Phishmas Comes Early: New Developments in USPS Smishing Attacks
Share this entry
Executive Summary
- Phishing attacks to gather personal information attributed to the threat actor Chenlun/Sinkinto01 have continued after our original investigation in December of 2023.
- After analyzing related domains, I’ve noticed interesting evolutions in their tactics, techniques, and procedures.
- Chenlun has expanded to use Amazon lures in addition to the previously identified United States Postal Office (USPS) lures.
- Our domain-related data allowed us to identify a preference of using subdomains with short life-cycles on older apex-level domains.
- Both subdomains and apex-level domains used indicate the use of a domain generation algorithm (DGA) as a method of obfuscation.
- I’ve identified the use of redirect domains used after visiting the domain mentioned in the SMS message to further obfuscate the path traveled by the victim before being asked for personal information.
Introduction
Last year, DomainTools published research on a phishing campaign that targeted individuals by using SMS messages to impersonate the USPS. The original article provides details on likely responsible threat actor Chenlun/Sinkinto01. Apparently, the holiday season arrived early for me this year and I may have Chenlun to thank. In one year’s time, some of their gift giving techniques have evolved.
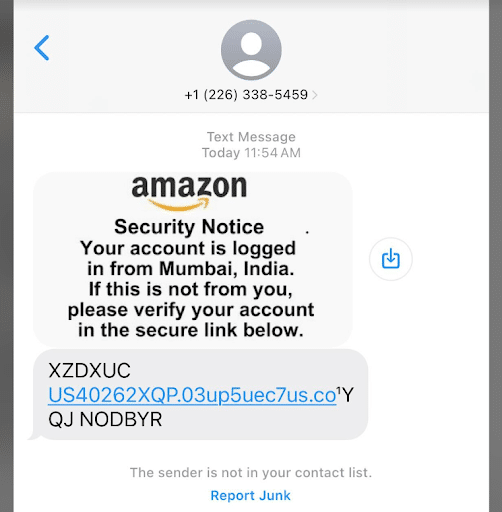
A Brief History of the 2023 USPS Smishing Attacks
The original article from December 2023 highlights a surge in phishing attacks, specifically smishing (SMS phishing), aimed at USPS customers. These attacks exploited the increased volume of holiday deliveries to deceive recipients into visiting malicious links with the primary goal of harvesting peoples’ private information.
The attackers used convincing tactics, such as cloning legitimate USPS pages and sending fake delivery notifications via SMS. When victims input their personal information it would ultimately be sent to a Telegram account controlled by the attackers.
The campaign was notable for its scale and sophistication, making it one of the more impressive phishing efforts seen at the time. DomainTools predicted that due to the large volume and comparably high success rate these phishes generated, other threat actors in eastern Asia and elsewhere were likely to follow.
Use of Subdomains and Domain Generation Algorithms in USPS Smishing Attacks
I used Iris Investigate to look up the apex-level domain, 03up5uec7us[.]co, which is associated with the latest smishing attempt shown in the screenshot above. The domain has a high Domain Risk Score, predicting its likely malicious use. It was also connected to about a dozen other domains with a similar naming scheme through its Website Title.
While looking at the cluster of connected domains I noticed two familiar looking aliases, Matt Kikabi and Mate Kika. Last year’s article identified Matt Kika as a likely alias used in the campaign. Furthermore, the same phone number contained in the email address for Matt Kika was used as the phone number in domains registered by Matt Kikabi and Mate Kika.
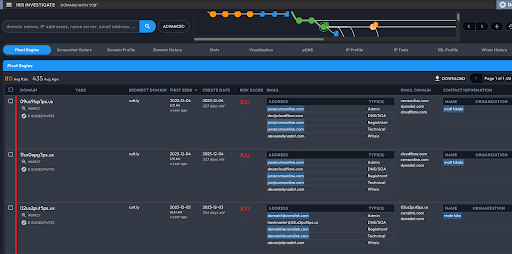
I then found over 700 domains pivoting off the same phone number, 19296258844. Despite creation dates of ten months or more, subdomain activity continued through to the week of writing. Additionally, a large majority of these domains and their associated subdomains seemed to be generated by a DGA with at least two common patterns.
Regex 1:
^us.*\.[[:digit:]]{2}(us|up).*(us|ps)\.(us|co)\.$
Regex 2:
^[[:alnum:]]{8}-[[:alnum:]]{4}-[[:alnum:]]{4}-[[:alnum:]]{4}-[[:alnum:]]{12}\.random\.[[:digit:]]{2}u.*\.us\.$
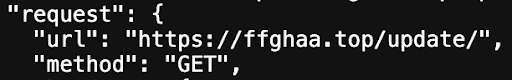
Using a regular expression to search for domains matching these patterns, I queried against our passive DNS database using DNSDB Scout and uncovered subdomains that were last seen in the wild within the last 24hrs from the time of this writing. Upon further investigation one of these domains, 4d9b3981-60e7-40a9-810c-792c7925adc3.random.01up4zpe8us[.]co, redirected to ffghaa[.]top/update/.
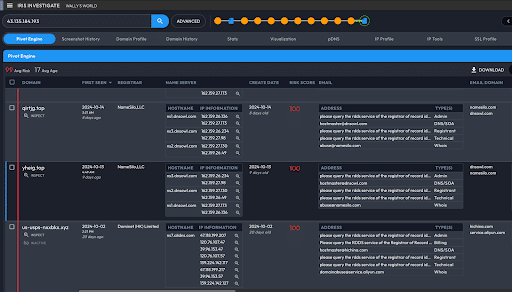
The ffghaa[.]top domain is much younger (first seen in DNS on 10-15-2024) and through Iris Investigate I pivoted on its IP address, 43[.]135.184.193, to find 90 connected domains first seen in DNS within the last month.
An interesting pattern emerged within that cluster. Those first seen in DNS on 10-2-2024 began with the substring “us-usps,” have a Domain Risk Score of 100, and have not had resolutions observed in DNS in at least 10 days. The second subset of domains using the same IP address first seen since 10-13-2024 abandoned the “us-usps” substring, changed registrars from Dominet (HK) Limited to NameSilo,LLC, and changed their name server provider from Alibaba Cloud’s DNS service (AliDNS) to DNSOwl’s service.
Key Differences From Original Findings
DomainTools attributes these new domains to Chenlun with medium to high confidence. In addition to the activities from last year, DomainTools recommends monitoring for these new associated TTPs:
- Prompting targets to verify Amazon account access after warning of suspicious activity.
- Use of a DGA to further obfuscate subdomains and apex domains.
- Removal of brand names from their subdomains and apex domains.
- Reuse and expansion of information used with several aliases.
- Expansion of email domains to csmslink[.]com, which is associated with the same SMS integration platform known to be located in Shenzhen.
- More recent subdomain activity on old apex domains.
- Subdomains ultimately redirect to young apex domains with only alphabetic characters, NameSilo,LLC as registrar, and DNSOwl for name server provider.
Mitigation Strategies
- Use domain-related data to find connections and gain a deeper understanding of domains related to a specific attack.
- By analyzing domain-related data, you can identify patterns in attackers’ preferences and tendencies to uncover related infrastructure from the past, present, and future.
- Collaborate with other organizations and industry groups to share information about phishing threats and mitigation strategies.
Conclusion
Chenlun has continued to be a serious phishing player and they don’t seem to indicate slowing down. The changes I have seen here, however, indicate security practitioners and/or infrastructure providers are catching on, requiring Chenlun to use better obfuscation methods. The obfuscation changes made to avoid detection emphasize the value of domain-related data to obtain context, identify patterns, and discover other connected domains.
Indicators of Compromise (IOCs)
Domains seen the 30 days between 9/23/2024 and 10/23/2024 matching the two regex patterns mentioned above can be found in our public GitHub repository.








