The Perfect Pair: Integrating DomainTools Data Sets in Microsoft’s Sentinel SIEM Product
The Power of World-Class Passive DNS for SIEM
What happens when you add world-class passive DNS and domain registration data to one of the leading SIEM platforms? Interesting incident response (IR) and hunting use cases are unlocked! Today, we are happy to announce the integration of the DomainTools Iris Investigate and Farsight DNSDB data sets in Microsoft’s Sentinel SIEM product. Microsoft Sentinel is a popular platform, so it’s a natural fit. This integration will afford Sentinel users new capabilities for enrichment of events raised in Sentinel.
Iris Platform Workflows and Playbooks
There are several playbooks that make use of Iris data in Microsoft Sentinel Incidents. When an Iris Enrich Domain playbook is invoked, it retrieves all the Domain objects in the Incident, and then iterates through the Domain objects and fetches the results from DomainTools Iris Enrich for each domain. From this, all the details about the domain are added as comments in a tabular format. Iris Enrich is designed for high-volume, machine-scale enrichment. At the human-scale end of things, the Iris Investigate Domain playbook (and similar URL playbook) is comparable in data output, but in addition to the enriching datapoints themselves, the response includes attributes that have an analytically-useful number of connected domains (between 200 and 400), and link to the DomainTools Iris Investigate UI, so you can carry out further investigation.
But wait—you’d like the system to do some of that for you? No problem! The Iris Investigate Guided Pivots playbook does the same actions described above, but it also returns all of the domains (with risk scores) identified as first-order connections to the domain(s) originally identified in the Incident. The below screenshot gives a sense of what this looks like: the playbook has returned all of the domains connected to a specific SSL certificate hash, while the hash itself was connected to a domain raised in an Incident.
Here’s a list of additional Iris Investigate-based playbooks:
- Domain Risk Score Playbook – Given a domain or set of domains associated with an incident, return the risk scores and adjust the severity of the incident if a high risk domain is observed. Add the risk scoring details in the comments of the incident.
- Malicious Tags Playbook – Track the activities of malicious actors using the Iris Investigate UI, tagging domains of interest. Given a domain or set of domains associated with an incident, query Iris Investigate for information on those domains, and if a specified set of tags is observed, mark the incident as “severe” in Sentinel and add a comment.
- URL Playbook – Given a URL or set of URLs associated with an incident, return all DomainTools Iris Investigate data for the extracted domains from the URL as comments in the incident.
- Iris Investigate With Farsight pDNS Playbook – Given a domain or set of domains associated with an incident, enrich the domain using the DomainTools Iris Investigate API, returning whois and infrastructure details. Subsequently retrieve associated subdomains from passive DNS information seen in Farsight’s DNSDB. Farsight DNSDB API subscription required
These playbooks are only suggested workflows, and can be easily modified within Microsoft Sentinel’s logic app editor to suit your needs.
Farsight DNSDB playbooks
That last item above referred to Farsight DNSDB—but it’s not the only way to leverage this dataset. With the Microsoft Sentinel App for Farsight DNSDB’s playbooks, an investigator can answer questions such as “where did this domain previously resolve,” or “what other domains share hosting with this domain?” Such information can be extremely valuable when trying to correlate events that may otherwise show no relationship to each other. For example, a traffic flow to an IP address that is not currently associated with a malicious domain, but where that domain did previously reside, could be an indication of harmful activity such as command and control callbacks, malware downloader traffic, or other threats. You can see this by running the DNSDB_Historical_Address playbook. Likewise, if your DNS logs contain lookups for other domains that you know to be co-hosted with a known-bad domain, then you may have threat traffic to investigate. The DNSDB_Co_Located_Hosts playbook enables this.
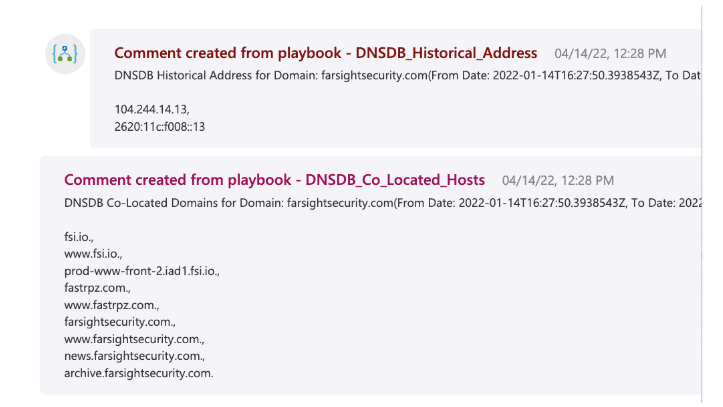
The various actions supported in the DNSDB integration enable you to probe the industry’s leading passive DNS database to develop insights around additional adversary assets beyond those that might have been observed in previous traffic flows to or from your protected environment. This can help uncover dormant infrastructure that could be activated by adversaries for future campaigns, or future stages of campaigns in progress.
Give them a try!
If you are a user of Microsoft Sentinel, we hope you’ll take a look at these integrations. Developing deeper context around adversary assets is essential to many network defense, incident response, and threat hunting workflows.
DomainTools Iris Investigate and Farsight DNSDB on the Microsoft Marketplace
If you don’t already have access to the Iris Investigate, Iris Enrich (optional, enables higher-volume lookups), or Farsight DNSDB APIs, please contact your account manager and we’ll help you get connected!