Post Quantum Cryptography (PQC): You May Already Be Using It!
Share this entry
Introduction
While DNS makes the Internet approachable and usable for people, cryptography makes it secure.
Without trustworthy encryption, logging on to remote computers, engaging in online banking and shopping, and exchanging confidential personal communications would be difficult, to say nothing of implications for national security-related systems. In this blog, we are going to stray from our DNS roots to talk about important changes happening in cryptography.
Brief Background on Cryptography
Historically, Internet encryption has relied on a number of well-proven cryptographic algorithms, most notably RSA (Rivest–Shamir–Adleman)1, Diffie-Helman (DH)2, and Elliptic Curve cryptography (ECC)3. While those algorithms are robust against publicly-known attacks by traditional computers, recent advances in quantum computing4 have surfaced concerns that quantum-enabled attacks (such as Schor’s algorithm)5 will soon be able to crack some mainstream cryptographic algorithms. If/when this happens, sensitive network traffic may become visible to unintended 3rd parties.
The amount of time left until large-scale fault-tolerant quantum computers become generally available is uncertain. Some knowledgeable experts predict that we’ve only got three to five years left6
– virtually no time at all when it comes to rolling out a replacement for widely used cryptographic algorithms. Many industry leaders are very hard at work on commercializing quantum computing, including:
- Amazon’s Braket Quantum Cloud Computing7
- Atom Computing8
- D-Wave Systems9
- Google’s QuantumAI Initiative10
- IBM11
- Intel12
- IonQ13
- IQM Quantum Computers14
- Microsoft Quantum15
- planqc16
- PsiQuantum17
- Quantinuum18
- QueEra19
- Rigetti20
- TerraQuantum21
Moreover, even BEFORE large-scale fault-tolerant quantum computers become available, nation-state adversaries may be “vacuuming up” all the network traffic they can intercept, even if it is encrypted, squirreling it away until the future date when it CAN be successfully decrypted (what some call “Harvest Now, Decrypt Later.”)22.
So, the push to decrypt quantum computing is “half the story.” Let’s now talk about the other half, post quantum cryptography (PQC).
Post Quantum Cryptography Standards from NIST
For nearly a decade, the National Institute of Standards and Technology (NIST) has been hard at work standardizing new cryptographic algorithms that will be secure even when practical quantum computing systems have been realized23. The new algorithms rely heavily on “Module Learning with Errors,” a problem from advanced mathematics24 that most non-mathematicians have probably never even heard of. It is thus perhaps rather appropriate that the names of the new NIST-approved PQC algorithms draw heavily from science fiction-related themes. I quote:25
- “FIPS 203 specifies a cryptographic scheme called the Module-Lattice-Based Key-Encapsulation Mechanism Standard, which is derived from the CRYSTALS-KYBER submission. A key encapsulation mechanism (KEM) is a particular type of key establishment scheme that can be used to establish a shared secret key between two parties communicating over a public channel. […]”
- “FIPS 204 and 205 each specify digital signature schemes, which are used to detect unauthorized modifications to data and to authenticate the identity of the signatory. FIPS 204 specifies the Module-Lattice-Based Digital Signature Standard, which is derived from CRYSTALS-Dilithium submission. FIPS 205 specifies the Stateless Hash-Based Digital Signature Standard, which is derived from the SPHINCS+ submission. […] NIST is also developing a FIPS that specifies a digital signature algorithm derived from FALCON as an additional alternative to these standards.”
The Internet Engineering Task Force (IETF) has a (recently expired) draft RFC that’s relevant, see “Kyber Post-Quantum KEM”26
Meaningful Deployment of Post Quantum Cryptographic Algorithms Is Already Happening
What’s amazing is that Post Quantum Cryptographic algorithms have been deployed and are already in widespread use. YOU may even be using PQC algorithms on your computer right now! To understand how that can be the case, start with a cool network statistical service offered by Cloudflare called “Cloudflare Radar.”27
Looking at United States https request traffic seen by Cloudflare for the 24 hours ending Friday, September 13th, 2024, we see:
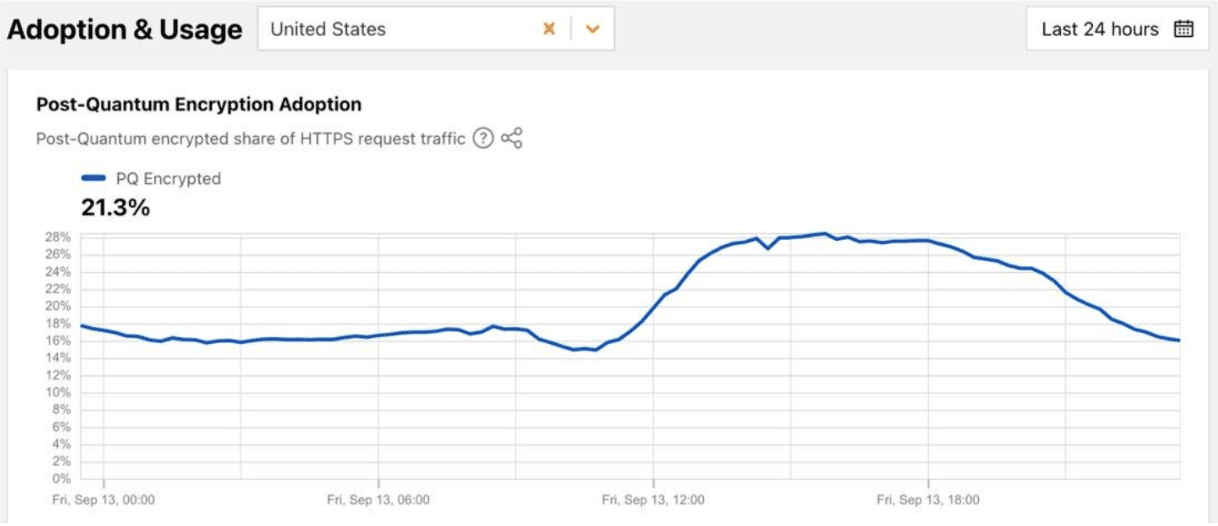
Up to 28% of the data seen by Cloudflare Radar is ALREADY using PQC! Amazing! How’s that even possible?
- Cloudflare enabled PQC for their customers as described in a 2023 blog28. That handles the server side.
- Then Google deployed default support for PQC in desktop Chrome installs for TLS 1.3 and QUIC and on Google’s servers29. Few people seem to have had problems30 (or even noticed)!
- Support in Firefox is still experimental/disabled by default. If you use Firefox and want to experiment with PQC now, go to
about:configin the Firefox browser address bar and search forkyber- Double click on the
security.tls.enable_kybersetting to set it totrue, thereby enabling it.
If you’re using QUIC and want to enable it there, too, also enablenetwork.http.http3.enable_kyber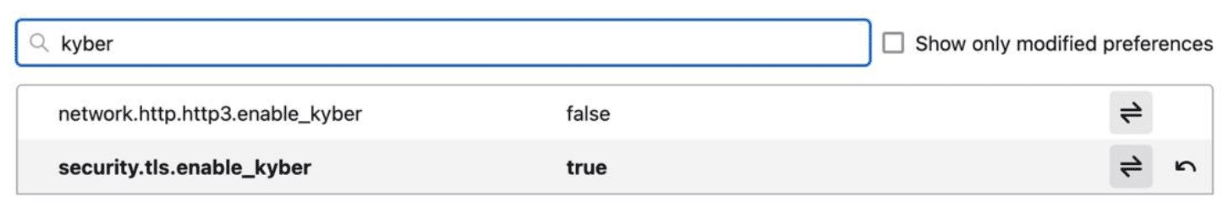
- Restart Firefox.
- If you ever decide you’d like to disable it for whatever reason, visit that setting again, and set the
kybersettings tofalse. Restart Firefox.
- Double click on the
- What about other browsers? Checking popular browsers on a Mac M1 laptop running Sonoma 14.6.1:
- Brave: Current version supports PQC by default.31
- Opera: Current version supports PQC by default.32
- DuckDuckGo.App: NOT using PQC as of 1.104.0 (251).33
- Safari: NOT using PQC as of 17.6.ToR: NOT using PQC as of 13.5.334
- ToR: NOT using PQC as of 13.5.335
- What about other platforms, such as the iPhone?
- Web browsers on mobile devices will often NOT enable PQC support by default (yet) – it’s a matter of protocol overhead on what are already often-slow platforms.
- When it comes to other mobile applications, note:
- “iMessage with PQ3: The new state of the art in quantum-secure messaging at scale”36
- “Quantum Resistance and the Signal Protocol”37
- “What about Microsoft?”
- See “Microsoft’s quantum-resistant cryptography is here”38 (September 9th, 2024)
“What If There’s a Subtle Cryptographic Problem with the New PQC?”
At least in the case of Chrome, Firefox, Brave, and Opera they’re all using a hybrid algorithm called “X25519Kyber768Draft00.”39 Want to check/confirm? Visit https://pq.cloudflareresearch.com/ – it will conveniently confirm if you’re using that protocol:
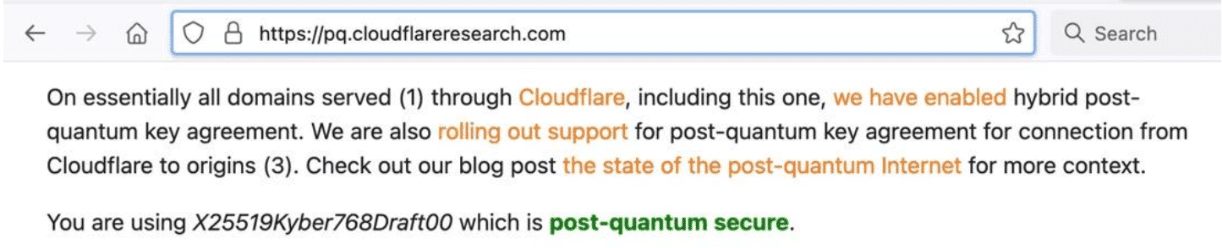
If you’re using X25519Kyber768Draft00 and there’s a problem with Kyber, traditional X25519 crypto protection will still “have you covered.” If there’s a problem with the X25519 crypto, Kyber’s “got your six.” We think that’s a comforting belt-and-suspenders deployment option!
Is This All Still Evolving? Yes…
For example, literally as this was being written on September 14, 2024, Google announced another shift in PQC algorithms, as described in “A new path for Kyber on the web.”40 That article explained that Google will be moving from the currently supported version of Kyber to a subtly different (now-standardized) version of ML-KEM with a different “codepoint,” effective with Chrome 131 (most people using the production version of Chrome are on 128). This should be effectively unnoticeable to users, but is still worth calling out as a sign that this is a very dynamic time!
Conclusions
Without the security provided by cryptography, the Internet would not be a viable platform for finance, business, research, or many other activities people rely on the Internet to provide. Quantum computers challenge the status quo regarding current cryptographic algorithms, but help is here with the creation and deployment of post-quantum cryptographic algorithms. It’s possible you may already be benefiting from them with additional improvements to come.
Sources
1 https://en.wikipedia.org/wiki/RSA_(cryptosystem)
2 https://en.wikipedia.org/wiki/Diffie%E2%80%93Hellman_key_exchange
3 https://en.wikipedia.org/wiki/Elliptic-curve_cryptography
4 Short introduction: https://mitsloan.mit.edu/ideas-made-to-matter/quantum-computing-what-leaders-need-to-know-now Book length (389 pages): “Quantum Computing: A Gentle Introduction,”
https://www.amazon.com/Quantum-Computing-Introduction-Engineering-Computation/dp/0262526670
5 https://en.wikipedia.org/wiki/Shor%27s_algorithm
7 https://aws.amazon.com/braket/
11 https://www.ibm.com/quantum
12 https://www.intel.com/content/www/us/en/research/quantum-computing.html
15 https://quantum.microsoft.com/
17 https://www.psiquantum.com/
18 https://www.quantinuum.com/
21 https://terraquantum.swiss/
22 https://en.wikipedia.org/wiki/Harvest_now,_decrypt_later
23 https://csrc.nist.gov/projects/post-quantum-cryptography
24 The mathematically inclined may find “On The Hardness Of The Module Learning With Errors Problem,” to be interesting, see https://langloi227.users.greyc.fr/webpage/20230602_slides.pdf
25 https://csrc.nist.gov/News/2024/postquantum-cryptography-fips-approved
https://www.nist.gov/news-events/news/2024/08/nist-releases-first-3-finalized-post-quantum-encryption-standards says that “[…] when the draft FIPS 206 standard built around FALCON is released, the algorithm will be dubbed FN-DSA, short for FFT (fast-Fourier transform) over NTRU-Lattice-Based Digital Signature Algorithm.”
26 https://datatracker.ietf.org/doc/html/draft-cfrg-schwabe-kyber
27 https://radar.cloudflare.com/
28 https://blog.cloudflare.com/post-quantum-to-origins/
29 “Advancing Our Amazing Bet on Asymmetric Cryptography,” May 23rd, 2024
https://blog.chromium.org/2024/05/advancing-our-amazing-bet-on-asymmetric.html
and “Post-Quantum Cryptography: Standards and Progress,” August 13th, 2024
https://security.googleblog.com/2024/08/post-quantum-cryptography-standards.html
30 Some software which did apparently have some issues with the PQC rollout can be seen at https://tldr.fail/
34 https://www.apple.com/safari/
35 https://www.torproject.org/
36 https://security.apple.com/blog/imessage-pq3/
See also https://cloudsecurityalliance.org/blog/2024/05/17/apple-s-new-imessage-signal-and-post-quantum-cryptography
37 https://signal.org/blog/pqxdh/
39 https://www.ietf.org/archive/id/draft-ietf-tls-hybrid-design-10.txt
40 https://security.googleblog.com/2024/09/a-new-path-for-kyber-on-web.html






