strains on the Korean peninsula providing cover for the 2018 disruptive attack on the Pyeongchang Olympic Games (even if the attacker in this case was not North Korea).
Based on precedent, analysts can identify developments in adversary operations and technical capabilities by tracking identifiers related to major events and conflict zones. Identifying capabilities deployed to take advantage of such items can yield insights into fundamental attacker tradecraft and behaviors, and enable defense and response for incidents which may strike far closer to home at a later date.
Initial Discovery: Caucasus Conflict
With the above thesis in mind, DomainTools researchers examined technical artifacts emerging around the 2020 conflict between Armenia and Azerbaijan in the Caucasus region. While investigating, researchers discovered the following malicious document file on a commercial multi-scanner service:
Name: PKK militants in Nagorno-Karabakh.doc MD5: e00af9b6303460666ae1b4bdeb9503ba SHA1: ce810173555d6a98ce10c847f16e95575fe13405 SHA256: 7c495c21c628d37ba2298e4a789ff677867521be27ec14d2cd9e9bf55160518f
Masquerading as a news article covering details about the Caucasus conflict, the document contains a reference to an external site to fetch additional material to the victim’s computer:

In this specific case, the document attempts to communicate to the domain “msofficeupdate[.]org”:
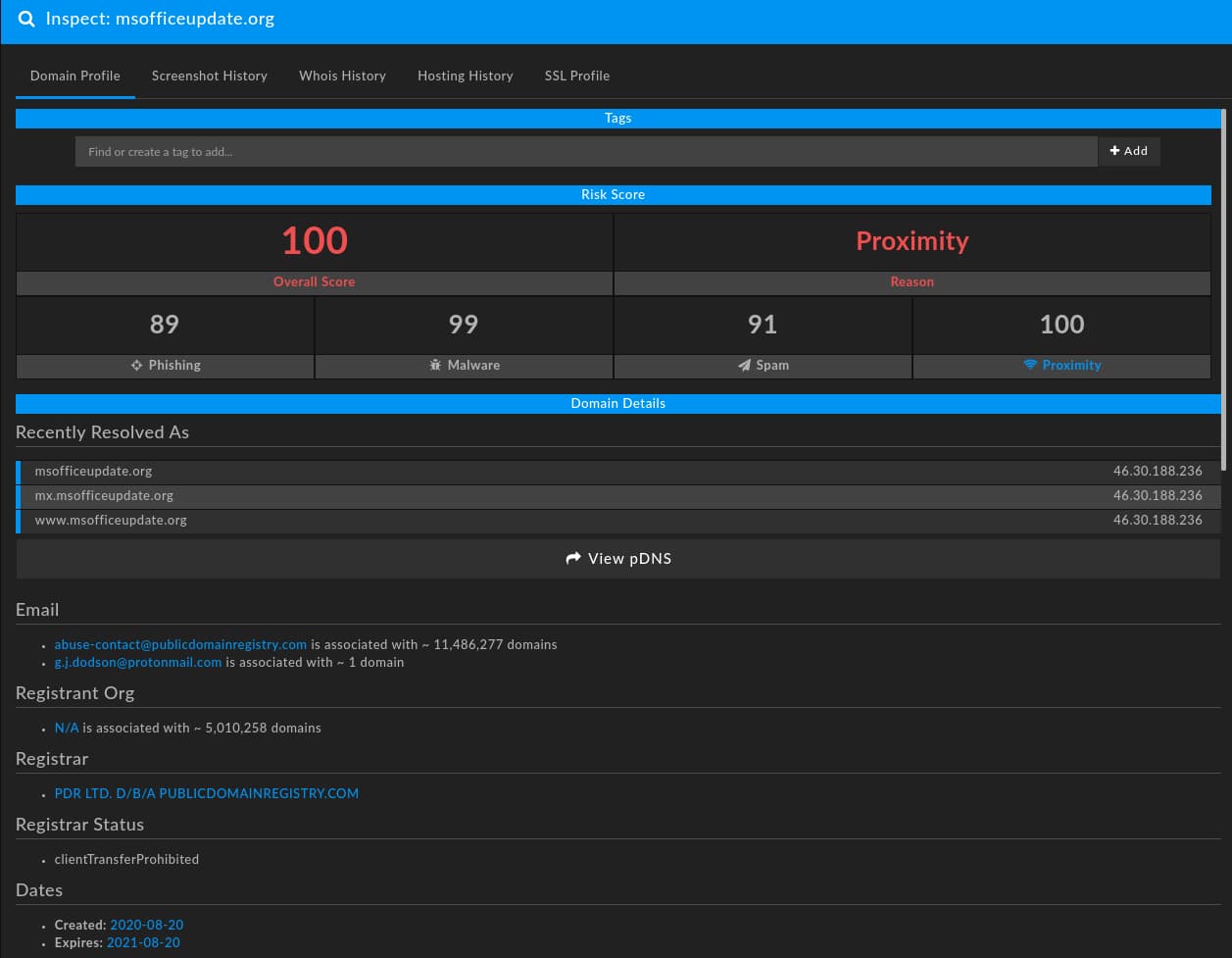
Overall, the document appears focused on the Armenian-Azerbaijani conflict with dedicated network infrastructure enabling the attack sequence. While we could stop and view this item in isolation, further analysis reveals even more interesting elements.
Identifying Items for Pivoting
Both the document and the domain contain items of interest for further analysis and pivoting. Reviewing lessons from a previous DomainTools blog, we can examine the technical indicators related to this campaign as composite objects with opportunities to discern fundamental adversary behaviors.
Examining the document, file metadata, shown here using Phil Harvey’s ExifTool, indicates the presence of an unusually long string of numbers as a template object:
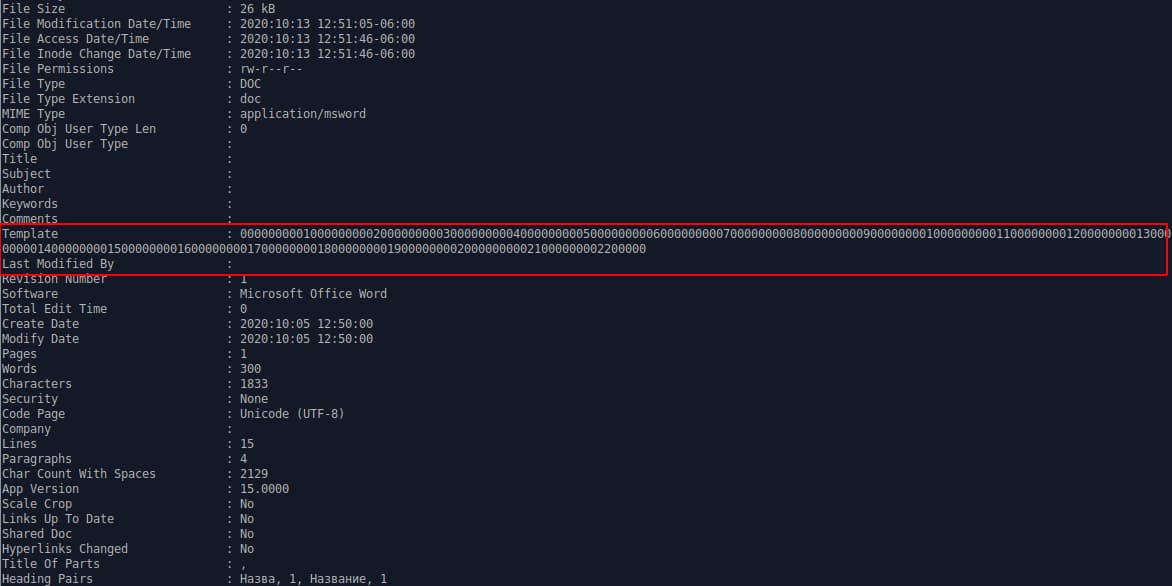
Based on the template object and a hard-coded Uniform Resource Locator (URL), the document will attempt to communicate to the domain identified above. The actual functionality of the malicious document hinges on network communication to the attacker domain, with an HTTP request to a resource such as the following:
hXXps://msofficeupdate[.]org/morgue6visible5bunny6culvert7ambo5nun1illuminate4
All following functionality appears dependent on a response to this request. At this time, DomainTools does not have any data or other information as to what may be returned from this response. As a result, our analysis is limited to the document itself and identified network infrastructure. However, defenders may find value in the URL pattern in the HTTP request—words divided by single numbers—for developing Network Intrusion Detection System (NIDS) signatures.
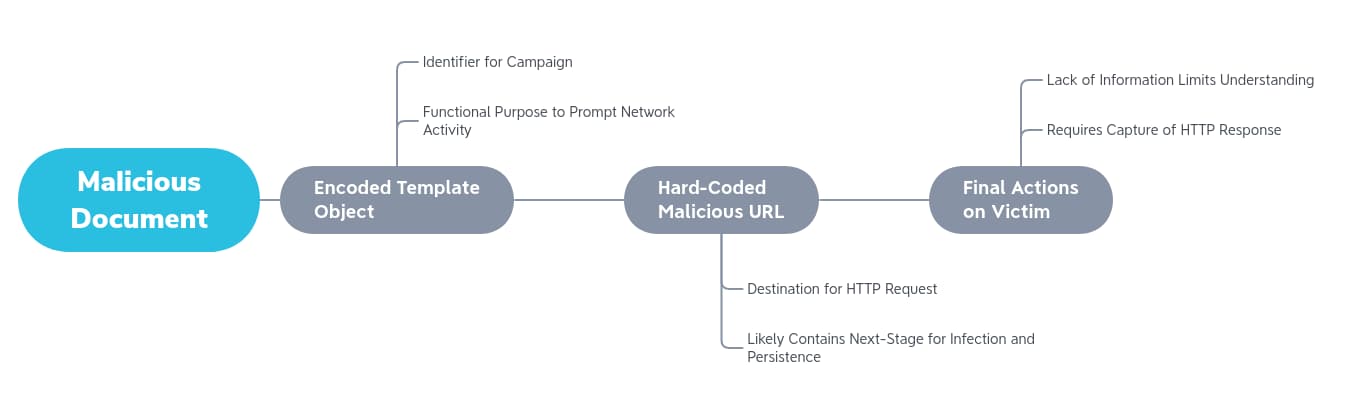
Lack of view into follow-on execution aside, we have a search string to use to fingerprint additional file samples or to disposition items that may be related to the original campaign in the template string. Notably, for a malicious document, the item does not contain any active content (ActiveX objects or Visual Basic for Applications [VBA] macros), limiting our ability to identify further items. However, the template item appears unique enough to serve as a signifier to identify additional samples similarly constructed.
On the infrastructure side, we have several more leads to follow. As previously documented in past blogs on infrastructure hunting and analysis, we have a combination of technical indicators related to domain creation and hosting as well as thematic identifiers related to the domain name itself. For the domain in question, as seen in the previous DomainTools Iris Investigate inspection image above, the following observations hold:
- Leaked registrant email, “g.j.dodson[AT]protonmail[.]com”.
- Domain registration service, “PDR Ltd. d/b/a PublicDomainRegistry.com”.
- Authoritative name server associated with the domain, “bitdomain[.]biz”.
- Hosting on a dedicated server, “46.30.188[.]236”, through the Netherlands-based provider “Web2objects Gmbh”.
- An SSL/TLS certificate obtained through Sectigo with limited identifying information.
- A domain “theme” of mimicking Microsoft Office update services.
While any of the above items in isolation may be relatively limited for identifying adversary tendencies or additional infrastructure—either by being too general or far too specific—in combination, they can yield patterns for further analysis. For example, looking for a combination of privacy-centric email addresses registering domains via PublicDomainRegistry using the name server “bitdomain[.]biz” hosted in Europe with Sectigo SSL/TLS certificates can yield a result set for further analysis. Applying a “thematic” search to the results of such an investigation, such as looking for other Microsoft or Office themes in domain names, can identify additional items for analysis related to this campaign.
Unraveling Additional Infrastructure
Based on the characteristics described in the previous section, DomainTools researchers identified 35 domains matching the patterns associated with the initially observed malicious domain at varying levels of estimative probability or confidence. As shown in the following table, we can observe additional tendencies such as favoring several privacy-oriented email services during registration and an overwhelming focus on European Virtual Private Server (VPS) providers for hosting purposes.
| Domain | Date Created | Registrant Email | IP Address | Hosting Provider | Hosting Location | Confidence |
|---|---|---|---|---|---|---|
| iphoneupdatecheck[.]com | 2016-05-12 | [email protected] | 91.236.116.166 | [email protected] | SE | Medium |
| brexitimpact[.]com | 2016-06-23 | [email protected] | 185.112.82.7 | Oy Creanova Hosting Solutions Ltd. | FI | Low |
| srv3-serveup-ads[.]net | 2019-04-16 | [email protected] | 101.100.209.236 | Vodien Internet Solutions Pte Ltd | SG | Low |
| newoffice-template[.]com | 2019-06-12 | [email protected] | 147.135.170.193 | OVH Hosting Inc. | FR | High |
| ms-check-new-update[.]com | 2019-07-08 | [email protected] | 87.121.98.51 | Tamatiya EOOD | BG | Medium |
| template-new[.]com | 2019-08-28 | N/A | 66.70.218.38 | OVH Hosting Inc. | FR | High |
| user-twitter[.]com | 2019-11-13 | [email protected] | N/A | N/A | N/A | Medium |
| live-media[.]org | 2019-11-27 | [email protected] | 137.74.181.109 | OVH SAS | FR | Medium |
| officeupgrade[.]org | 2019-11-29 | [email protected] | 198.24.134.13 | Secured Servers LLC | US | High |
| template-office[.]org | 2020-01-10 | [email protected] | 185.243.114.175 | Access2.it Group B.V. | DE | Medium |
| get-news-online[.]com | 2020-01-15 | [email protected] | N/A | N/A | N/A | Low |
| liveinfo[.]org | 2020-01-15 | [email protected] | 91.195.240.87 | Sedo GmbH | DE | Medium |
| newoffice-update[.]com | 2020-02-11 | [email protected] | 51.161.96.100 | OVH Hosting Inc. | CA | Medium |
| update-office[.]com | 2020-03-03 | [email protected] | 192.52.166.12 | CrownCloud US LLC | US | High |
| upgrade-office[.]com | 2020-03-18 | [email protected] | 158.69.30.205 | OVH Hosting Inc. | CA | High |
| tls-login[.]com | 2020-03-25 | [email protected] | 103.255.250.70 | EN Technologies Pte Ltd. | SG | High |
| upgrade-office[.]org | 2020-04-07 | [email protected] | 66.248.206.239 | Hostkey B.V. | NL | High |
| newupdate[.]org | 2020-06-04 | [email protected] | 46.183.221.141 | DataClub S.A. | LV | Medium |
| 2020-windows[.]com | 2020-06-19 | [email protected] | 176.107.181.128 | PE Freehost | UA | Low |
| petronas-me[.]com | 2020-07-05 | [email protected] | N/A | N/A | N/A | Low |
| msupdatecheck[.]com | 2020-07-10 | [email protected] | 167.114.44.150 | OVH Hosting Inc. | CA | High |
| log1inbox[.]com | 2020-08-15 | [email protected] | N/A | N/A | N/A | Medium |
| gmocloudhosting[.]com | 2020-08-17 | [email protected] | N/A | N/A | N/A | Low |
| msofficeupdate[.]org | 2020-08-20 | [email protected] | 46.30.188.236 | Web2Objects GmbH | GB | High |
| interior-gov[.]com | 2020-08-31 | [email protected] | N/A | N/A | N/A | Low |
| e-government-pk[.]com | 2020-09-04 | [email protected] | N/A | N/A | N/A | Low |
| e-govoffice[.]com | 2020-09-07 | [email protected] | N/A | N/A | N/A | Low |
| azureblog[.]info | 2020-09-25 | [email protected] | N/A | N/A | N/A | Low |
| rneil[.]ru | 2020-10-01 | [email protected] | N/A | N/A | N/A | Low |
| N/A | N/A | N/A | Low | |||
| weather-server[.]net | 2020-10-09 | [email protected] | N/A | N/A | N/A | Medium |
| doc-fid[.]com | 2020-10-21 | [email protected] | N/A | N/A | N/A | Low |
| rarnbler[.]com | 2020-11-09 | [email protected] | 80.78.22.11 | Cyberdyne | SE | Medium |
| msofficeupdate[.]com | 2020-11-10 | [email protected] | 185.25.51.24 | Informacines Sistemos IR Technologijos UAB | LT | High |
| netserviceupdater[.]com | 2020-11-11 | [email protected] | N/A | N/A | N/A | Medium |
| new-office[.]org | 2020-11-13 | [email protected] | 51.89.50.150 | OVH Hosting Inc. | FR | Medium |
While the majority of items were created in 2020, some potentially related network observables date as far back as 2016. When matched against malicious document samples examined in the following section, we begin to see the outlines of a persistent, somewhat lengthy campaign. Although extended in time, the same fundamental network behaviors are reflected in observed items throughout this period.
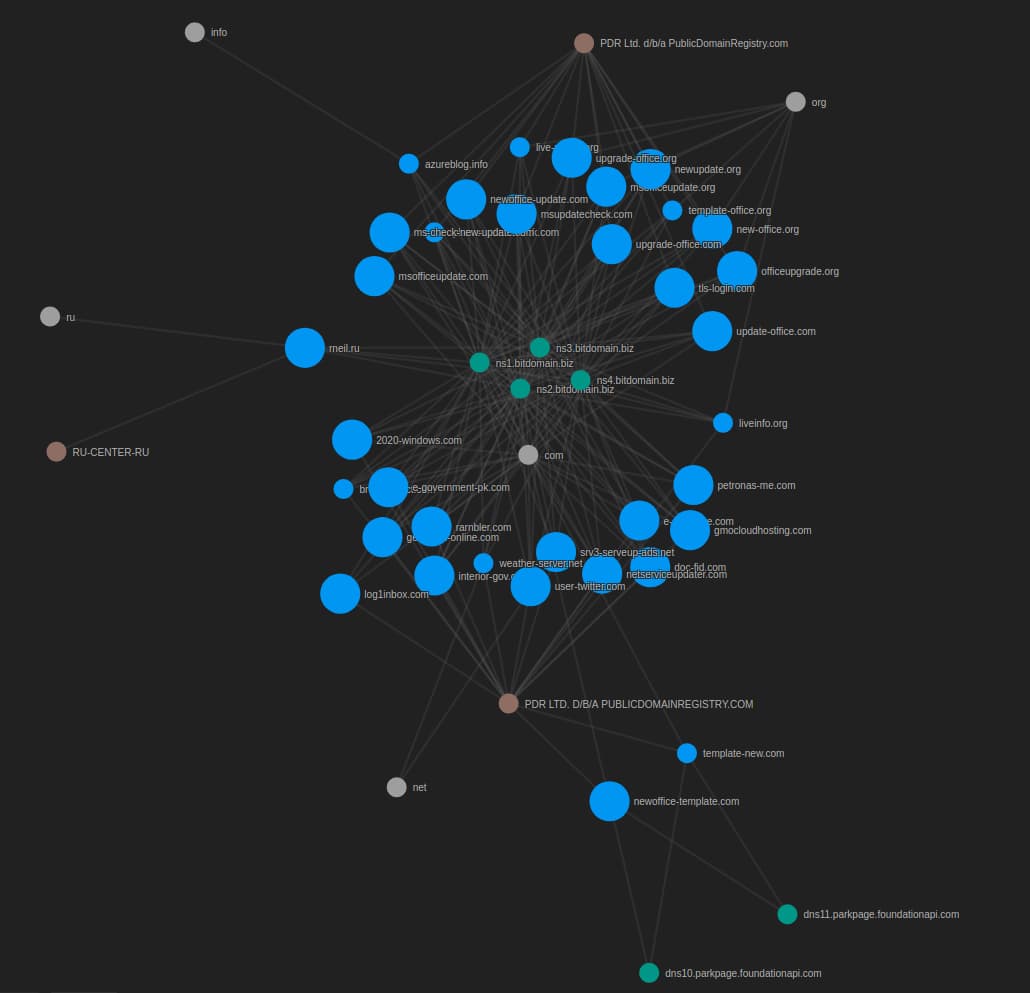
Observed visually, such as in the DomainTools Iris Investigate visualization below, we see clusters of activity divided between name servers, registrars, and Top Level Domains (TLDs). With an even larger population, we could begin to distill even more aspects of this adversary’s methods of operation and potentially devise predictive algorithms for future infrastructure creation.
Locating Additional Samples
In addition to identifying additional network infrastructure, a combination of reviewing the original document as well as pivoting off of observed network infrastructure yields additional malicious document samples. Primarily, the unique Template string of numbers combined with relationship to domains and document themes enable the discovery of additional items. As shown in the following table, these items are linked through both the unique Template string as well as contacting infrastructure related to the analysis provided above on network observables.
| SHA256 | File Namestrong | First Seen | Submitter Country | Domain Contacted |
|---|---|---|---|---|
| 1f117d5f398e599887ec92a3f8982751ceb83f2adb85d87a2c232906104e8772 | C. Bayramov.doc | 25 Jul 2020 | AZ | upgrade-office.org |
| 4ad0e64e8ebed1d15fac85cd7439bb345824f03d8b3c6866e669c24a42901daa | Scandal that killed 346 people.doc | 29 May 2020 | AZ | upgrade-office.com |
| 68bde4ec00c62ffa51cef3664c5678f1f4985eb6054f77a5190b4d62bd910538 | xyz.doc | 13 Sep 2020 | TR | msofficeupdate.org |
| 7ba76b2311736dbcd4f2817c40dae78f223366f2404571cd16d6676c7a640d70 | Фадеев М1.doc | 18 Dec 2019 | UA | officeupgrade.org |
| 7c495c21c628d37ba2298e4a789ff677867521be27ec14d2cd9e9bf55160518f | PKK militants in Nagorno-Karabakh.doc | 12 Oct 2020 | AZ | msofficeupdate.org |
| 89503c73eadc918bb6f05c023d5bf777fb2a0de1e0448f13ab1003e6d3b71fef | О поставке зенитных ракетных систем С-400.doc | 11 Dec 2019 | AZ | officeupgrade.org |
| c630aa8ebd1d989af197a80b4208a9fd981cf40fa89e429010ada56baa8cf09d | Планируемые расходы 2020(1).doc | 28 Dec 2019 | UA | officeupgrade.org |
| e5a4957d0078d0bb679cf3300e15b09795167fdcfa70bbeab6de1387cd3f75bf | Strategic Defence and Security Review (2021 SDSR).doc | 31 Oct 2020 | SI | msofficeupdate.org |
| 7a1effd3cfeecdba57904417c6eeaa7a74d60a761138885b338e8dc17f2c3fbc | Справочник АП_26.10.2020_.doc | 29 Oct 2020 | UA | msofficeupdate.org |
| 0b116f5b93046c3ce3588bb2453ddbb907d990c2053827600375d8fd84d05d8b | Новые поправки к Госпрограмме переселения в РФ (вст. в силу 01.07.2020).doc | 16 Sep 2020 | UA | N/A |
| 79c0097e9def5cc0f013ba64c0fd195dae57b04fe3146908a4eb5e4e6792ba24 | N/A | 16 Sep 2020 | GB | newoffice-template.com |
| d8f13e6945b6a335382d14a00e35bfefadbdfb625562e1120e5ed0b545f63e11 | N/A | 09 Nov 2020 | N/A | template-new.com |
| 348b25023c45ed7b777fa6f6f635cb587b8ffbf100bfa6761d35610bba525a11 | Минтруд госслужба.doc | 04 Nov 2020 | UA | msofficeupdate.org |
| 93279005aa4c8eddf01020b31bc2b401fe1366cbcc9bb2032ffaeb2984afcd79 | Минтруд госслужба 1 1.doc | 03 Nov 2020 | UA | msofficeupdate.org |
As described in greater detail in the following section, these items largely feature themes related to conflict in the Caucasus or continuing conflict in Ukraine. Additionally, they extend from December 2019 through November 2020, indicating this activity has continued without significant change for nearly a year.
In addition to these items, DomainTools researchers also identified a second set of documents, all originating from France, with a “testing” theme but matching various characteristics of the above items, such as the unique Template string:
| SHA256 | File Namestrong | First Seen | Submitter Country | Domain Contacted |
|---|---|---|---|---|
| 29b49fc728510b8d10a84edbd884cd23a0c453c1158551dbd2d266539d5d09b5 | testmw4.doc | 18 Sep 2020 | FR | N/A |
| da43472f3bced232ae8f905e819339fb75da0224a31fb1c394110c77b3318b09 | testmw8.doc | 18 Sep 2020 | FR | upgrade-office.com |
| 6478821432b8458053d953b6cff7d1b49f4349f5da366278778c87bc8789b65c | testmw7.doc | 18 Sep 2020 | FR | upgrade-office.com |
| 4285a05a993359b8418b590d3309a361f2c42ef7bc29216c0209e57b74513adb | testmw6.doc | 18 Sep 2020 | FR | N/A |
| 40b21a2cd054e01cf37eb22d041ef2ea652eaaeae0ba249439fa7ec07a4e9765 | testmw5.doc | 18 Sep 2020 | FR | aaaaaaa-aaaaaa.com |
| 282c805363469440eef082ac0f2a52dbdd47a8cdaecc08df4c1b4c073c5a8256 | testmw3.doc | 18 Sep 2020 | FR | test.com |
| df2a85d84daf10b4dcf8d8fdd83493f3c04f2ac7b3edaf4730df0522cc52009f | testmw2.doc | 18 Sep 2020 | FR | N/A |
The items above stand out from the other documents for several reasons:
- All were submitted to the same multiscanner service on the same day.
- The items appear to be iterative given the file naming schema (testmw2, testmw3, etc.).
- Analysis of the files indicates fuzzing or alteration of capability among them, in line with the iterative nature of the file names.
An initial conclusion would be these are “testing” runs for a malicious document format or template which would emerge in later campaigns. However, the timing is off for this conclusion to hold as the “test” items appear in mid-September when items using the same template (functionality and lure document) first appear in December 2019.
Overall, this batch of items remains somewhat a mystery as there are no obvious signs linking it to other campaigns. Additionally, some of the items in question are non-functional or lack other components linked to the activity in the first set of documents associated with a likely persistent campaign. DomainTools does not possess any additional information to disposition these items at this time, so they remain somewhat of a mystery relative to the other malicious documents which appear more clearly designed for espionage purposes.
Motivations and Attribution
The identified documents emerge from multiple locations but overwhelmingly focus on Azerbaijan and Ukraine.
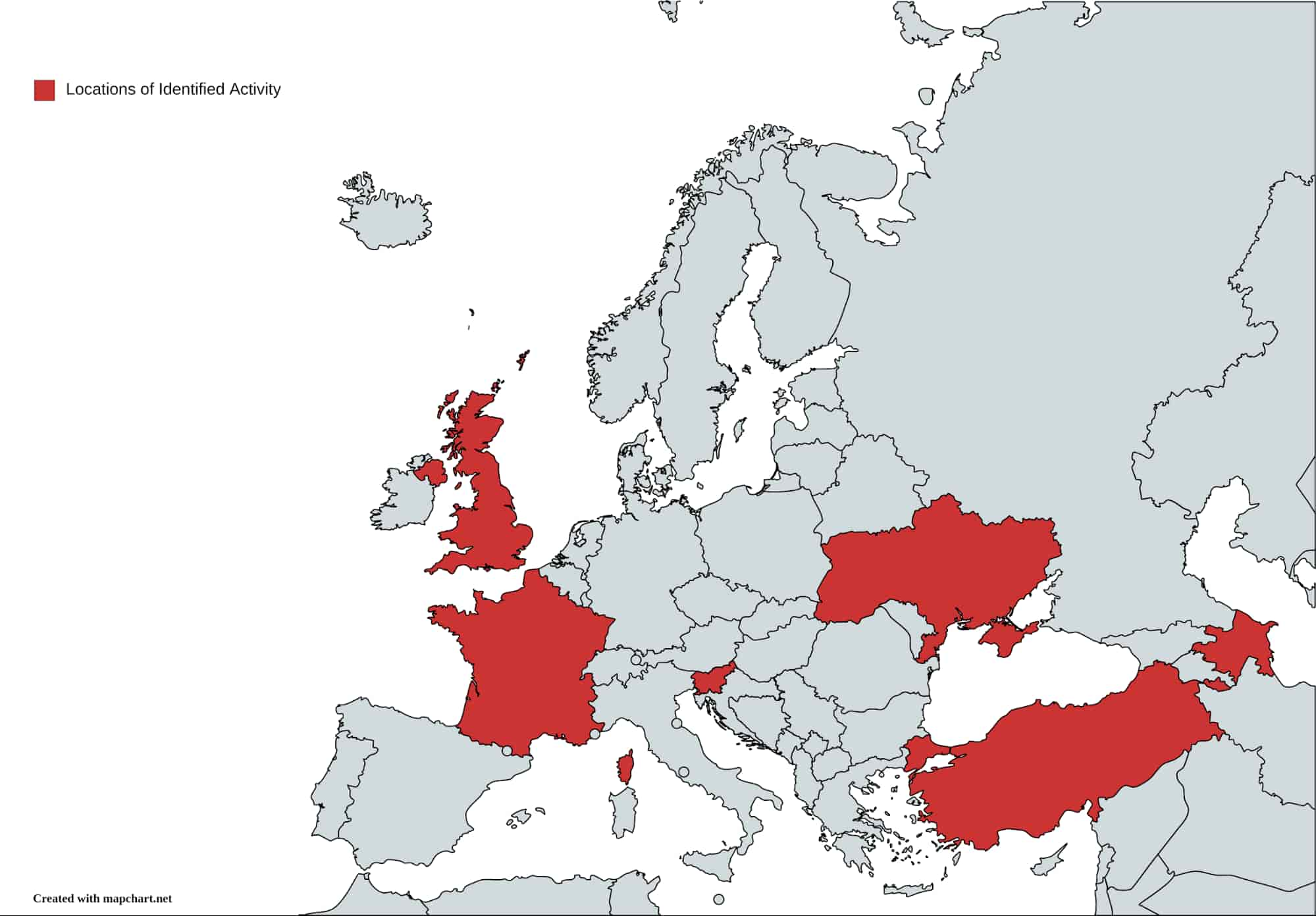
More interesting still are the themes associated with the documents in their text and titles. In addition to the document which sparked this investigation and its themes centering on the recent conflict on the Caucasus, identified topics include the following:
- C. Bayramov.doc: references the Azerbaijani foreign minister, Ceyhun Bayramov.
- Фадеев M1.doc: presents itself as a fundraising advertisement for a documentary filmmaker covering events in the Donetsk region of Ukraine, an area of conflict.
- О поставке зенитных ракетных систем С-400.doc: masquerades as a report on the S-400 air defense system, produced by Russia and sold to multiple countries.
- Планируемые расходы 2020(1).doc: “Planned Expenses 2020”, a document that appears to show personnel expenses for a Ukrainian local government entity.
- Strategic Defence and Security Review (2021 SDSR).doc: a strategic defense planning document intended for the Slovenian defense ministry. Notably, this document appears related to a phishing email sent to an individual who appears to be the Slovenian military attache to the country’s embassy in the Russian Federation.
- Справочник АП_26.10.2020_.doc: a planning document from the Russian-backed but unrecognized breakaway Donetsk People’s Republic.
- Новые поправки к Госпрограмме переселения в РФ (вст. в силу 01.07.2020).doc: a document on internal resettlement within the Russian Federation.
- Минтруд госслужба.doc:a document from the Russian-backed but unrecognized breakaway Luhansk People’s Republic.
Overall, documents appear related to political, military, and related subjects largely in conflict zones such as the Caucasus and the Russian-backed breakaway regions of eastern Ukraine. Additional items, such as the Slovenian defense document which DomainTools researchers were able to link to a phishing email, strongly imply state-sponsored interests for espionage or similar purposes as motivating this campaign.
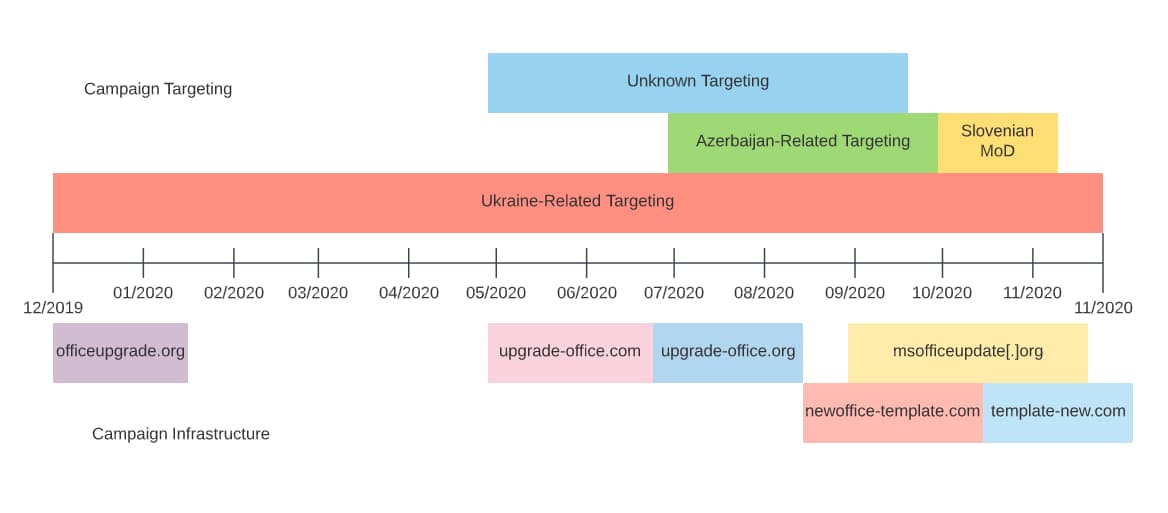
In October 2020, several researchers noticed some of the documents identified in this report and linked it to a group referred to in public reporting as “Cloud Atlas” or “Inception.” While data available at present does not completely align with prior Cloud Atlas activity, the following commonalities are observed:
- Targeting focusing on Russian near-abroad regions.
- Use of template objects for initial activity through malicious documents.
- Likely reliance on network communication to retrieve second-stage tooling for follow-on activity.
The response to the HTTP requests sent by the documents would presumably be the key for aligning the above campaigns to the Cloud Atlas actor, but absent this evidence DomainTools can neither confirm nor deny association to this group at present.
Irrespective of specific attribution, possible links to a known Advanced Persistent Threat (APT) actor (Cloud Atlas) combined with campaign themes that are highly political in nature with no obvious mechanism for monetization make the discovered campaign a likely state-sponsored or state-directed espionage campaign. While targeting in this case may imply Russian-related interests, it is important to note that earlier Cloud Atlas activity has also targeted entities in the Russian Federation. One possible alternative hypothesis given the targeting in Russia, as well as a focus on breakaway regions in Ukraine, is that the activity represents Ukraine-sponsored cyber espionage activity. Although interesting, again insufficient evidence exists to support this hypothesis at this time.
While the activity described above is certainly concerning, available information at this time does not support even weak attribution to any state interest, with only plausible (but as yet unproven) links to the Cloud Atlas entity. Although specific attribution may not be possible, we can nonetheless conclude with high confidence that this activity represents cyber espionage activity directed by some, as yet unknown, state actor.
Conclusion
Tracking themes related to geopolitical events can be quite fruitful for discovering active campaigns likely related to state-sponsored interests. In the above example, searching for items related to the Armenia-Azerbaijan conflict in the Caucasus in late 2020 yielded a malicious document. Further analysis of this document and related infrastructure then led to the discovery of additional items which outlined an entire campaign stretching back to 2019.
While the victims of this campaign appear geographically limited, largely focusing on Ukraine and Azerbaijan, the lessons drawn from the analysis of both the malicious documents and related network infrastructure can be used to further defense against similar types of attacks. By monitoring for these types of event-specific incidents, CTI analysts can gain insight into emerging APT activity and deploy defensive countermeasures shortly after discovery.
To learn how to identify and track adversary operations in DomainTools Iris Investigate visit our product page.





