Guess who's back, back again? DTI’s back, tell a friend!
Share this entry
Well hello there! If you are a returning reader, that likely means you found this information beneficial to your organization or all of my jokes last month absolutely KILLED. Or all of the above! Either way, welcome back!
If you’re new around these parts, I’m Daniel Schwalbe, CISO and Head of Investigations at DomainTools, and the purpose of this newsletter is to share an overview of what my team at DomainTools Investigations (DTI) has worked on in the past month.
Before we dig into that, I recently returned from a trip to Japan with my family. It was a whirlwind tour, but even my teenagers loved it! Here’s some of the cool things we did:
We started out in Tokyo, where we met up with an old high school friend of mine who’s been living there for more than two decades. He gave us a crash course in Tokyo’s excellent public transit system.

He showed us around Shinjuku, Roppongi, Akihabara (“Electric Town”), Musashino, Setagaya, and Shibuya.

Next, we took the Shinkansen (the “bullet train”) to Hiroshima to pay our respects, followed by stops in Osaka (the Cup Noodle Museum was fun!) and Kyoto (check out Nishiki Market). We stopped by some of the locations featured in the recent “Shōgun” TV Series, and ate local specialties (Okonomiyaki, Katsu). Speaking of food, it was amazing: Sushi, Ramen, Teppanyaki, Shabu Shabu, Sukiyaki, the list goes on.
If you are into shopping, the Don Quijote stores are amazing (and a little overwhelming)!
We departed Tokyo at 6pm, and arrived on the west coast at 10am the same day. Time Travel is real, but so is jet lag. Good thing I’m going to Europe soon – read on for more. But enough about my recent travels, let’s jump into what the DTI team has been up to since last month’s newsletter:
RATs! There’s More to Say on Chinese Malware
There’s more to say on this topic, which we covered in our inaugural newsletter, examining a second cluster of over 1100 domains suspected to have been registered by the same group between April 2024 to January 2025. Very similar to Cluster 1, Cluster 2 involves spoofs of many common applications from messenger apps, VPNs, cryptocurrency exchanges, gaming platforms, game emulators, online gambling, web browsers, and multimedia apps.
Why Is This Important? A crucial aspect of this investigation lies in recognizing the broader implications of the observed tactics. By proactively studying and understanding these techniques now, the cybersecurity community can better prepare for similar threats that may emerge.

Get the full scoop and IOCs here.
Yes And…
CSIRT Gadgets took a look into parts I and II of this Chinese malware story and
- Their writing is pretty hilarious (10/10 would read again) and,
- They used a tool called AlphaHunt to find likely linkable attribution (though YMMV).
Based on what DTI sees and what others in the community have reported, AlphaHunt makes the argument that this threat actor could be the SilverFox APT group.
Take a gander – let us know what you think. We’ve already ruled out other silver foxes like George Clooney and Patrick Dempsey, but can you contribute any additional findings that this is indeed the SilverFox APT group?
Cheers to the Good Guys
The Justice Department published a release in late January regarding seizing servers of the Pakistan-based threat group known as the Manipulaters (and that is how “they” spell).
You may recall last year DomainTools Research looked into this group previously thought to be dormant and found they were very much back to their old tricks – with some new ones thrown in there. The FBI and the Justice Department’s Criminal Division, in cooperation with law enforcement partners in the Netherlands, have taken down 39 domains and related infrastructure linked to this group! Chalk one up to the good guys!
Find our research here, updated to reflect this takedown.
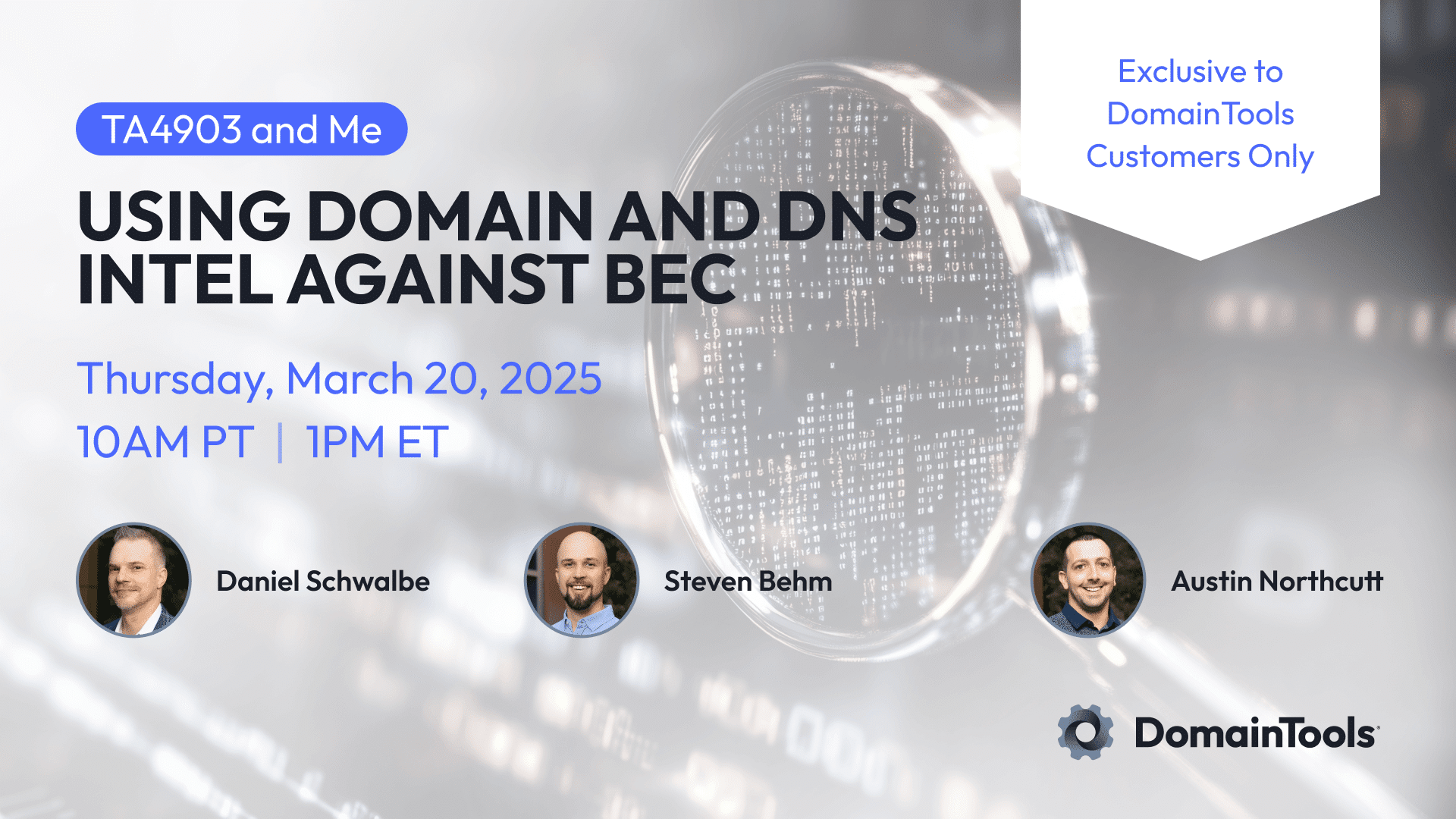
Double Secret Probation Webinar
It’s not actually that secret; you just need to be an existing DomainTools customer to attend. I’ll moderate this discussion with DTI team members Steve Behm and Austin Northcutt as they use our domain and DNS intelligence platform to demonstrate how to stay ahead of Business Email Compromise (BEC) using the example of TA4903, a financially motivated threat actor with notoriously high campaign volume.
BUT WAIT! There’s more! After the webinar concludes, attendees can get a 14-day trial for the tools we showcase in the demonstration, if they don’t currently have access to them.
DomainTools customers can save their spots here.
Where We’ll Be
- NICAR – 06 March
- I’ll be teaching a workshop with my colleague, Kelly Molloy
- Finding the Story Using DNS search for investigative journalism
- DCC – 10 to 13 March
- IYKYK. Come say “Hi” if you are attending.
- Closed Door Sessions (Invite-Only, TLP:RED research – say I referred you)
- Seattle – 26 February (almost at max capacity)
- Austin – 01 April
- Boston – 03 April
- FIC – 01 to 03 April
- Catch my colleague Malachi Walker at FIC in Lilles, France.
Final Thoughts
Again, if you’re a returning reader for last month, I thank you. If you’re new, I hope you found this newsletter informational, helpful, and worthy of sharing with your peers.
We share this newsletter via email as well – if you’d prefer to get it to your inbox, sign up here.
If you missed last month’s content, here are some quick links:
Account Trafficking Websites in December 2024
Chinese Malware Delivery Websites
CTI Grapevine Becomes DomainTools Investigations
Cyberhaven Breach Likely Part of a Long-Term Criminal Campaign
Thanks for reading – see you next month!
Daniel





