Return to Sender - A Brief Analysis of a US Postal Service Smishing Campaign
Share this entry
In recent weeks there has been a noticeable uptick in campaigns targeting the US Postal Service (USPS) as an institution, even in the usual deluge of phishing and smishing emails and text messages. The volume of these reaching our families and co-workers within a period of weeks piqued our natural curiosity to dig into it and see where it leads. An example of one of these smishing messages is shown in Figure 1.
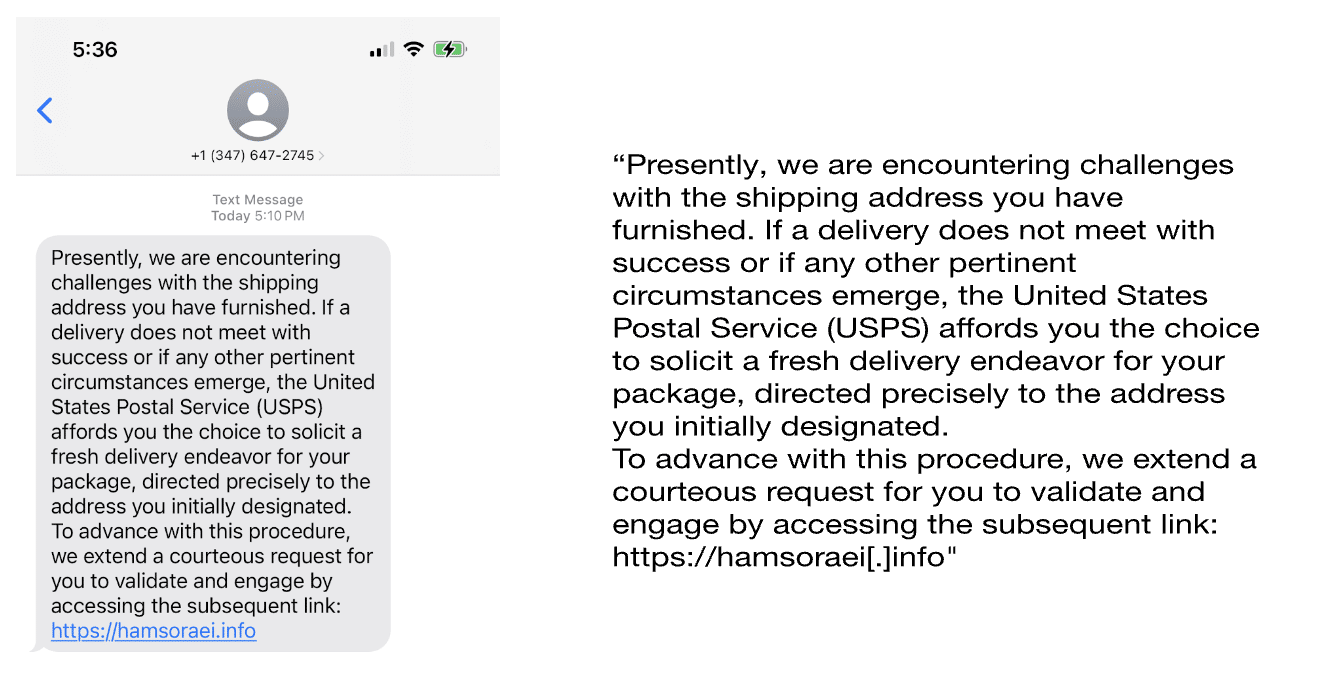
At first glance, the choice of language in the text seems suspect. Likely adopted from another phishing script and used over in this campaign, the phrasing shows signs that it was written by someone that either has English as an additional language, or has limited proficiency and likely relied on a translation service to help craft the message. Thankfully they didn’t have the foresight to use a platform like ChatGPT to help craft the content, which could have generated a more convincing lure.
Pivoting on hamsoraei[.]info
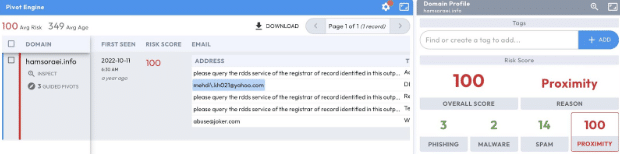
As we start to look into the domain mentioned in the text message, Figure 2 glows in the dark with a risk score of 100, the highest you can get, reflecting both the infrastructure and other previous malicious activity as well as other domains associated with it. In this case, the score is in part tied to the domain’s start of authority record (SOA), a Yahoo email mehdi\.kh021@yahoo[.]com. This unique email address, containing a backslash, is associated with 71 other domains. From here, guided pivots in Iris Investigate can be a helpful way to quickly identify more domains from this initial indicator of compromise (IOC).
By expanding our search, we can see a host of domains registered by an email address using a familiar naming convention, mehdi.k1989@yahoo[.]com, varying only by the 5 characters after the period in the email. This second email address is associated with 63 domains which also share above average risk scores. We also note a variation of the SOA record email that is missing the “\”–this variation adds an additional 30 domains to our running count of 163 domains at this point of our investigation.
By continuing to pivot through IOCs related to this person of interest, we start to get the full picture of domains and hosting infrastructure related to our investigation. Visualization tools, such as Maltego, allow us to better understand the scope and history of activity and quickly see their connections. Figure 4 shows data from this investigation using a Maltego transform on data from the DomainTools Iris platform.
When looking at indicators like email addresses that have been associated with a fairly high degree of recidivism from a domain registration perspective, it is not uncommon for individuals to reuse these addresses for other purposes as well. This ended up being true here. By using publicly available OSINT sources, you can enumerate and connect additional items related to your investigation. In this case, the person of interest used the same email addresses not only to register for different services, but tied the emails together by using them as back up or secondary emails for a number of other accounts. When these additional accounts are included, we uncover an additional 20 domains tied to the same person.
When individuals don’t expect this data to come to light, they may become lax in what else they tie to these items, including social media and other accounts that are useful in expanding and adding new prospective avenues for inquiry. This too was present in this investigation as highlighted by the Facebook account we found in Figure 5.
Reviewing this additional social media information, we have reason to believe our person of interest is an Iranian national who lives and works in Tehran, and who may have attended the Islamic Azad University. From our investigation, it is unclear what level of fluency they have in English, but could prospectively be in keeping with our initial observation that the lure text of the smish was likely not written by someone whose native language is English.
Conclusion
Even though phishing and smishing campaigns have become an unfortunate daily fact of life, they remain a significant source of prospective harm for not only individuals, but the companies and organizations whose services they use. The resulting harm both from a loss perspective as well as the emotional toll on individuals, is added to the cost in time, money, and resources that companies face in defending their customers and ensuring that their brand reputation and business operations are not impacted.
In this article, we were able to start with a single domain found in USPS smishing campaign and pivot out to identify nearly 200 domains and several email addresses associated with this threat actor. These pivots eventually lead us to a Facebook account associated with a person of interest for this campaign.
For those organizations and the law enforcement agencies that help combat and prosecute these criminal acts, being able to quickly and thoroughly identify the infrastructure and individuals associated with it, becomes important in minimizing the harm it causes. DomainTools data and services are curated and designed to identify threats, power investigations, and respond effectively to campaigns such as this. If you want to know more, please contact us.
IOCS
Emails
| Domain | Risk Score |
| avinpayamak[.]ir | 100 |
| parnasharifanimation[.]com | 100 |
| andishkademedia[.]com | 100 |
| sharifanimation[.]com | 100 |
| hamsoraei[.]info | 100 |
| 20update[.]ir | 90 |
| luxgiftlux[.]com | 82 |
| academy-fh[.]ir | 81 |
| behsoo-app[.]ir | 81 |
| asprlus[.]com | 80 |
| web3ar[.]cam | 78 |
| devloper[.]ir | 77 |
| superonline[.]click | 76 |
| jettaxi[.]click | 72 |
| superonlineme[.]ir | 71 |
| coverir[.]ir | 70 |
| animationpress[.]ir | 67 |
| sony1.[i]r | 65 |
| toseeschool[.]com | 63 |
| sarazaccessories[.]com | 60 |
| mehriazist[.]com | 57 |
| instagramme[.]ir | 57 |
| parname[.]ir | 54 |
| esetstore[.]shop | 52 |
| iranianios[.]com | 51 |
| bazarchemivevatarebar[.]com | 50 |
| parsiranwasher[.]com | 50 |
| pnpcgart[.]com | 50 |
| pooshbam[.]com | 50 |
| ts-smart-co[.]com | 50 |
| ts-tarh[.]com | 50 |
| siboushop[.]ir | 50 |
| amoomehdi[.]com | 49 |
| amoomahdi[.]com | 49 |
| ganjineman[.]com | 49 |
| upvc-behinesazan[.]com | 49 |
| giftaks[.]ir | 48 |
| adakcharmrasa[.]ir | 47 |
| 7thart-m[.]com | 46 |
| film-pardaz[.]com | 46 |
| parskaolin[.]info | 46 |
| besigni[.]ir | 46 |
| bankesaz[.]com | 45 |
| ariyaart[.]com | 41 |
| silverfood[.]ir | 37 |
| mehriadarman[.]ir | 36 |
| siboshop[.]ir | 36 |
| c730[.]ir | 36 |
| 2line[.]ir | 36 |
| iosia[.]ir | 35 |
| kakperess[.]ir | 35 |
| 99web[.]ir | 35 |
| rahnamaapp[.]site | 35 |
| stakam[.]ir | 34 |
| clickbekhar[.]ir | 34 |
| photoiran-co[.]com | 34 |
| tashstone[.]org | 34 |
| idsazan[.]ir | 34 |
| mediageram[.]ir | 34 |
| avaper[.]ir | 34 |
| tashstone[.]com | 33 |
| toloezarineeghtesad[.]ir | 33 |
| melkbazme[.]ir | 33 |
| meymehmarket[.]ir | 33 |
| sajjadnameni[.]com | 32 |
| tashstone[.]net | 32 |
| ghasrelebas[.]ir | 32 |
| parna-sakhteman[.]ir | 32 |
| attarionlineme[.]ir | 32 |
| tekinja[.]com | 32 |
| raadhouseoffilm[.]ir | 31 |
| salimal666[.]ir | 30 |
| arsesraeika[.]ir | 30 |
| saliamal[.]ir | 29 |
| alamutstore[.]ir | 29 |
| arsentrans[.]com | 28 |
| andishkadehmedia[.]com | 28 |
| modaverse[.]ir | 28 |
| emdadtrip[.]com | 28 |
| digitou[.]ir | 28 |
| azinpelak[.]ir | 28 |
| khabarejadid[.]ir | 28 |
| copycopy[.]ir | 28 |
| alocms[.]ir | 28 |
| sepiderooz[.]com | 28 |
| bartarinhoghooghdan[.]ir | 28 |
| velaati[.]com | 28 |
| mooyekamand[.]com | 28 |
| sahamdaraneedalat[.]ir | 28 |
| piktakk[.]ir | 28 |
| pakhshmehrbook[.]ir | 27 |
| nasrbahar[.]com | 26 |
| addc[.]ir | 26 |
| 40o[.]ir | 25 |
| oygar[.]ir | 23 |
| nod-tia[.]com | 23 |
| arsesraeika[.]com | 22 |
| telliranshop[.]com | 22 |
| iranpishroasia[.]ir | 21 |
| smartiweb[.]ir | 20 |
| azinpelak[.]com | 20 |
| tarhopelak[.]com | 20 |
| tkolbet[.]com | 20 |
| pakhshefadak[.]ir | 20 |
| mngg[.]net | 20 |
| pazinehpress[.]ir | 20 |
| hesarakidokhtarane[.]ir | 18 |
| ebiroll[.]ir | 18 |
| hamsoraa[.]ir | 17 |
| gardeshgareirani[.]com | 16 |
| clickbekhar[.]com | 15 |
| pishroyadaknovin[.]com | 15 |
| meki[.]me | 15 |
| denavasher[.]com | 15 |
| gdoe[.]ir | 15 |
| avinpersian[.]com | 13 |
| wordfa24[.]ir | 11 |
| alocms[.]com | 11 |
| sarzaminideal[.]ir | 11 |
| maharelec[.]com | 11 |
| flowers-cake[.]ir | 11 |
| cofeios[.]com | 11 |
| sibou[.]ir | 10 |
| bargpichak[.]ir | 10 |
| cafe7[.]ir | 10 |
| azinorder[.]ir | 9 |
| danesh-book[.]ir | 9 |
| matbazaar[.]se | 8 |
| bimesaad[.]ir | 8 |
| ropekaa[.]ir | 8 |
| datisabzar[.]com | 5 |
| ghabfather[.]ir | 5 |
| ghabfather[.]com | 5 |
| khatekhana[.]ir | 5 |
| khonegi-kala[.]ir | 5 |
| drackman2027[.]ir | 5 |
| taradox[.]ir | 5 |
| smarticoach[.]ir | 5 |
| tehranfoton[.]ir | 5 |
| nadcompelex[.]ir | 5 |
| rihajeans[.]ir | 5 |
| 20web[.]ir | 5 |
| raeekala[.]ir | 5 |
| beautiland[.]net | 4 |
| timekook[.]ir | 1 |
| zooby[.]ir | 1 |
| wp30[.]ir | 1 |
| instasos[.]ir | 1 |
| itunes24[.]ir | 1 |
| tarna[.]ir | 1 |
| appomobil[.]ir | 1 |







