Finding New ASNs
Share this entry
A surprisingly large number of ASNs get assigned by the Internet’s regional registries every month, see table 1.
| Regional Registry | Average New ASNs/Month | Reference |
| RIPE NCC | 181 | https://www.iana.org/numbers/allocations/ripencc/asn/ |
| APNIC | 146 | https://www.iana.org/numbers/allocations/apnic/asn/ |
| ARIN | 90 | https://www.iana.org/numbers/allocations/arin/asn/ |
| LACNIC | 53 | https://www.iana.org/numbers/allocations/lacnic/asn/ |
| AFRINIC | 15 | https://www.iana.org/numbers/allocations/afrinic/asn/ |
| TOTAL | 485 |
That’s a lot of new ASNs.
Other times, ASNs that have laid dormant for some years may be “reanimated” and suddenly reappear in the routing tables.
While both the brand new ASNs and “newly reanimated” ASNs may be used for totally legitimate purposes by totally legitimate parties, in other cases, those newly-seen ASNs may be staged for insalubrious purposes. Either way, newly seen ASNs may be worth a closer look. Today we’re going to describe how you can easily find those new ASNs.
“So, What Is An ASN? Why Would I Be Interested in ASNs as a Cybersecurity Person?”
An ASN, or Autonomous System Number, is defined as a number assigned to a group of network addresses, managed by a particular network operator, that share a common routing policy. Most ISPs, large corporations, and university networks have an ASN. For example, Google uses AS15169, Sprint uses AS1239, Intel uses AS4983, the University of California at Berkeley uses AS25, DomainTools uses AS17318, and so on. Some large networks with particularly complex routing policies may have more than one ASN; others, with simple routing policies and only a single upstream network provider, may have none (their network blocks are just announced using their upstream provider’s ASN).
Think of an ASN as a number that “maps to” or represents a particular provider or network. As such, it is a useful way to aggregate and sort IP addresses into useful chunks, even though its initial purpose (and continued most important usage) is in conjunction with BGP4 for inter-AS routing of network traffic.
Some specific examples of cybersecurity uses for ASN data:
- Team Cymru has an excellent IP to ASN mapping service you can use to map a list of IPs to their corresponding ASNs, see https://www.team-cymru.com/ip-asn-mapping
- We’ve previously explained how to “Automatically Go from An Autonomous System Number (ASN), to the Prefixes It Announces, to the Domain Names Seen Using Those IPs,” see https://www.domaintools.com/resources/blog/automatically-going-from-an-autonomous-system-number-asn-to-the-prefixes-it-announces-to-the-domain-names-seen-using-those-ips-another-farsight-dnsdb-api-demo-application-and-whitepaper/
- dnsdbq supports ASN tagging of output, see
https://www.domaintools.com/resources/blog/new-dnsdbq-options-asn-tagging-and-new-output-transforms-added/ - ASNs also effectively define “online neighborhoods” of sorts, with some ASNs having good reputations, and others having less-good ones. We’ve previously demonstrated computing aggregate per-ASN risk profiles in
https://www.domaintools.com/wp-content/uploads/Domains-That-Begin-With-A-Digit.pdf - Spamhaus even publishes an ASN-based “Do Not Route or Peer” (DROP) advisory list, see https://www.spamhaus.org/drop/ and https://www.spamhaus.org/drop/asndrop.json
Today, however, we just want to focus on how we can find the new ASNs that we haven’t seen before. We’ll snag BGP data from the RouteViews project at the University of Oregon (see https://www.routeviews.org/routeviews/) for this purpose.
Retrieving Routing Data
RouteViews collects data at many different locations worldwide (https://www.routeviews.org/routeviews/index.php/collectors/) so our first decision is, “What collector do I want to look at?” We arbitrarily decided to use data from the collector at Equinix in Virginia. We can see the RIB (routing information base) files for October 2023 for that site at
https://archive.routeviews.org/route-views.eqix/bgpdata/2023.10/RIBS/
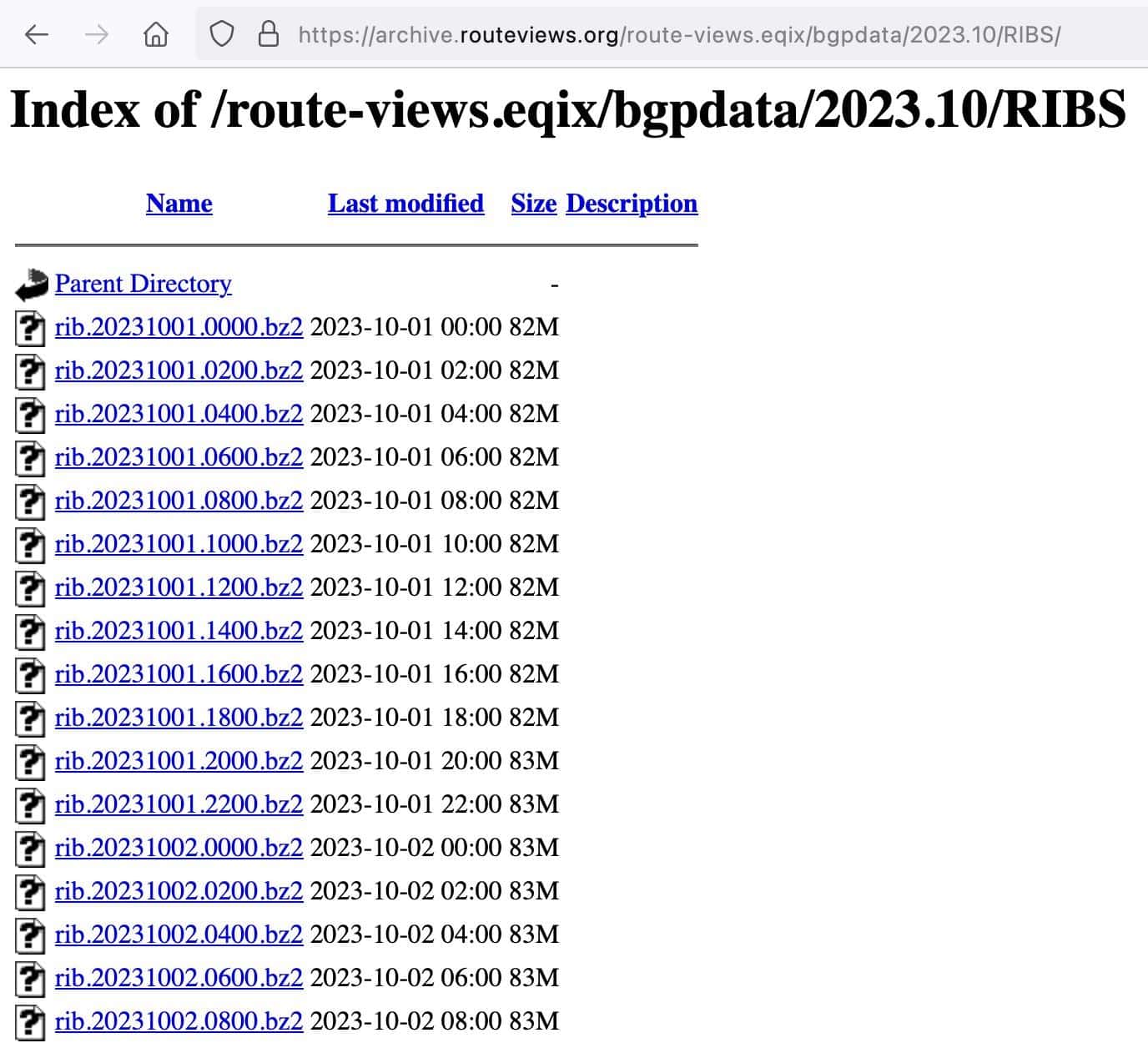
We can download files by pointing-and-clicking links on that page, or we can use a command line web client such as wget (see
https://www.gnu.org/software/wget/) to retrieve files:
$ wget https://archive.routeviews.org/route-views.eqix/bgpdata/2023.10/RIBS/rib.20231012.1400.bz2The file we retrieve is compressed with Bzip2 (see https://en.wikipedia.org/wiki/Bzip2) so our first task will be to decompress it with bunzip2:
$ bunzip2 rib.20231012.1400.bz2Then we can use bgpdump (see https://github.com/RIPE-NCC/bgpdump) to read the decompressed RIB file. Typical entries from the decompressed file output look like:
$ bgpdump -M -v rib.20231012.1400
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.214|57695|0.0.0.0/0|57695 60068 174|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.172|11039|0.0.0.0/0|11039|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.47|19151|1.0.0.0/24|19151 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.214|57695|1.0.0.0/24|57695 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.137|293|1.0.0.0/24|293 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.120|41095|1.0.0.0/24|41095 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.237.22|199524|1.0.0.0/24|199524 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.218|40934|1.0.0.0/24|40934 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.37|6939|1.0.0.0/24|6939 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.25|6079|1.0.0.0/24|6079 13335|IGP
TABLE_DUMP2|10/12/23 14:00:00|B|206.126.236.12|2914|1.0.0.0/24|2914 13335|IGP
[etc]
We want to focus on just the 7th “vertical bar”-separated column (highlighted above) since it has the ASN path for each prefix. We’ll save the extracted ASNs into a file called dumped_asns.txt:
$ bgpdump -M -v rib.20231012.1400 | awk -F"|" '{print $7}' > dumped_asns.txt
We now need to read and process that data. We’ll do that with a little Python3 program called accumulate-asns.py. It will essentially read the ASN data, split it up, and then add each ASN to a Python3 set if it isn’t already a member, printing out any newly-seen ASNs along the way.
$ cat accumulate-asns.py
#!/usr/local/bin/python3
import sys
asn_set=set()
# we save state
oldasns=open("old_asns.txt", "r")
for asns in oldasns:
asns=asns.rstrip()
asn_set.add(asns)
# we are going to look for new ASNs in this new RIB
for line in sys.stdin:
asns = line.split(" ")
num_of_asns=len(asns)
for asn in asns:
asn=asn.rstrip("}")
asn=asn.lstrip("{")
asn2=asn.split(",")
for my_as in asn2:
my_as=my_as.rstrip()
if my_as not in asn_set:
print(my_as)
asn_set.add(my_as)
We can then run that program. The first time we run it, we need to create an empty initial “old_asns.txt” file for our code to “read:”
$ touch old_asns.txtWe can then run our program:
$ cat dumped_asns.txt | ./accumulate-asns.py | sort -n > base-asns.txtWe now have a “base list” of ASNs in base-asns.txt. If you want to save a pristine copy of this file, now’s a good time to do so.
Finding What’s New: First Addition…
New RIB files get saved every two hours. So after a couple of hours we can then run:
$ wget https://archive.routeviews.org/route-views.eqix/bgpdata/2023.10/RIBS/rib.20231012.1600.bz2
$ bgpdump -M -v rib.20231012.1600 | awk -F"|" '{print $7}' > dumped_asns_2.txt
$ cat dumped_asns_2.txt | ./accumulate-asns.py | sort -n > base-asns-new.txt
We then have a list of newly-seen ASNs in base-asns-new.txt
We’ll update the old_asns.txt file by adding the newly discovered ASNs to it.
To make it easy for the reader to “grok” the new ASNs interactively here, we manually re-arranged and augmented that list of ASNs with associated provider details from https://bgp.he.net/
20362 VeriSign Global Registry Services
36625 VeriSign Global Registry Services
36631 VeriSign Global Registry Services
396547 VeriSign Global Registry Services
396554 Verisign Global Registry Services
9501 AS number of Chemical & Metallurgical Design Co. Ltd. (PBC) [India]
40006 Tri-County Wireless, LLC [US]
42491 Arpage AG [Switzerland]
49996 Individual entrepreneur Vyacheslav Yuryevich Anisimov [Russia]
60381 Pana Services Ltd [UK]
135500 R Systems International Limited [India]
151531 PT Data Telematika Indonesia [Indonesia]
200208 SOLNET COMUNICACION SL [Spain]
216184 CNC BILISIM HIZMETLERI INSAAT SANAYI VE TICARET LIMITED SIRKETI [Turkey]
328353 Methodist University College Ghana [Ghana]
65000 [private ASN]
65555 [reserved ASN]Getting In the Rhythm: Finding a Second Batch of New ASNs
And a few hours later, a new RIB is available for processing…
$ wget https://archive.routeviews.org/route-views.eqix/bgpdata/2023.10/RIBS/rib.20231012.1800.bz2
$ bunzip2 rib.20231012.1800.bz2
$ bgpdump -M -v rib.20231012.1800 | awk -F"|" '{print $7}' > dumped_asns_3.txt
$ cat dumped_asns_3.txt | ./accumulate-asns.py | sort -n > base-asns-new.txt
33179 Two Monkeys LLC [Sheridan WY]
58249 Sky Dragon Company With Limited Liability [Iran]
64289 Macarne LLC [Sacramento CA]
135740 Netlife Network Pvt Ltd [India]
141611 PT Interkoneksi Dan Komunikasi Indonesia [Indonesia]
216179 Nathaniel Bill [UK]
329221 TANZANIA ELECTRIC SUPPLY COMPANY LIMITED [Tanzania]Once again, we’ll update the old_asns.txt file with our newly discovered ASNs.
And A Third Run
And one last time…
wget https://archive.routeviews.org/route-views.eqix/bgpdata/2023.10/RIBS/rib.20231012.2000.bz2
bunzip2 rib.20231012.2000.bz2
bgpdump -M -v rib.20231012.2000 | awk -F"|" '{print $7}' > dumped_asns_4.txt
cat dumped_asns_4.txt | ./accumulate-asns.py | sort -n > base-asns-new.txt
11913 Elevate Homescriptions [Orem UT]
23398 Dasan Zhone Solutions, Inc. [Plano TX]
35659 GERMAN NETWORK GMBH [Germany]
37085 The Open University of Tanzania [Tanzania]
131074 APNIC R&D Centre JP [Australia]
131694 PT Jabikha Teknologi Indonesia
150335 Brosis Communication [Bangladesh]
151765 NAKODA NETWORK PRIVATE LIMITED [India]
197438 Julius Birkhofen [Germany]
199114 McKesson Europe AG [Germany]
216275 Noerdnet ApS [Denmark]
216381 Axians IT Services AG [Switzerland]
394035 Pac-12 Conferences [San Francisco, CA]
399160 Neustar Security Services [Herndon, VA]
As before, update the old_asns.txt file with our newly discovered ASNs.
Conclusion and Next Steps
You’ve now seen how you can use RouteViews data to find new ASNs as they begin to be used. Where could we take this next?
- While we ran our sample data manually, it wouldn’t take much imagination to turn that process into a repeatable, automatable procedure.
- We pulled the data for our monitoring from a single RouteViews collector location, but there are 46 collectors listed at
https://www.routeviews.org/routeviews/index.php/collectors/
Using data from more than one collector might deliver improved visibility for new ASNs, but please retrieve Routeviews data responsibly — don’t pull data if you don’t have the time, system capacity and need for it. - Manually augmenting the newly-discovered ASNs with name and location data encourages familiarity with the data, but is (in honesty) somewhat tedious. An automated process would eliminate some of the drudgery associated with that custodial ASN annotation maintenance work.
- Some ASNs might be of more interest than others — maybe you’re only interested in new ASNs from a conflict region, for example, or maybe you’re an investigator focused only on a particular cyber crime locus. Automatic filtering to support that sort of “fencing” would probably make some people very happy.
- We focused on discovering newly appearing ASNs, but ASNs may also disappear. Things that stop existing may be as interesting as things that have just started to exist. It might also be cool to graph when ASNs are (and aren’t) seen.
- ASNs can be mapped to one or more IP address prefixes. IP address prefixes can be mapped to domains using DNSDB. It might be interesting to know what domains are suddenly coming up on brand new ASNs, eh?
Anyhow, we hope you find this an intriguing topic! If you have any questions, please reach out.