How to Leverage Threat Intelligence in Incident Response to Move from Reactive Tactics to a Proactive Strategy
The “Organized Crime” of Cyber Threat Campaigns in 2020
While bad actors have become more organized and sophisticated by refining their craft, they are not the only attackers a security professional needs to be concerned with in 2020. There are still opportunistic, less skilled hackers that utilize commoditized exploits. These attack strategies are made possible by leveraging resources such as simple phishing kits or even ransomware-as-a-service (RaaS) tactics that are highly profitable and easy to use. These resources assist even the most junior bad actors in leveraging advanced, malicious code so they can move rapidly to create campaigns and execute them with ease.
The threat landscape continues to grow, and security professionals need additional skills, tools, and advanced strategies in their arsenal to combat those who wish to do harm. This blog will outline how to better protect your organization by integrating threat intelligence into your incident response processes.
Incident Response Challenges—The Struggle is Real
Though security teams comprise several roles and are responsible for various functions, incident responders have the heavy burden of identifying anomalies quickly, gathering data to triage the possible incident, and then moving rapidly to neutralize the situation. With the barrage of alert notifications bombarding security analysts, having a process in place to categorize the incident type and then mitigate each threat accordingly is essential to keeping an incident from becoming a breach.
Organizations seek security analysts that have advanced knowledge and experience, especially around incident response best practices. They need to have skills such as the ability to perform deep malware analysis, forensic investigation, and reverse engineering of threats. These senior security analysts can use their knowledge of these complicated processes to create playbooks, guiding their teams to appropriate responses for each threat scenario.
Security teams are constantly hit with a barrage of low-quality alerts from data feeds and a multitude of systems. This creates vast amounts of data to sift through in order to determine which alerts indicate true threats and which are false positives, leaving less time for deeper investigations once true threats are identified. Security analysts need context to enrich alerts to help analysts make more informed decisions based on cleanly presented information. By leveraging threat intelligence and automation, security teams can filter out false positives, prioritize the riskiest alerts, and help less experienced analysts make quick escalation decisions—ensuring highly-skilled analysts spend their time on more skill-specific work.
The Early Bird Gets the Worm by Marrying Threat Intelligence with Automation
The traditional reactive approach to an IOC just isn’t enough anymore. Security teams need to shift to think more proactively by applying tactics such as automating certain aspects of incident response. Leveling-up incident response efforts by proactively evaluating threats in the wild and blocking them before initial interaction can reduce the number of threats that need to be addressed on the network. The external context of threat intelligence can also support quicker decision making during incident response procedures.
At the end of a threat is a person who has a plan to exploit a vulnerability. These people or groups often reuse infrastructure, attack mechanisms, or code to reduce the amount of effort it takes to exploit a target. Threat intelligence provides a window into these tactics, techniques, and procedures (TTPs) associated with bad actors. That intelligence supports the incident response process by identifying when indicators might be associated with a particular group or type of threat—for example, enriching alerts from a Security Information and Event Management (SIEM) and comparing corresponding internal network data with external threats in the wild, employing threat profiles, risk scores, connections, and TTP analysis to identify when IOCs are likely associated with already-identified actor groups. This additional context enables defenders to make faster decisions or to build rules around specific indicators or attributes that can help categorize, prioritize, or automate alert response.
The Incident Response Battle Strategy
Automation plays an important role in helping the security professional with prioritizing. Organizations are adding new tools to their stack such as SIEM and Security Orchestration, Automation, and Response (SOAR) solutions. A SIEM solution improves efficiency by providing a system to view all the security log data from many hosts. A SOAR solution assists security teams in investigating and responding to threats faster by way of automating detection, investigation, and response capabilities and carrying out response actions at machine speed—reducing threat dwell time and decreasing their mean time to remediation (MTTR).
Security professionals often leverage various frameworks that are considered best practices such as NIST, ISO, PCI/DSS, SOX, HiTrust, etc. If we take a framework-agnostic approach, there are really 4 phases that are the meat and potatoes of incident response processes: preparation, triage, remediation, and containment. Adopting threat intelligence enhances incident response in triaging and containing threats when combined with SIEM and SOAR solutions.
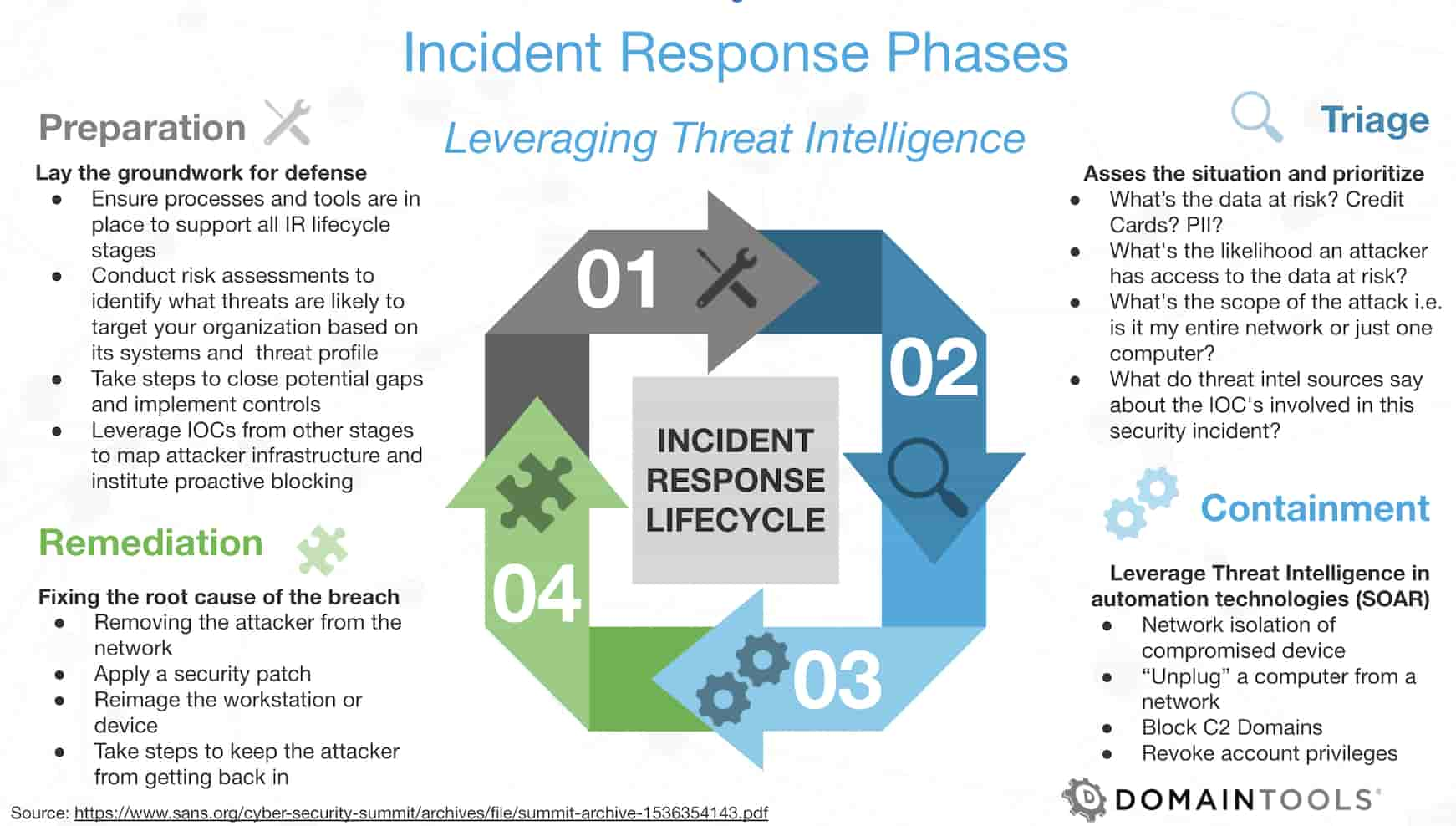
There should always be preparation to lay the groundwork for the defense. And you should never stop preparing. Preparation should be constant and should leverage the ongoing experiences of your incident response and network defense teams to ensure that you’re instituting a cycle of constant improvement. The preparation phase sets the incident response lifecycle up for success by conducting risk assessments, closing gaps, and implementing controls. Planning ahead to identify what threats are likely to target your organization based on its systems or leveraging IOCs from other stages in previously detected attacks to map attacker infrastructure and institute proactive blocking can help incident responders stay ahead of the game.
In the triage phase, assessing the situation and prioritizing—in the way a proverbial battlefield medic would—is key to an effective response. To extend the metaphor, the battlefield medic needs to quickly assess the situation based on initial, observable attributes to discover what the issue is and what needs to be done in the early stages. Our triager can leverage threat intelligence, risk scoring technology, and threat profile information to help with their assessment within their SIEM or SOAR solutions. The more information someone has up front, the faster and more effectively they can make a decision about next steps.
In the containment phase, a security analyst can combine threat intelligence and automation technologies, and these automated playbooks can kick off certain aspects of this process. A good example is if our metaphoric triager identifies there’s a malware outbreak on the network, they can apply strategies to quarantine or isolate infected machines or systems. In this scenario, our battlefield medic needs to stop the bleeding.
At the remediation stage—or now that the patient is stabilized—our soldier has to switch from a triage mindset to investigate the issue further, addressing the root cause of the incident by getting the attacker out of the network and then closing holes that allowed the attackers access in the first place (e.g., reimaging workstations or devices, applying security patches, etc.).
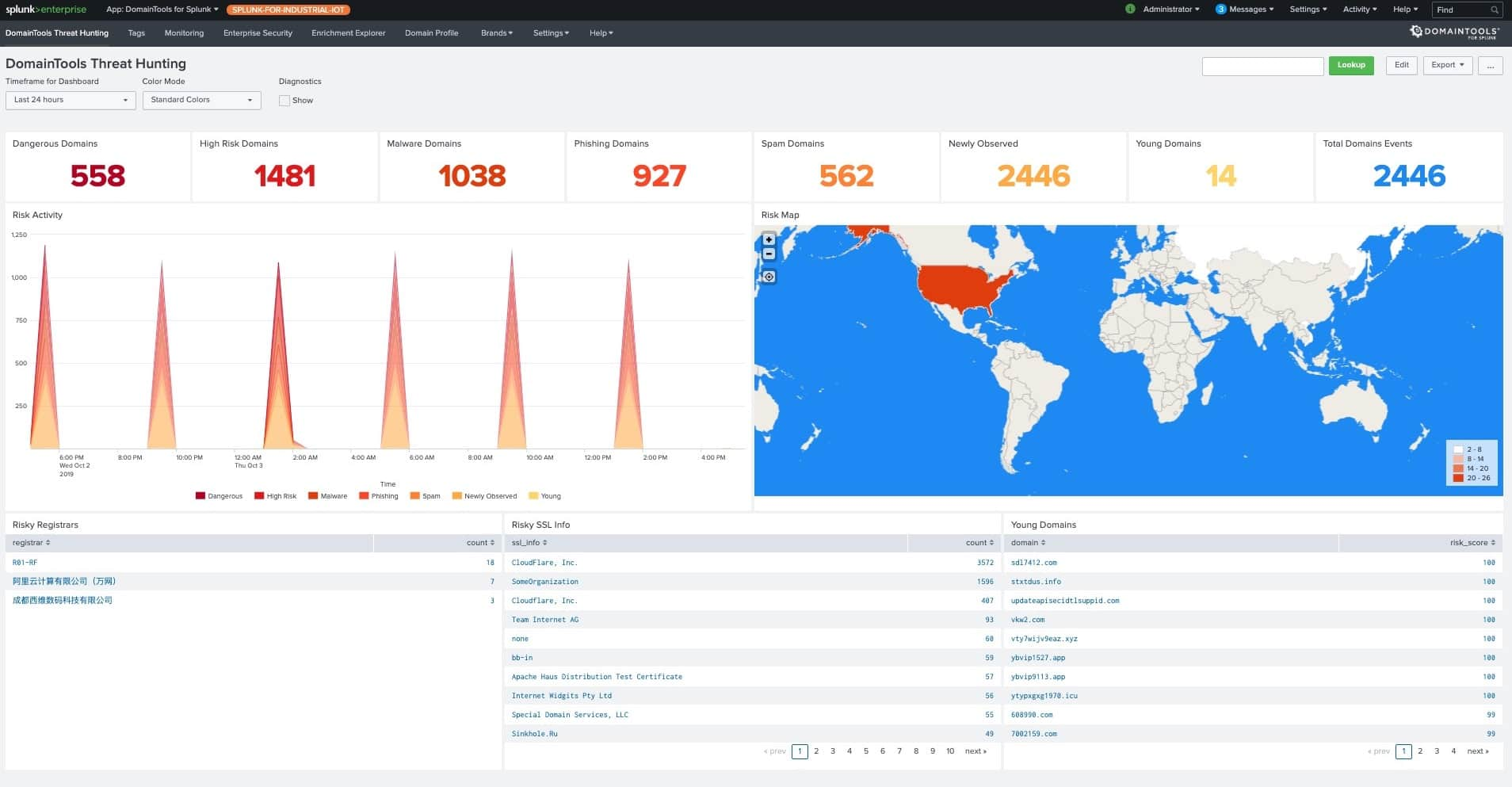
Solutions in Action: Alerting with threat intelligence in a SIEM
By combining threat intelligence with automation via SIEM platforms, incident responders can enrich indicators from their log files and fire off alerts and notable events when high-risk domains are detected or when activity patterns reach certain thresholds. Here’s a view of the DomainTools App for Splunk that highlights log file events related to domains with high risk scores or that fit the profile of domains used for Phishing, Malware, or Spam attacks. Consider how implementing tools like these can help your incident response team contextualize attacks and make more accurate decisions faster.
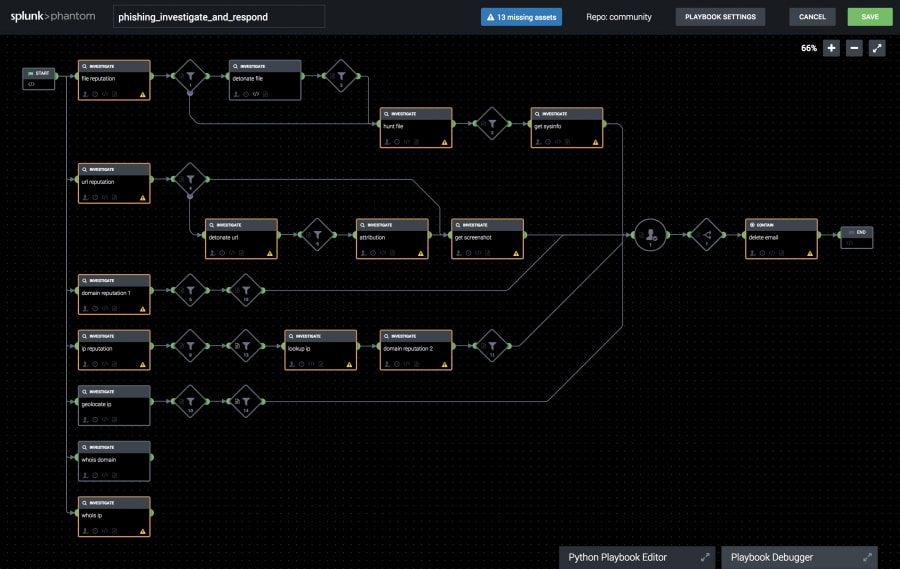
Solutions in Action: Threat intelligence in SOAR automation
Automating incident response elements improves efficiency. By using threat intelligence to structure rules and using risk indicators or the presence of connected infrastructure as decision points for executing automated actions and pivots, organizations can better support analyst teams by automating as much of the investigation as possible—leaving their senior security specialists to focus on the work that definitely requires human expertise.
Here’s an example of an incident response process mapped out in a SOAR tool (Splunk Phantom) that leverages DomainTools’ threat intelligence, including risk scores and connected infrastructure counts, to help automatically investigate and identify threat-delivering infrastructure and make determinations on next steps.
Know more. Thwart More.
Intelligence is key to enabling security teams to anticipate threats, respond to attacks more quickly, and make smarter, more informed decisions on how to reduce risk. Threat intelligence can be applied to incident response procedures and enable an organization to have a more proactive strategy that magnifies the effectiveness of security teams and security solutions by predicting unknown threats and streamlining processes to make better use of human resources.
Learn more about DomainTools Threat Intelligence for SIEM solutions




