DomainTools 101: The Art of Tracking Threat Actors
On the side of police vehicles, you’ll often see the motto “To Protect and Serve” — except in the Transformers movies where the police car has the motto “To Punish and Enslave”. Sam Witwicky mistakenly thinks the police car is his friend when it is really against him.

Some days the internet might seem that same way since we often see domains that appear to be one thing but when you look a little closer, you see that they are something different. When threat hunting, you have to look very closely to see the differences. Here is a sample of a world cup website that might look good, but is in fact a scam: cheapfootball-jerseys[.]com.
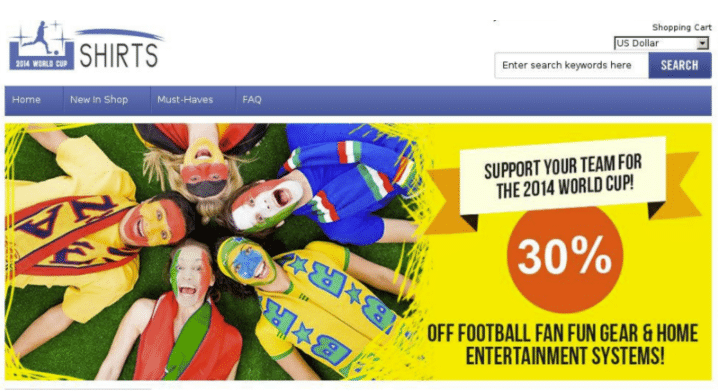
Other Examples Back in January 2016 Palo Alto Networks research team published a paper about a group based in China that went by the name “C0d0so0” or “Codoso”. In this particular article, they mentioned a couple of domains that were part of the Command and Control, or C2 infrastructure. These are the main domains mentioned;
- jbossas[.]org
- supermanbox[.]org
- microsoft-cache[.]com
These domains might look like the real thing, but when you look closer, you’ll see that they are not good at all.
I was able to use DomainTools Iris Investigate to learn that these domains were tied to a single email address. Using that email address, I set up a registrant monitor to track the newly registered and dropped domains tied to this user. Out of my 20+ current Registrant monitors, this one has proved to be my most active Registrant monitor. Most of the domains registered to this group are Command and Control, or C2 domains, although the actor also registers domains that appear to be selling counterfeit goods. Like the counterfeit jerseys above.
Around October 1st, I noticed that there was a significant downturn in the number of domains being registered or dropped. Although I have noticed downturns in registrations for things like summer vacations, this instance felt different. I was only seeing one or two new domains being registered a day, and many of my daily reports illustrated that domains were being dropped. This piqued my interest so I set out to see if I could find out what might be the cause of this drop in registrations. I started my Iris Investigate probe by looking at domains that had been registered to see what details they were using like the registrant name. I also filtered results down to domains registered in the past 30 days.
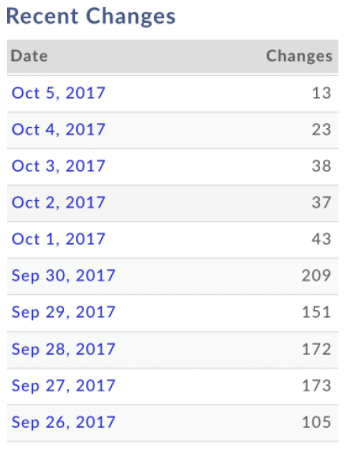
That’s where I found the answer to my question. The email address that was previously used was bodfeo at 163[.]com I began my investigation with this email address, and pivoted out on the registrant name “gueijuan xu”. Using stats panel in Iris Investigate, I was able to find a new email address bodfeo at Hotmail[.]com at the time of writing this blog, there are almost 2,700 domains registered using this email address, all registered at the starting at the end of September. So we can see that the actor has started using a new hotmail email address in addition to the original email address at 163[.]com, a large Chinese email provider.
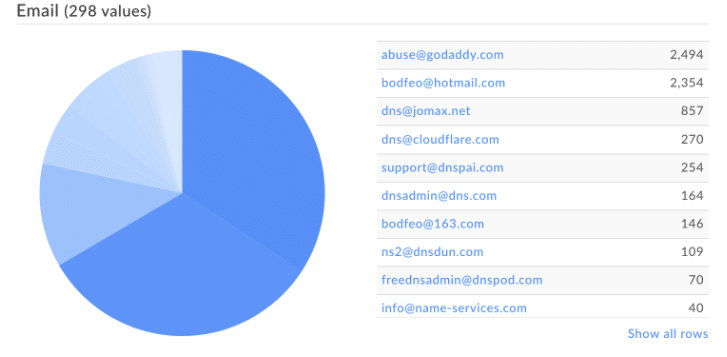
One of my key takeaways from this investigation was learning more about how threat actors are constantly changing their tactics, techniques and procedures. We as security professionals have to be able to find ways to track threat actors. DomainTools Iris Investigate and monitoring tools are great ways to get ahead of the threat actors.
Safe Hunting.




