New COF2MISP import module for MISP enables Threat Hunters to improve Cybersecurity Investigations
Farsight Security, Inc. and MISP, Open Source Threat Intelligence Platform, have developed a COF2MISP import module to import DNSDB Passive DNS data in Common Output Format (COF) into MISP. The author of the new MISP module is Aaron Kaplan.
To utilise this module, you will need to install it if not already. For that, please, follow the steps in MISP Documentation.
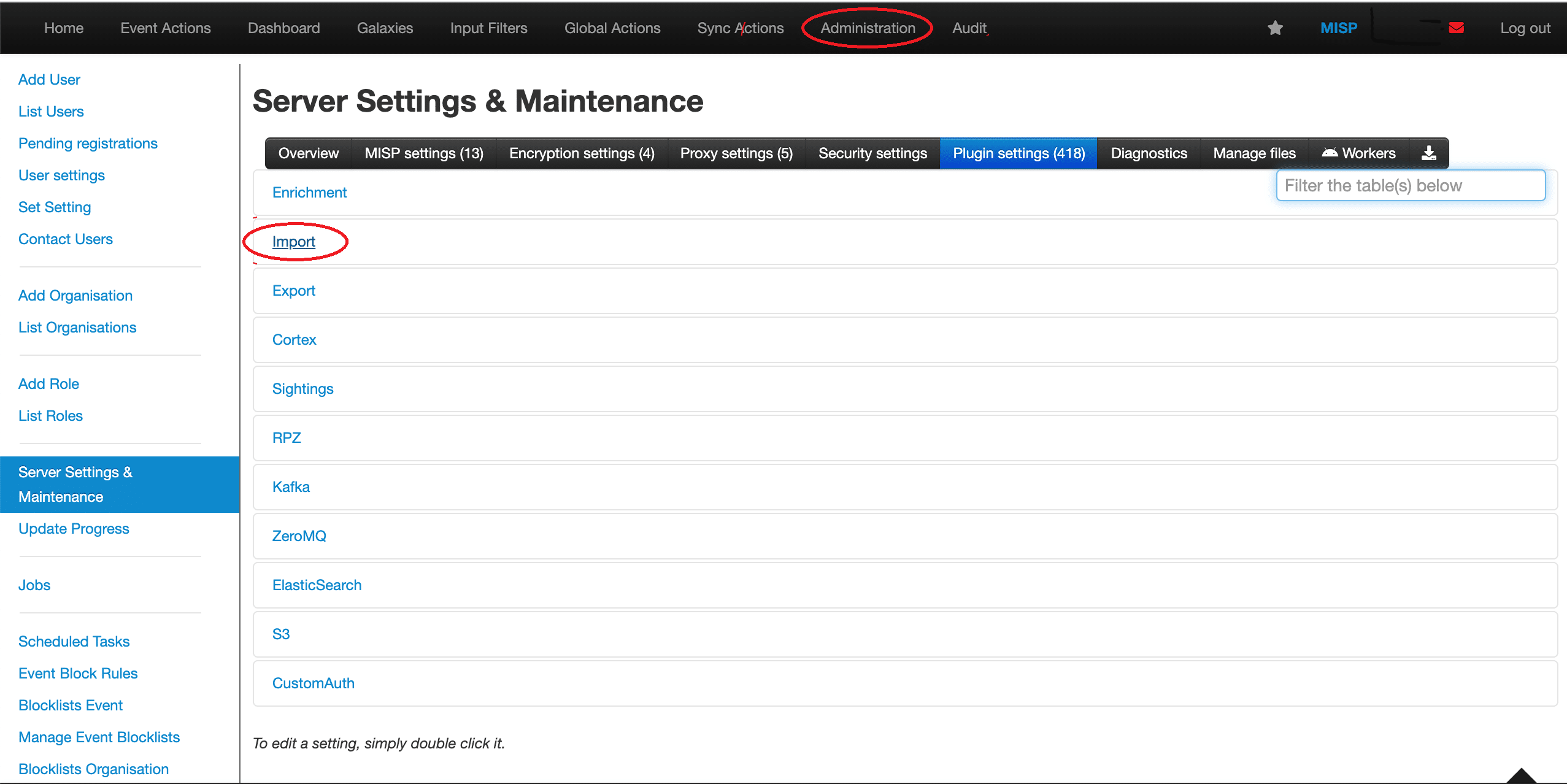
The next step you would need to do is to enable the module via MISP GUI Administration > Server Settings & Maintenance > Plugin settings > Import:
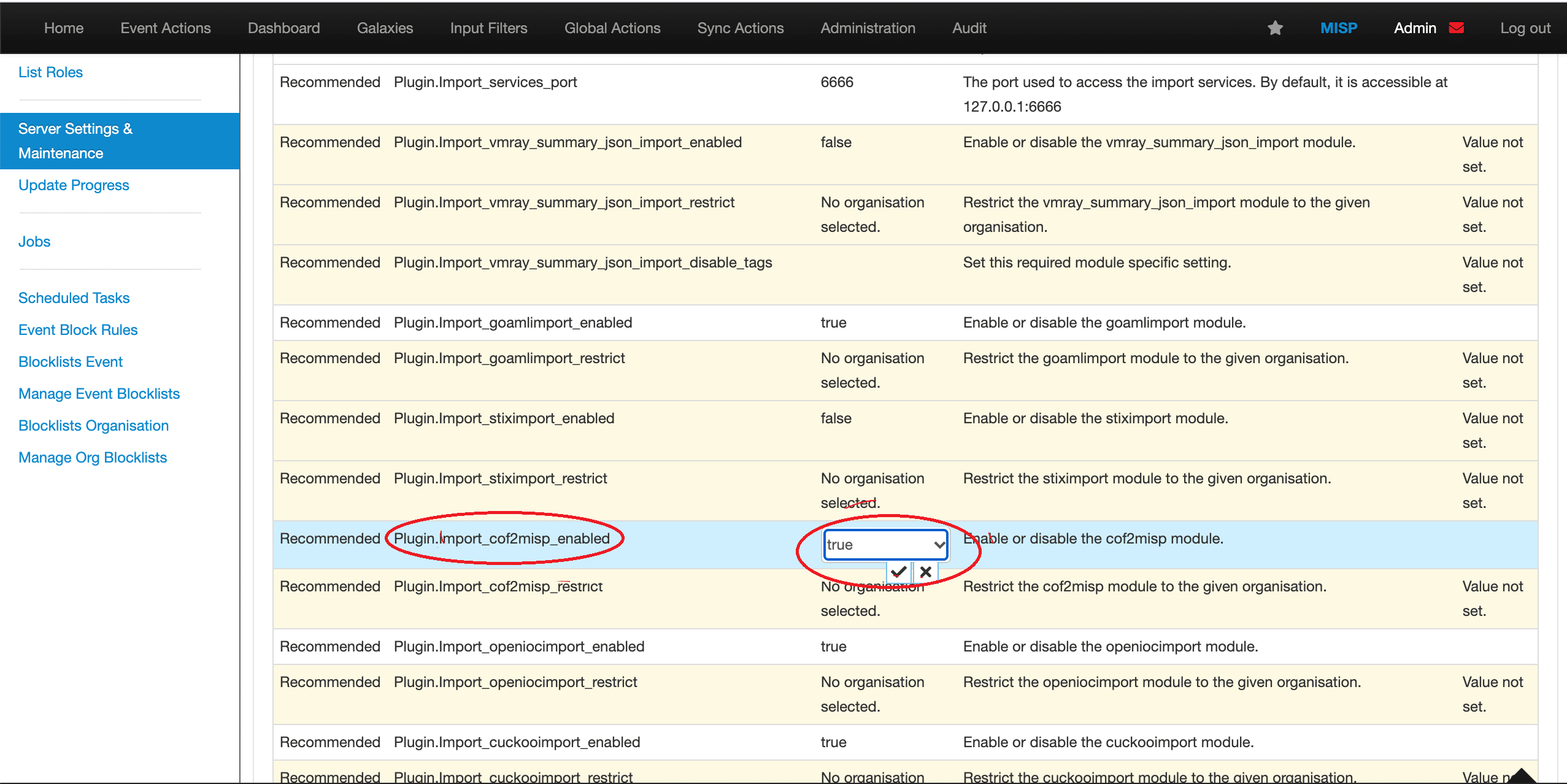
After this initial setup, the module will become available for import your data collected and saved after pivoting in e.g. Farsight DNSDB Scout or Farsight dnsdbq and dnsdbflex CLI tools to query Farsight DNSDB.
Let’s first prepare data for this exercise.
Assume, we are interested in potential phishing sites attacking Western Union in the last 7 days. First, we will construct a flexible search regex query searching for host names that start with westernunion.com, but exclude those that end with westernunion.com (i.e. the resources that potentially try to pretend to be the Western Union proper):
$ dnsdbflex --regex '^westernunion\.com\.' --exclude '(^|\.)westernunion\.com\.$' -A7d | egrep '"A"|"AAAA"|"CNAME"' | jq -r '.rrname' | sort -u | head westernunion.com.00d00000000hduyeai.live.zalando.com. westernunion.com.acronis.com.tw. westernunion.com.adobeaemcloud.com. westernunion.com.au. westernunion.com.au.cutercounter.com. westernunion.com.br. westernunion.com.co. westernunion.com.d1.sc.omtrdc.net. westernunion.com.dwl.dnswl.org. westernunion.com.fi.
Once we see, the resources do exist, we run the results of the previous search via a standard DNSDB query:
$ dnsdbflex --regex '^westernunion\.com\.' --exclude '(^|\.)westernunion\.com\.$' -A7d -F | egrep '/A|/AAAA|/CNAME' | dnsdbq -fmSj -A7d | head -n2
{"count":1,"time_first":1619984856,"time_last":1619984856,"rrname":"westernunion.com.apartmentjet.com.","rrtype":"CNAME","bailiwick":"apartmentjet.com.","rdata":["redirect2.homeaway.com."]}
{"count":1,"time_first":1619965497,"time_last":1619965497,"rrname":"westernunion.com.vk.me.","rrtype":"A","bailiwick":"vk.me.","rdata":["87.240.129.187","87.240.190.64"]}
The full results we save in the file to later export to MISP for further investigation:
$ dnsdbflex --regex '^westernunion\.com\.' --exclude '(^|\.)westernunion\.com\.$' -A7d -F | egrep '/A|/AAAA|/CNAME' | dnsdbq -fmSj -A7d > westernunion.json
Note: the same queries can be made using Scout, however it will take much longer to execute due to manual process.
Now, once we have the westernunion.json file in COF format, we can import it to MISP.
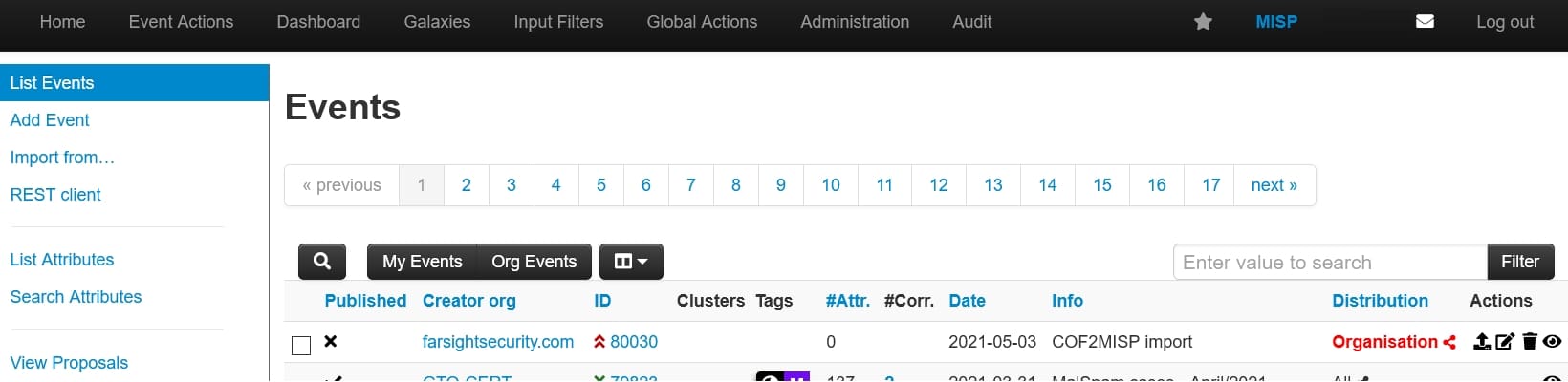
To use the module, open the desired event and chose “Populate from…”:
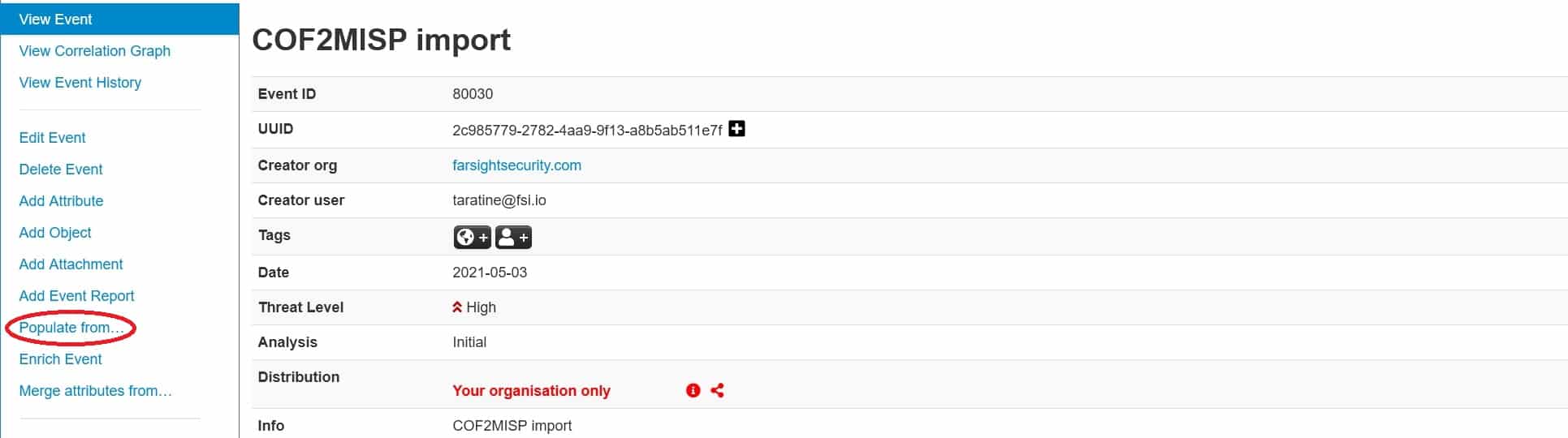
In the pop-up window, chose and click on Cof2misp import module:
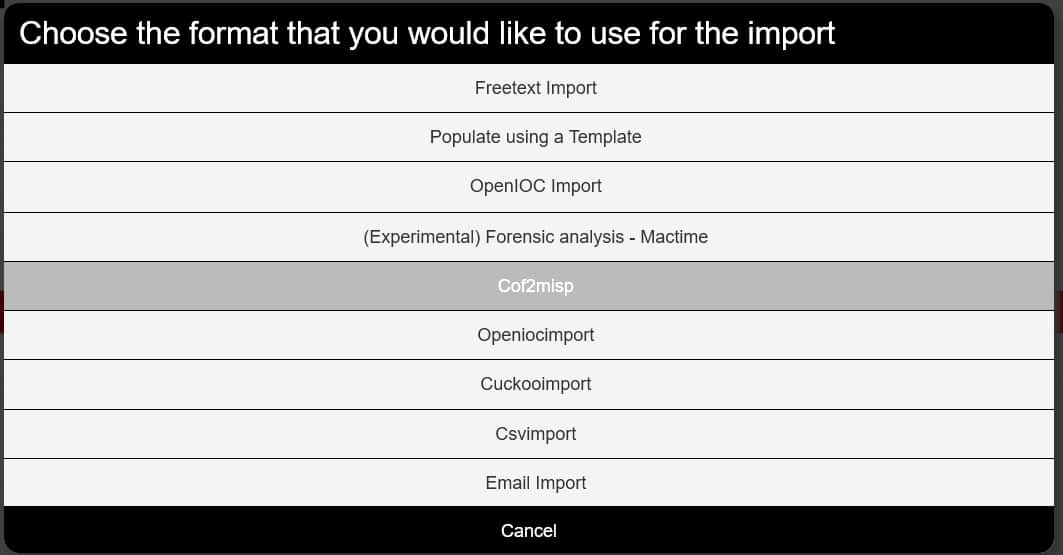
The module will be activated, and you will see a dialogue to select the data file to import:
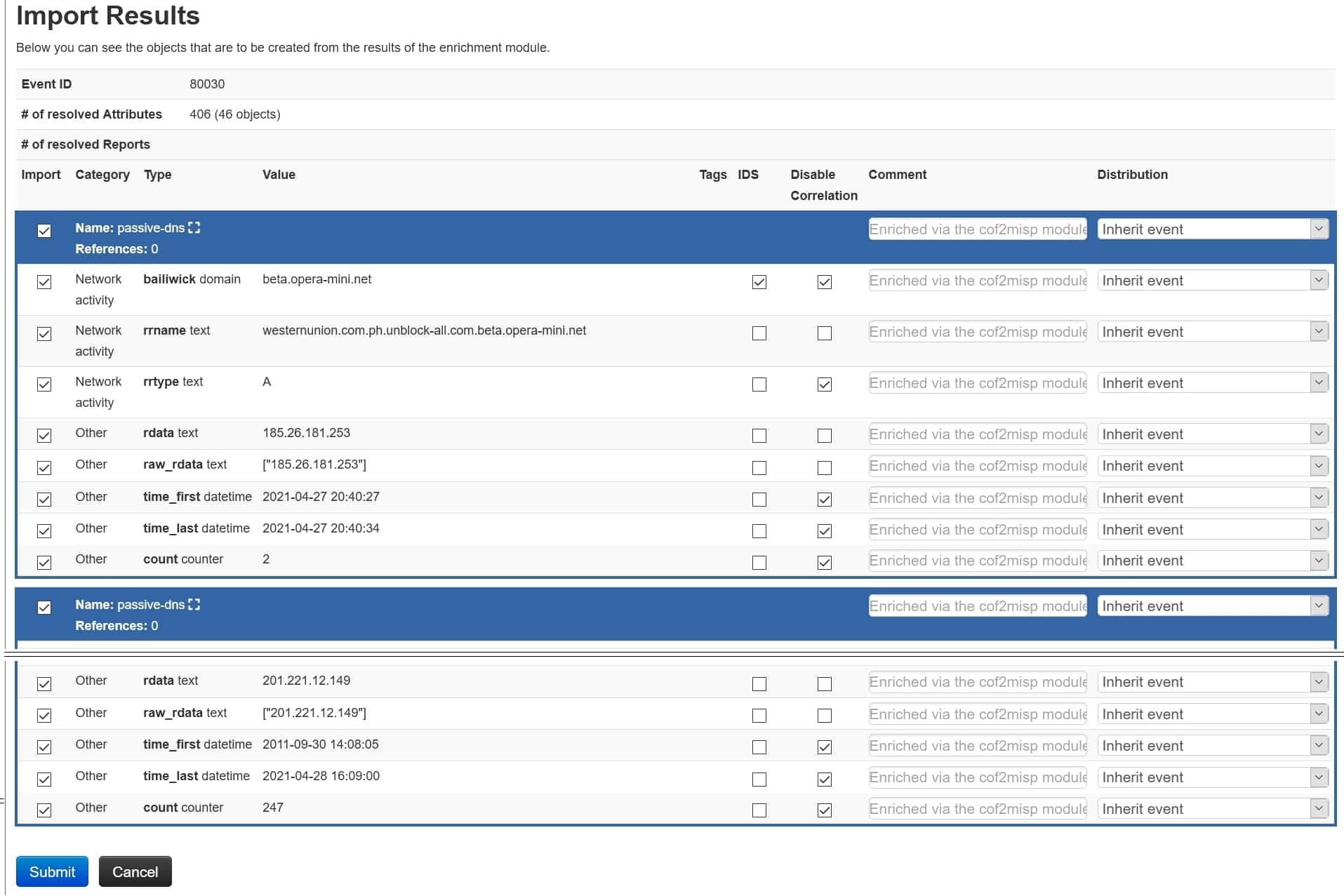
Upon review, you can submit the results by clicking on the Submit button at the bottom of the screen.
Once submitted, the results will appear attached to the event:
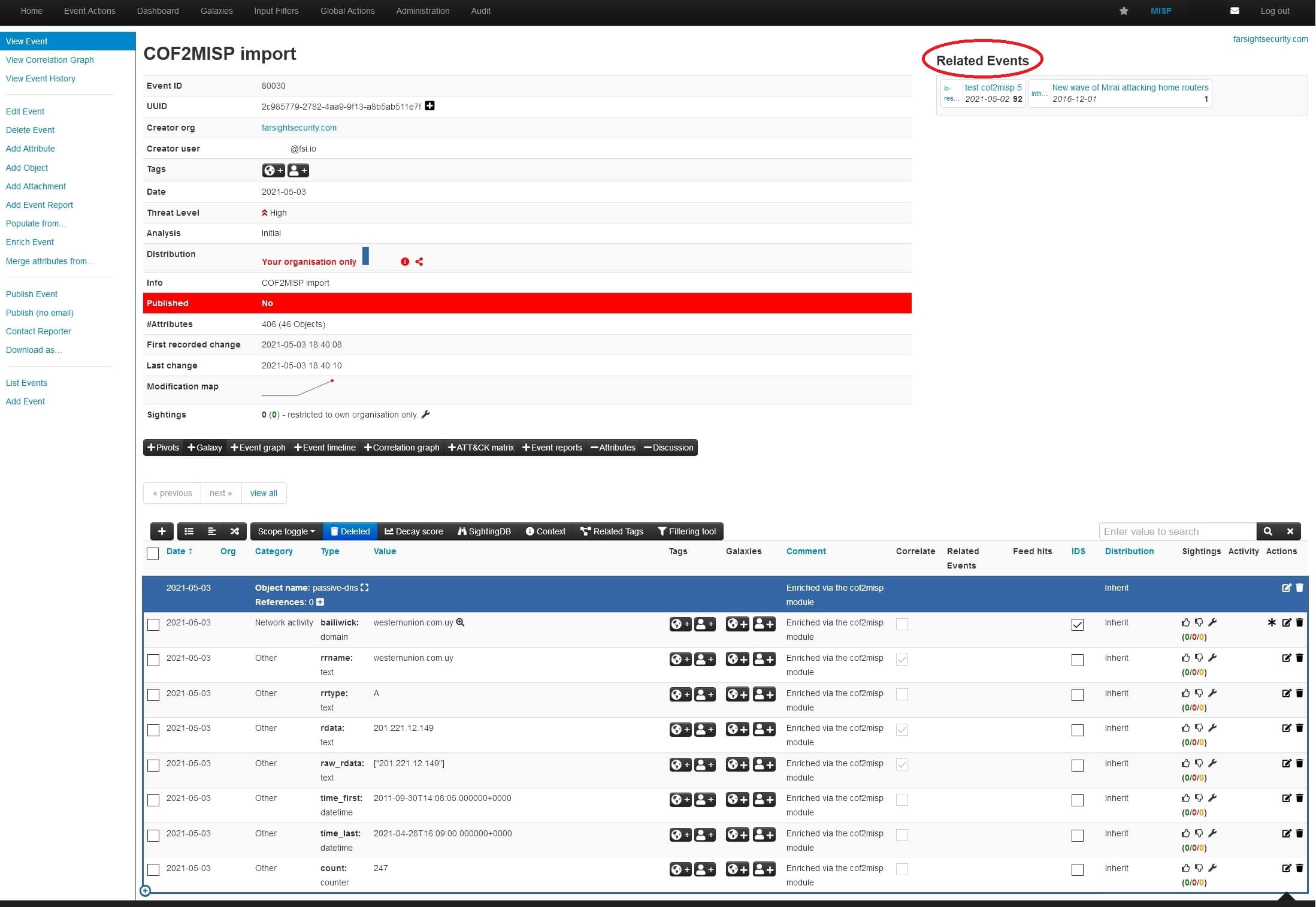
Note: in the top right corner MISP will present “Related Events” through powerful internal MISP correlation module.
You may elect to share these results across the MISP platform within your Farsight License agreement for further investigations and collaboration.
We, at Farsight, plan to get closer involved into further improvement of the modules to ensure the full power of the DNSDB API v.2 and Flexible Search capability is fully unleashed to the MISP community of the World-Wide defenders.
Farsight DNSDB is the world’s largest historical passive DNS database, with more than 100 Billion DNS records dating back to 2010.
MISP, Open Source Threat Intelligence Platform, is helping information sharing of threat intelligence including cybersecurity indicators. MISP modules are autonomous modules that can be used for expansion and other services in MISP.
Let’s together make the internet a safer place for everyone.
Boris Taratine is a Principle Architect for Farsight Security, Inc..
Alexandre Dulaunoy is a Security Researcher for the CIRCL – MISP Project.
Christian Studer is a Security Researcher for the CIRCL – MISP Project.