DomainTools Iris for MISP
My mother operated a daycare and preschool out of our home when I was growing up. Everyone loved her, kids and parents alike, and things went along just fine, until someone decided they didn’t want to share.
From some corner of the front yard you’d hear “no, that’s MINE, you CAN’T HAVE IT”, and every kid who was already aware of Mrs. Kendrick’s passion for sharing would scatter in all directions to ensure they were not collateral damage in whatever justice she would mete out upon that ungenerous youngster.
I get the sense the creators and developers of MISP were raised with similar values, because they clearly believe that sharing is caring, especially when defending against cyber attacks, and they have woven that belief into the very fabric of their open source project.
If you’ve not aware of MISP, I’d encourage you to take a serious look at it.
It’s an open source, community-maintained, no-cost implementation of a threat intelligence platform that helps you ingest, analyze, and share indicators of compromise (IOCs).
Sharing is certainly a core feature of the platform, but thankfully, the project maintainers are not so dogmatic about it that you are forced to use those features. That has undoubtedly contributed to the project’s success – it has broad adoption in big enterprises, national CERT teams, tiny one-person threat intel shops, and everything in between.
If you’d like an example, check out this webinar I hosted last year to learn how Jack Henry and Associates, a US-based financial services company, leverages MISP in their cybersecurity practice, including a novel use of the sharing mechanism to bridge disparate parts of their security organization.
MISP is now a very mature, feature-rich, actively-maintained project, to the extent that, for many organizations, it presents a viable alternative to commercial threat intelligence platforms.
MISP also has a healthy ecosystem of integrations and a solid plugin architecture that makes it easy to extend its capabilities, and indeed, DomainTools has leveraged that to great affect, with our previous set of MISP modules built on our enterprise API endpoints.
The next step was clear – we wanted to bring the rich dataset of our Iris research platform into MISP, and find ways of tying the two experiences together. The features in our Iris Investigate API were built precisely for this purpose, and today, we’re excited to announce the availability of a powerful set of DomainTools Iris MISP modules.
The new Iris-aware MISP modules bring in nearly everything we know about a domain. We display a subset of that data in MISP hovers and tooltips for quick analysis and triage, including domain age, IP country, ISP, and more, plus the complete list as on-demand enrichment attributes to easily add to your event.
One of the things I love about MISP is the correlation engine, and our data is ideally suited to leverage that. You might not find hits in your threat intel feeds for the phishing domain you’re investigating, but enrich it with Iris data, and you’ll have a better shot at finding it’s hosting IP, SSL hash, or whois contact details in published feeds or MISP events shared by your peers.
The DomainTools modules for MISP include not just our predictive Domain Risk Score , but also the components of the score that reveal the specific machine learning classifiers that influence that score.
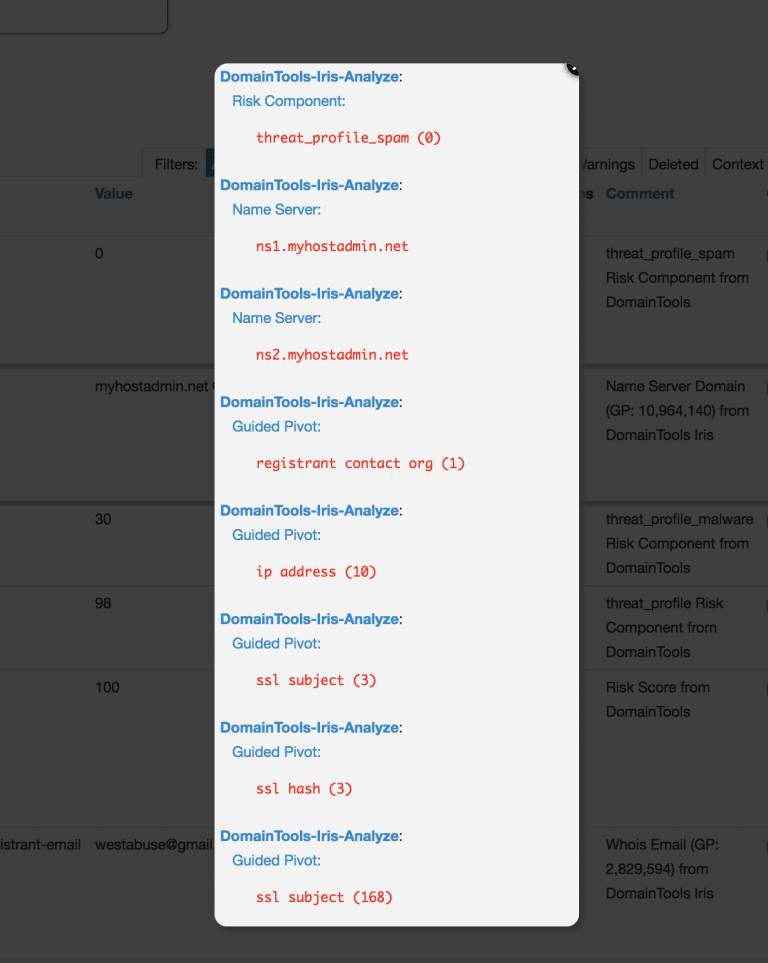
Profiling a domain is only the first step – what you really need to know is all the other domain names controlled by the actor, and the IOCs that describe the dedicated infrastructure, boutique registrars and SSL certs they are using.
You can find that by pivoting in DomainTools Iris on dozens of fields, and of course, we enable as many of those pivots in our MISP module as possible, but how do you know here to start?
The answer is what we call Guided Pivots – connection counts on most fields in Iris that show how many domains are shared by a given attribute, like an IP, email address, or SSL hash. It’s one of the most beloved features in Iris, and since we wanted these counts visible in MISP, we added them to the comments field for each attribute our API returns.
Guided Pivot counts often deliver meaningful analytics on their own, even before you pivot – if you spot an IP address with fewer than, say, 50 domains pointed to it, you’ve likely discovered the actor is using a dedicated web host.
This can be so effective in an investigation, we decided to tag any attribute with a small number of shared connections with a “Guided Pivot” tag in MISP to make these easier to find.
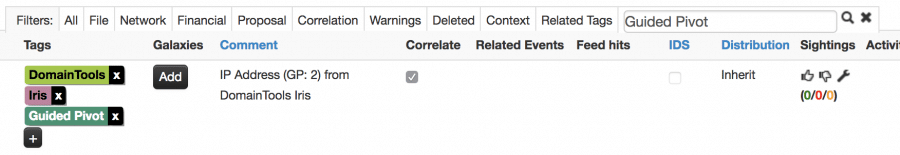
Once you’ve honed in on a useful pivot, you can leverage the modules to bring in the list of shared domains, further increasing your chances of finding correlations with other MISP events. Our module can pivot on registrant name, registrant email, registrar, IP address, nameserver, or SSL certificate hash.
But what if you need to pivot on other fields?
Perhaps you’re building a “digital fingerprint” that needs complex boolean logic to describe the set of hosting, identity, SSL cert and tracking codes to profile a specific attacker? How about digging through historical whois data, or correlating with pDNS sightings? Are you lost? Would an investigation history help? How about a graph visualization? You’ll want to use Iris UI for that – it’s designed for precisely those kinds of investigations, and you’d be amazed what you can uncover with it.
After just a few minutes in Iris, you’ll have a nice, tidy list of evil domains that should be cataloged, shared with your colleagues, and pushed into your alerting and detection logic. MISP can handle all that for you, if you can get the domains into it – CSV is so 1980, and STIX is, well, STIX, so we built a MISP module just for this purpose.
It’s simple to use – you grab the search export blob from the advanced search pane in Iris, fire up the DomainTools Iris Import module in MISP, paste in the blog, and bam, all those domains are now attributes of your MISP event.
As you can imagine, we’re quite excited about these features, and we can’t wait for you to give them a try. Since there’s no cost to use MISP, there’s no reason to hesitate. Even better, the Iris Investigate API is available at no additional charge for all DomainTools Iris customers, so if you’re already using Iris, you’ve got no excuse not to try out MISP.