Inside the Murky World of HMRC Phishing Campaigns
NOTE: Iris Detect has supplanted PhishEye, with dramatically expanded capabilities. Please explore Detect for your brand protection, anti-fraud, and spoof infrastructure analysis needs.
DomainTools identifies malicious campaigns targeting HMRC and other organizations with the intent of capturing PII
When people in the UK think of phishing scams, there’s a fair chance that the ones they are thinking about look something like this:

This is a phishing email which claims to be from HMRC (Her Majesty’s Revenue and Customs), the non-governmental department responsible for collecting taxes. Last year, the Guardian reported that thousands of university students were targeted with fake tax fraud emails in order to steal banking and personal information. The tax authority received thousands of reports over the weeks leading up to the deadline. This is a common practice during tax season, whether it’s the HMRC, or the IRS, these fraudulent campaigns pose a major risk for both individuals and organizations.
We used our PhishEye and Iris products to perform analysis of the top 30 domains spoofing HMRC (as defined by their Domain Risk Score). In doing so, we were able to establish the country of origin associated with the domain. The results revealed that China dominated the most successful HMRC phishing scams, with a third of the most dangerous phishing campaigns originating there. Canada, the USA and the UK provided 2 each, and Brazil, New Zealand and Panama each provided the home of one domain. 10 out of the 30 most dangerous domains had no registered country of origin.
However, the most interesting data was uncovered when we used the Pivot pane to study two of these high-risk domains to explore where they fit into the cybercrime ecosystem.
Example 1: hmrc-refund.co[.]uk
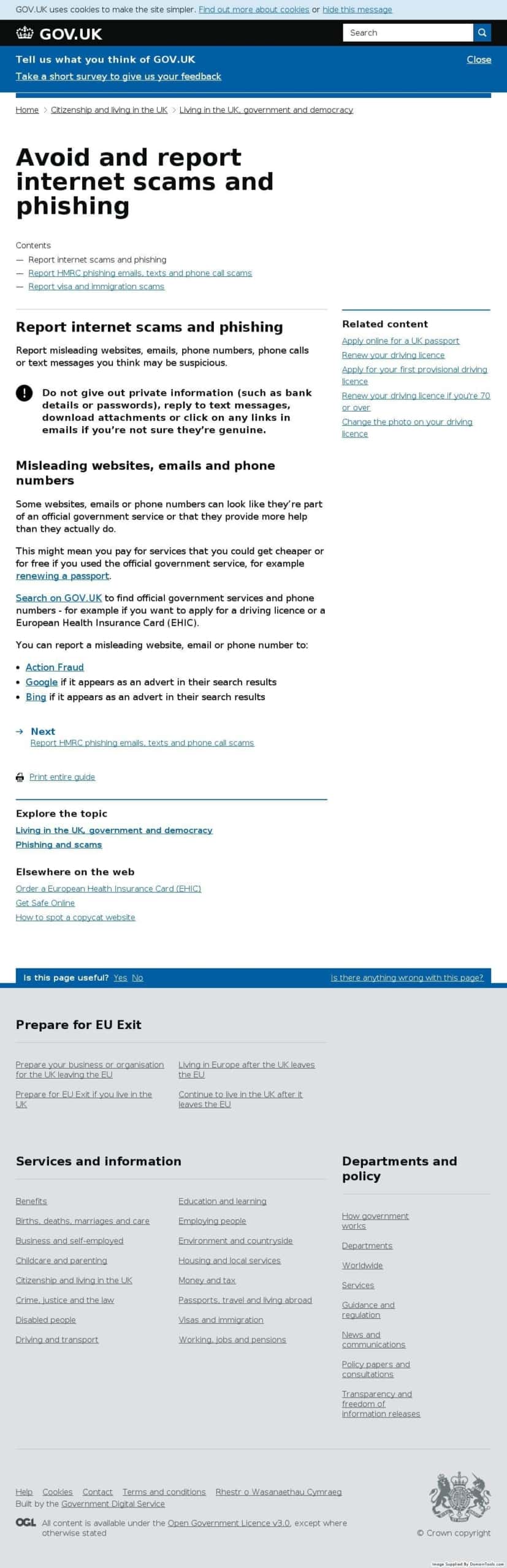
This domain is an example of how a lot of HMRC scammers develop campaigns; They register a domain such as the one above with the purpose of sending fraudulent emails tricking individuals into thinking HMRC have been in contact to issue them with a tax rebate. (it is worth consumers bearing in mind such tax corrections will always be sent via the post).
This domain is one of many registered by the scammer. The single pivot performed in our Iris tool showed that 108 domains shared the registered contact name, which was HM Revenue & Customs.
Of these domains, 6 have already been added to industry blocklists, and a further 6 have been assigned an overall Domain Risk Score of 70+ by DomainTools, meaning they are potentially malicious sites, mimicking behavior of phishing, malware, or spam. This can indicate that the individual/group who created these domains is currently engaged in successful phishing campaigns on an industrial scale.
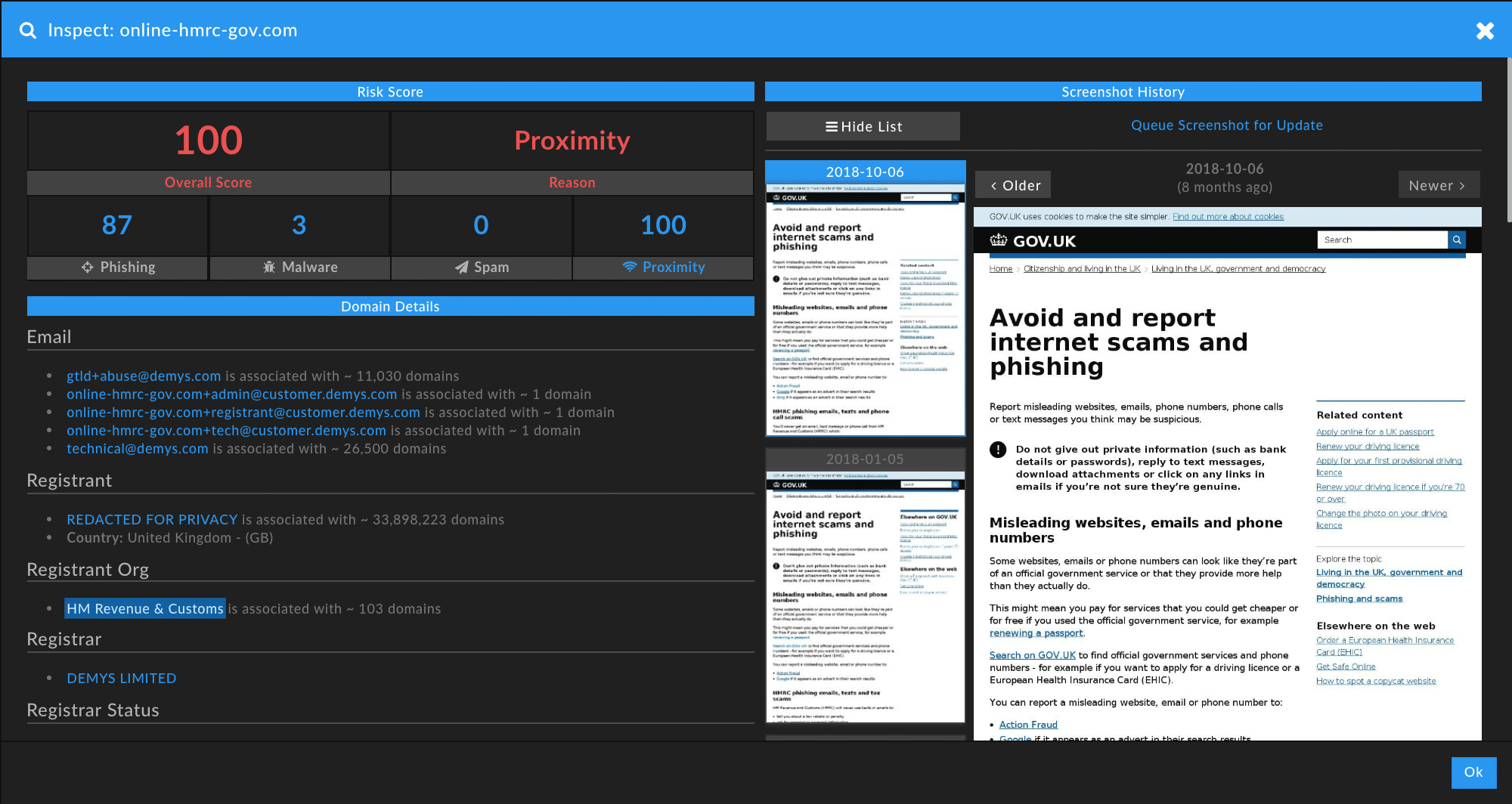
Example 2: hmrc-gov-deptukonl[.]org
By taking a deep dive into the listed information on this domain, we were able to identify a plethora of information about where it fits into the wider phishing landscape. Performing a guided pivot which showed us other domains registered to this IP address (188.215.92.10) we were able to establish 353 domains with the same IP address. Of these domains, we found 36 had already been added to industry blocklists, and 80 domains with an overall Domain Risk Score of 70+, meaning that because of their association to know malicious domains, they are potentially being used for phishing, malware, or spam.
What is most interesting about these domains however is that the addresses indicate that the individual/group responsible is spoofing a wide variety of organizations, with HMRC as just one facet of the cybercrime network he has built up. Other domains registered to this IP address include:
- navyfederalbankcreditunion[.] org – Now on industry blocklists
- googleservlces[.]com – Now backlisted
- alldisabledchildcaresupport[.]com – Showing a Domain Risk Score of 96 (71 for Phishing and 96 for malware, specifically)
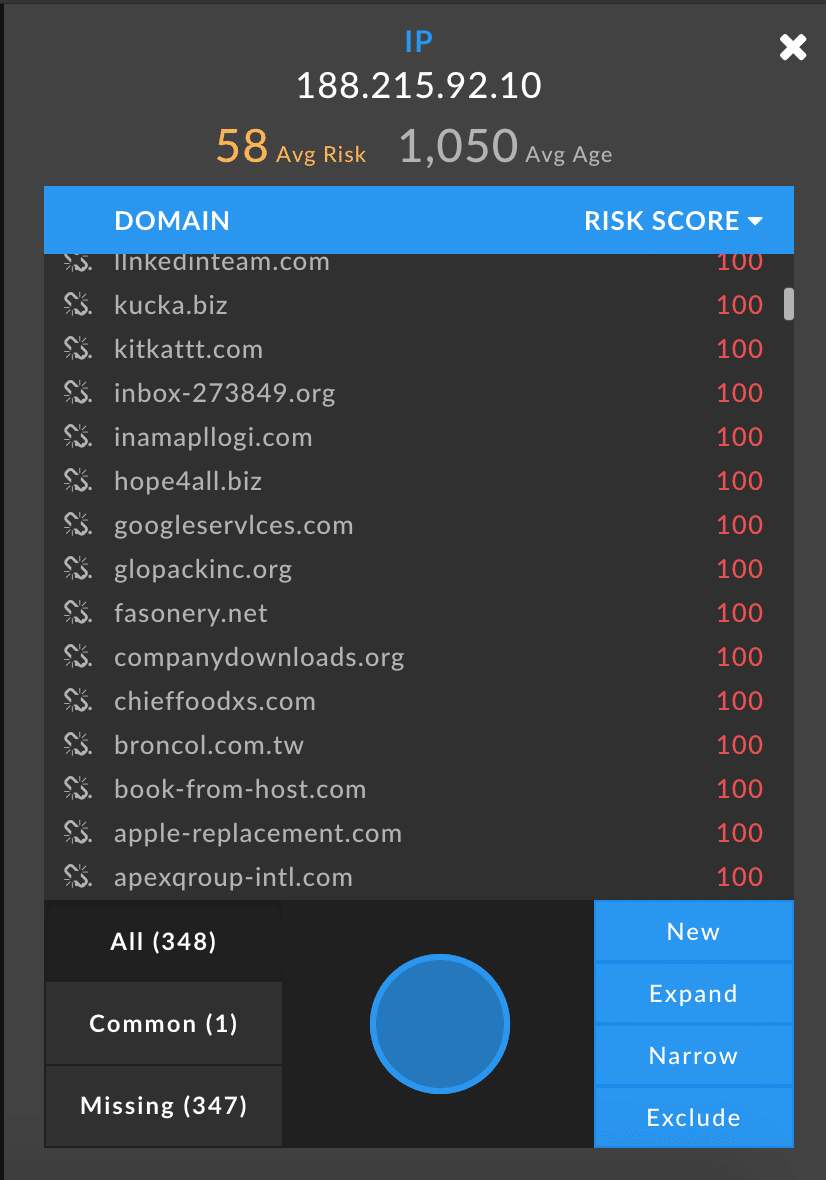
When pivoting on the Registrant Organization, we see similar results. There were 370 domains associated with the Registrant Organization. Of these, 35 are on industry blocklists, and 55 have a Domain Risk Score of 70+. Similarly, we see examples of other organizations being phished from this IP address as well as HMRC-spoofing domains:
- rbcbanksaving[.]com – Now on industry blocklists
- fidelitystrustplc[.]com – Now on industry blocklists
- craigslists-trading[.]com – Now on industry blocklists
- fedx-onlne[.]com – Showing a Domain Risk Score of 91 (91 for Phishing and 79 for Malware, specifically)
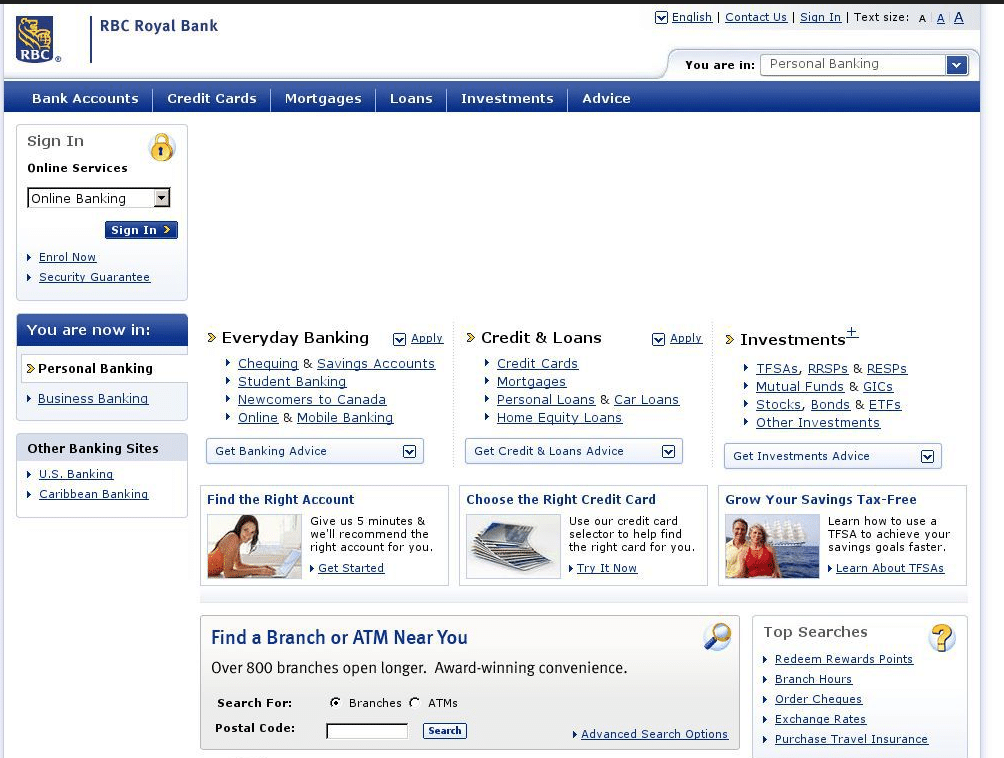
rbcbanksaving[.]com screenshot from 04/17/2016
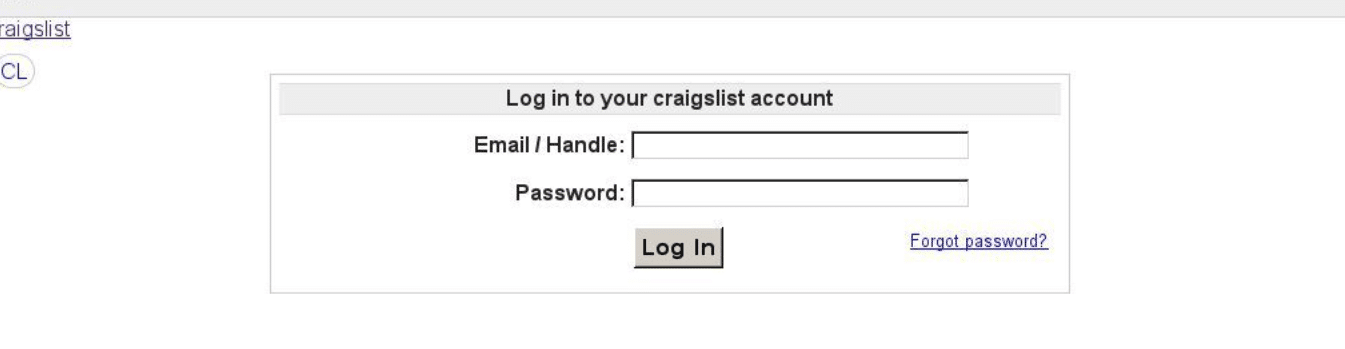
craigslists-trading[.]com screenshot from 5/23/2016
What does this all mean?
Firstly, it’s important to place these scams in a global context. We identified a similarly complex and multi-faceted network of scams last August targeting taxpayers in the United States via IRS phishing scams, some of which overlapped with corresponding HMRC domain scams.
In short, this proves that cybercrime is no different to other criminal activities; The bigger the better. The cybercriminals who run these scam websites may themselves not be part of larger cybercrime gangs or organizations, but the networks of malicious websites they have built mean they do not necessarily have to be – The ease with which phishing websites can be built, and the step-by-step guides available on the dark web as to how to carry out phishing campaigns mean that even relative amateurs can create vast networks of fraudulent websites. If one of these websites is already on one or more industry blacklists, as we have seen above, there are still hundreds of others attempting to phish unwitting customers of some of the world’s largest brands and organizations. While HMRC scams are certainly the most visible scams in the UK, the tentacles of these cybercriminals spread much, much further.




