DomainTools App for Demisto - Comprehensive, Contextual and Automated Incident Response
Human capital remains the most constrained resource within security teams in the midst of growing cyber warfare. Adding to this issue is the constant challenge of reconciling internal assets and event data with known Indicators of Compromise (IOC) and threat actors.
In spite of the technological advancements in SecOps, analysts continue to spend a disproportionate amount of their time manually reviewing and exploring external data sources while investigating a malicious domain or IP. Establishing such relationships between an IOC and other data sources provides the incident response analyst critical context during the incident remediation process. However, the triage and analysis process can be extremely time-consuming and often becomes a bottleneck. A helpful addition to the SecOps workflow would be a way to automate the enrichment and qualification of IOCs.
With the DomainTools Iris Demisto integration, we can help you corroborate DNS artifacts and determine corrective actions.
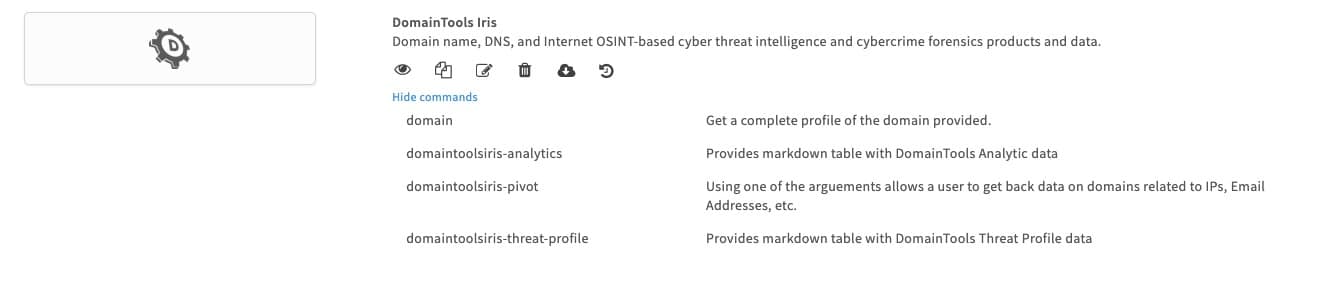
The new Demisto Iris App brings contextual DNS intelligence from DomainTools Iris to Demisto. Security teams using Demisto can leverage the App plugin to automate the enrichment of malicious observables within incidents. Security analysts can now leverage DomainTools intelligence across all their response workflows and automate mundane tasks.
There Are Two Major Use Cases:
Ad Hoc DNS Investigations From Within Demisto
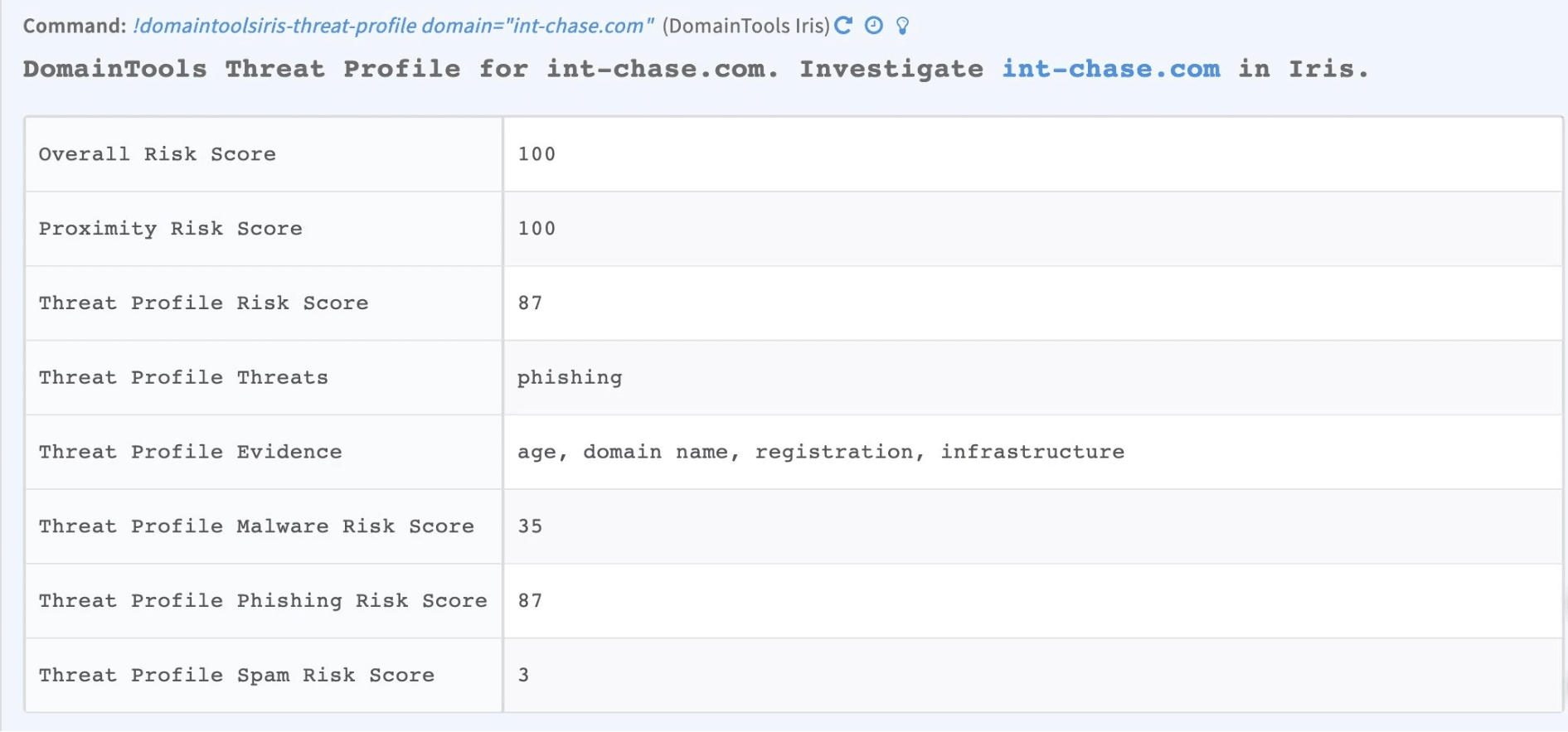
Analysts can now eliminate context switching and perform interactive domain investigations from within the Demisto War Room. The App enables a key set of purpose-built commands that presents core intelligence like DomainTools Risk Score, etc. from DomainTools Iris in a human-readable format. The built-in functionality of War Room automatically keeps track of investigations performed for convenient incident reporting.
Automate Enrichment of DNS intelligence for Incidents
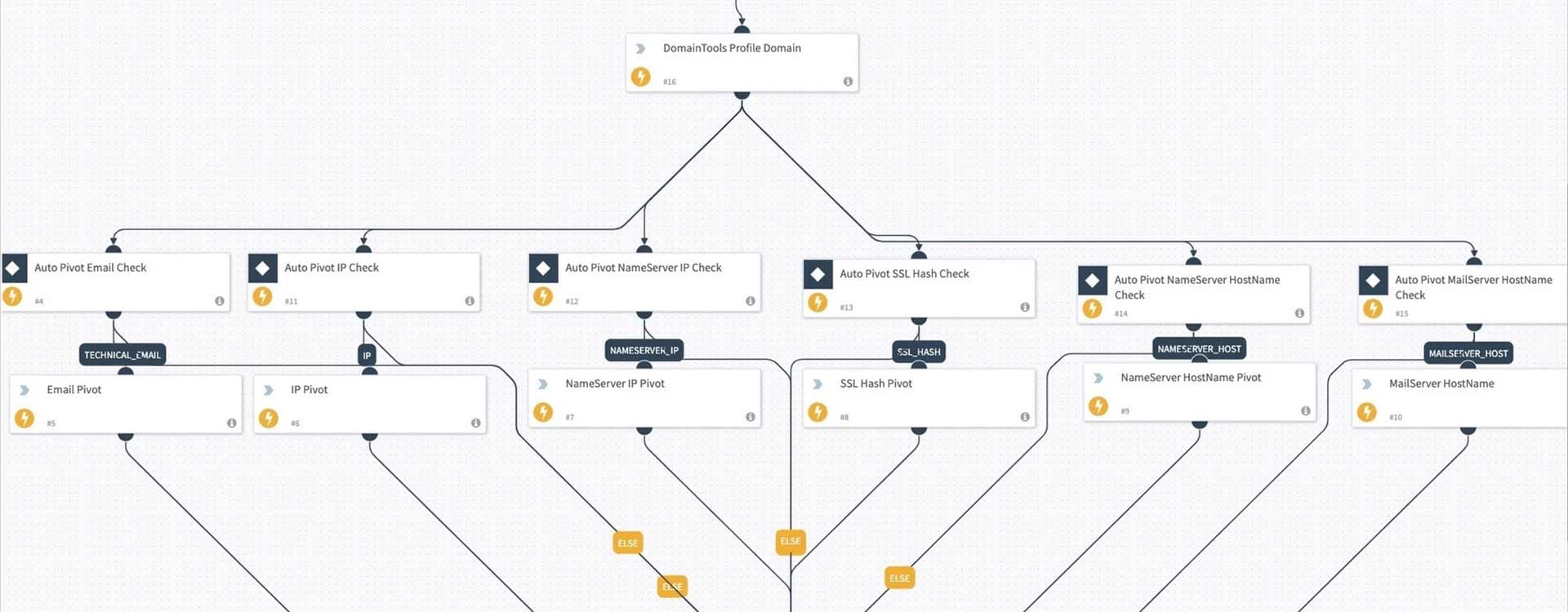
The plugin enables security teams to automate playbooks that can enrich DNS observables at scale with DomainTools Iris intelligence. Not only do analysts have access to critical context inside of Demisto ContextData, but they also have the ability to store the DomainTools enrichment intelligence inside of the indicator table. This allows analysts to correlate the domain and DNS intelligence and establish connections of the IOC across incidents, within their organization.
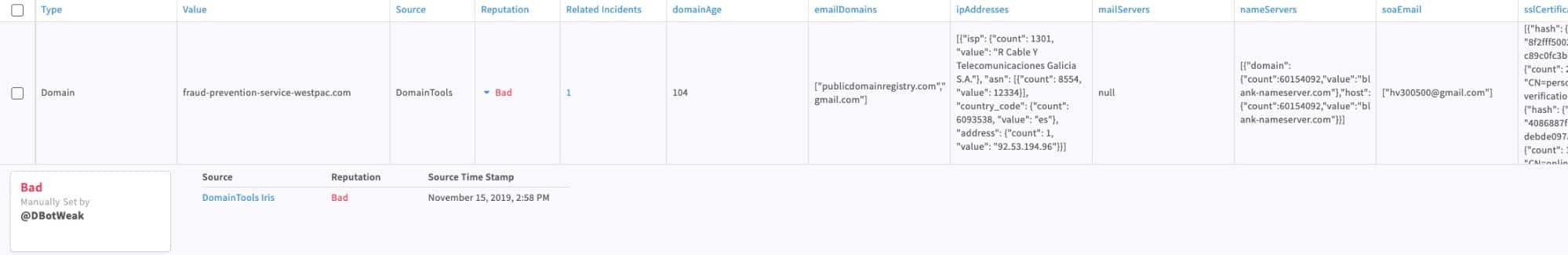
We also included automation scripts and playbooks as a reference that will enable analysts to automate the investigation process to discover connected malicious infrastructure associated with a known bad indicator.
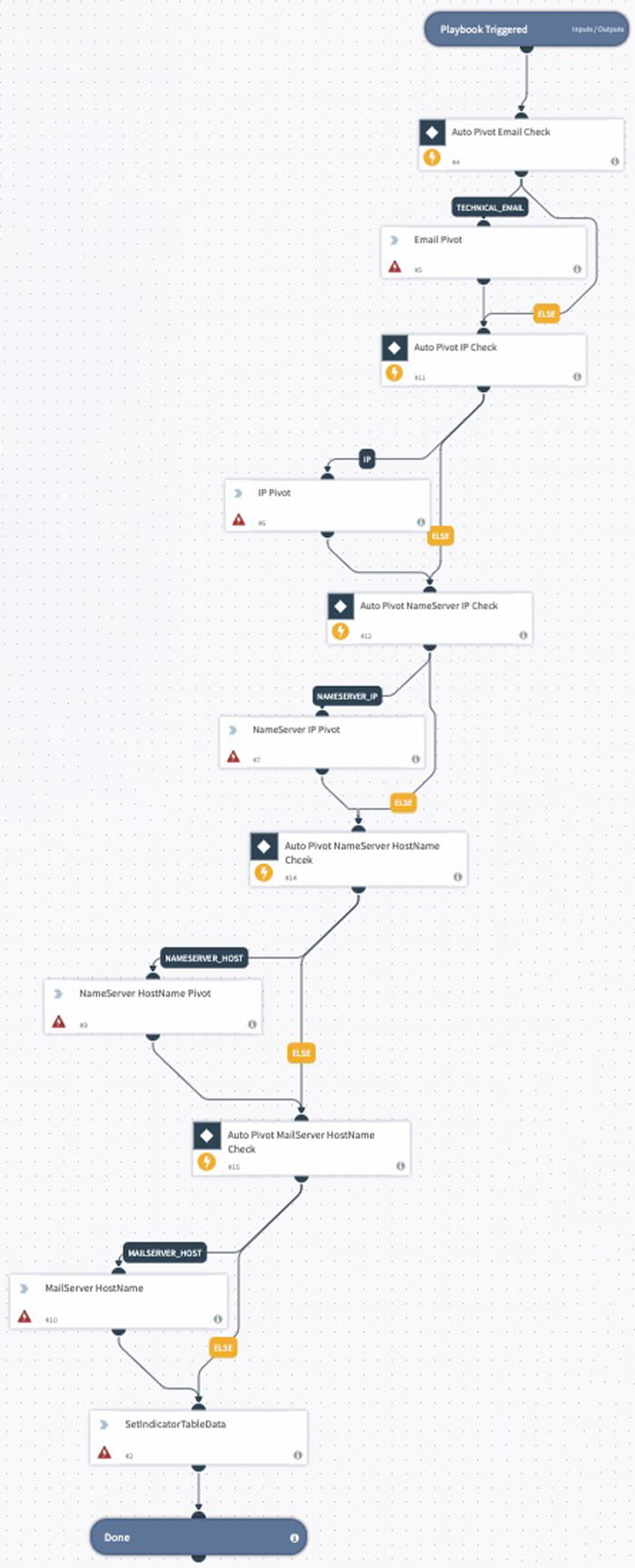
Many DomainTools and Demisto users currently leverage prior versions of this integration in automating DNS investigations and enrichment. Now, with the availability of the DomainTools Iris dataset within Demisto, users can further optimize and reconcile investigation steps inside of Demisto.
As we see consistent growth in the maturity of SOAR implementations across security operations, we expect to discover additional ways to automate DNS enrichment throughout your workflow. Please send any feedback to [email protected], I would love to hear how we can further improve your workflows.