Strengthen Your Investigations’ Resolve with pDNS
Passive DNS
The Internet’s Domain Name System (DNS) is the underlying address book that maps human-readable names to machine-readable numbers. For this reason DNS is considered a core fabric of the Internet’s functionality and is being leveraged by many research and security teams to both block and redirect malicious traffic.
Passive DNS (pDNS) takes that approach a step further and through a global sensor network logs the anonymized query and response pairs that go through DNS recursive resolvers. A passive DNS data set also logs the first time a record set was seen and the last time the record set was seen along with a count of every instance of that record set.
Leveraging this, security teams can hunt through malicious domains to see the underlying infrastructure set up behind them, any DNS tunneling for C2 or data exfiltration happening and the historical fluctuation between malicious servers behind a domain name. The uses do not stop there and that is why DomainTools has worked to curate a comprehensive set of pDNS data sets in the Iris Investigate Platform.
PDNS in the DomainTools Iris Investigate Platform
The pDNS in DomainTools Iris Investigate Platform is marked as A (Farsight pDNS), B, C and D to indicate the four providers that we source data from. We have taken a curated approach to sources as the pDNS space contains more than a dozen providers with some overlap between them. In a data set already fraught with noise we find this scoped approach to provide the most value to customers and we continually reevaluate on a regular cycle to make sure our choices remain sound.
Coupled with the pivoting capabilities of the Iris Investigate Platform, analysts can find connections between entities through data points they have in common. Iris Investigate also includes “Guided Pivots” which automatically show which pivots are most likely to lead to relevant connections. In addition, users can pivot directly from pDNS requests and responses into their active investigation, expanding queries with new domains found while exploring record sets. This integration allows for investigators to quickly expand on our classic WHOIS data set to discover new areas of malicious activity that can then be further enhanced using either our IP, NS or SSL data sets all under a single pane of glass.
Examples of Data Found In pDNS
DNS Tunneling
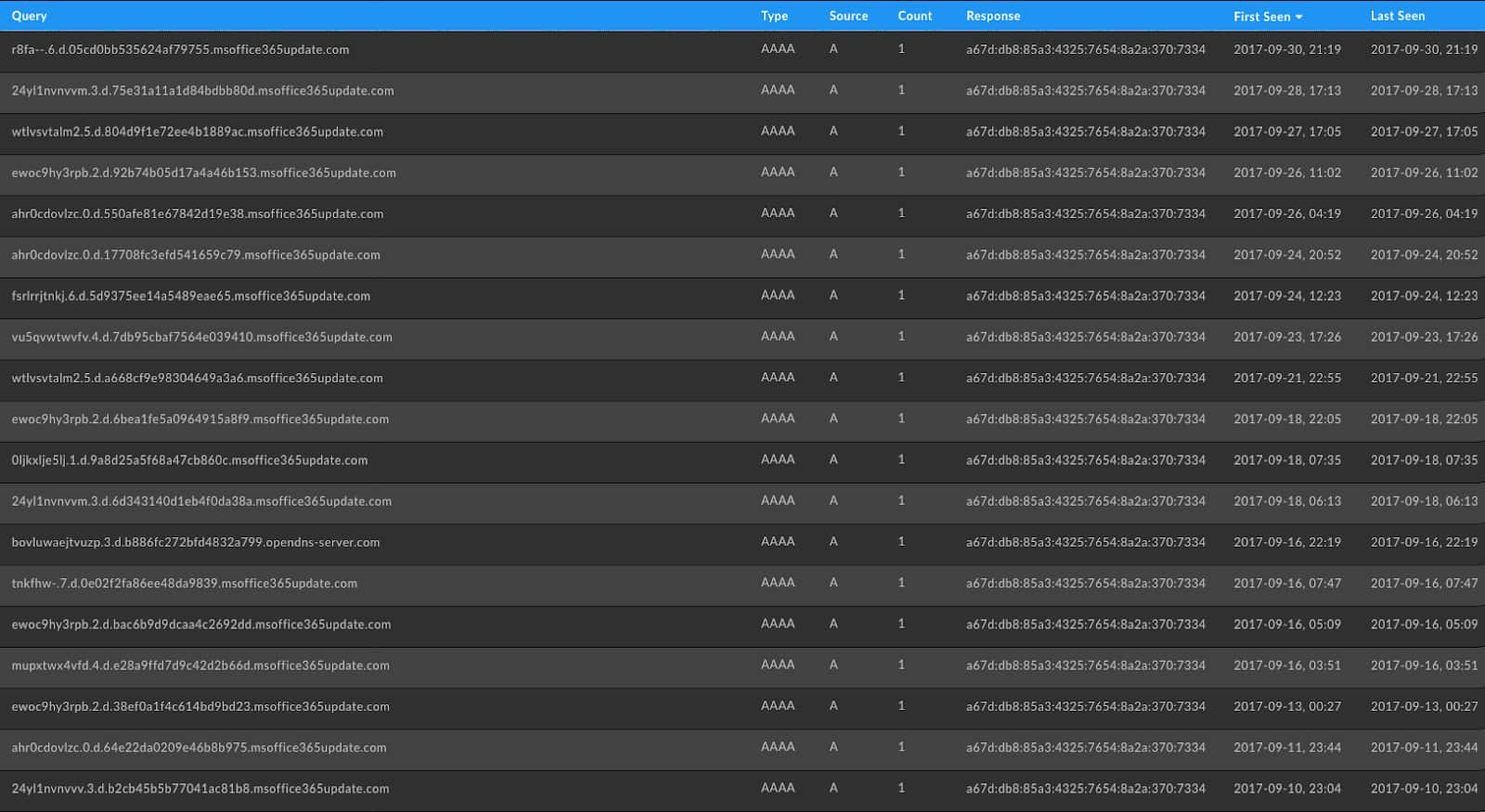
DNS tunneling involves using DNS to either exfiltrate data or function as a command and control for a botnet. Since DNS is unmonitored and unrestricted at many organizations this is an increasingly popular method used by attackers in the wild. Below shows the records that can be found involving the ISMDoor malware variant that leverages DNS for signaling and data exfiltration.
Actor Infrastructure Mapping
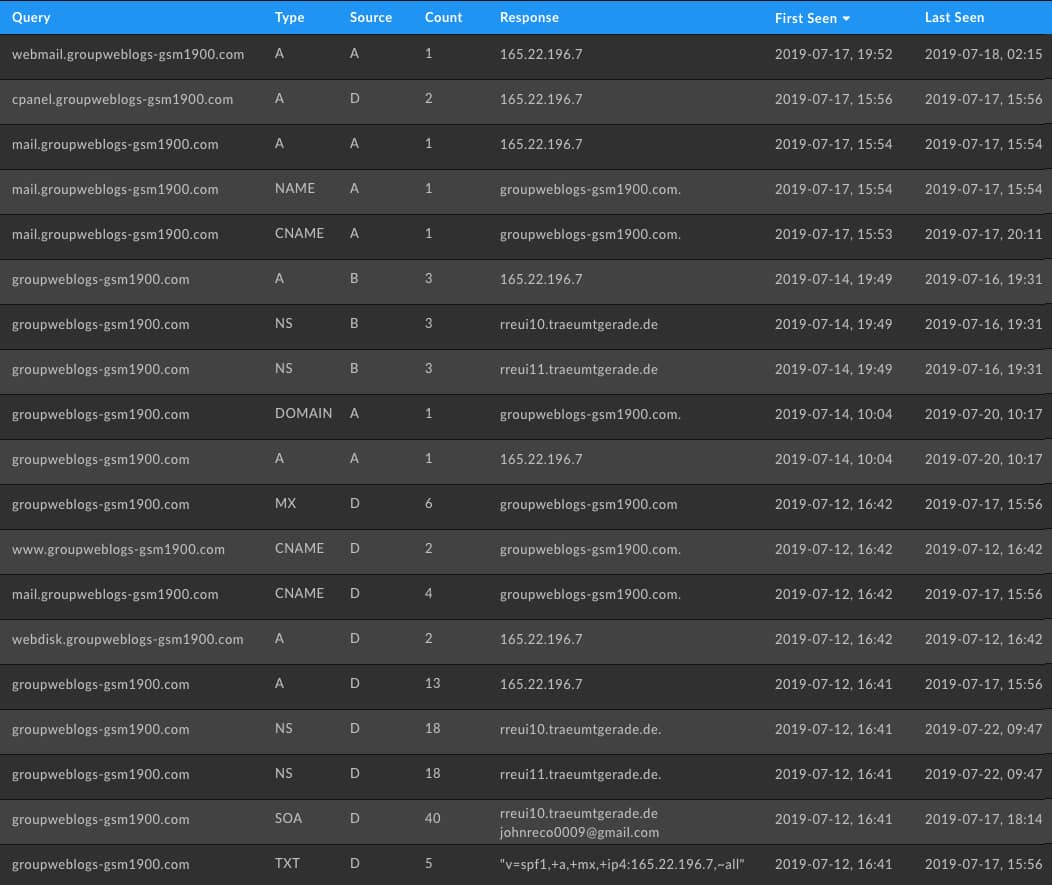
DNS structure reveals a lot about the tooling attackers use and can provide a fingerprint for that actor’s operations. Many run of the mill cybercriminals will use the same infrastructure and tools across the board choosing to set things up programmatically so patterns can often be spotted in pDNS. In this instance you can see the use of cPanel, webdisk and more which indicates an OVH user. The spread of the dates reveals the time table of an actor’s work as well as the use Dyn Dynamic DNS services to point at their nameservers — showing that these attackers run their own DNS infrastructure.
Historical Picture of Infrastructure and Fast Flux
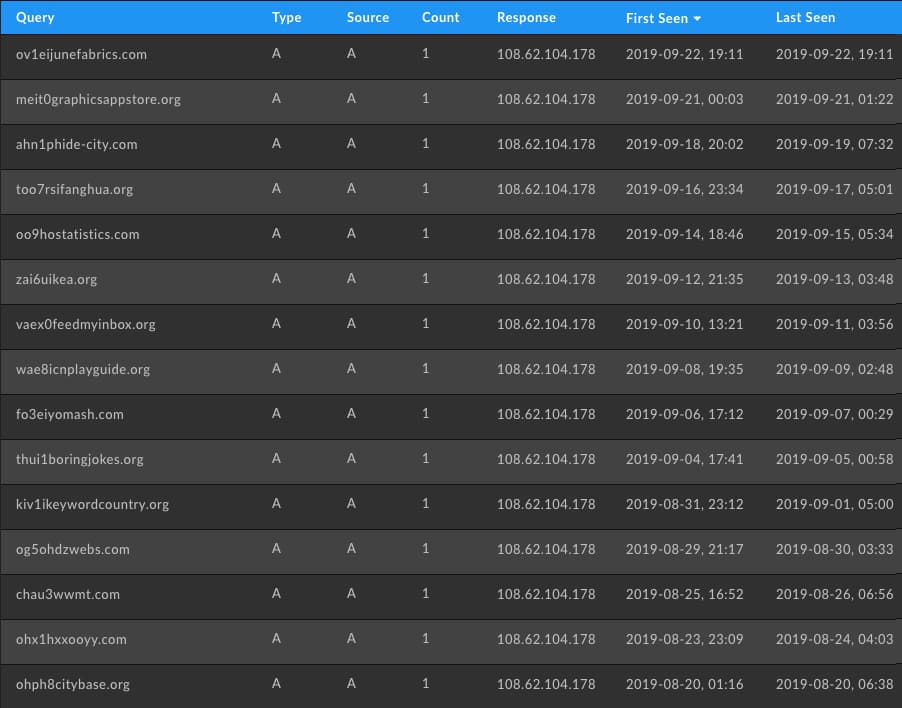
pDNS can show the shifting infrastructure behind a domain over a period of time that would otherwise be lost. Since pDNS collection relies on picking up an actual query we can see record sets that would have been lost unless there was active polling of the record at the record’s TTL. Additionally, tracking past fast flux domains used by a botnet can be quickly found using the IP and an inverted query by response in pDNS.
Actor Motive Prediction
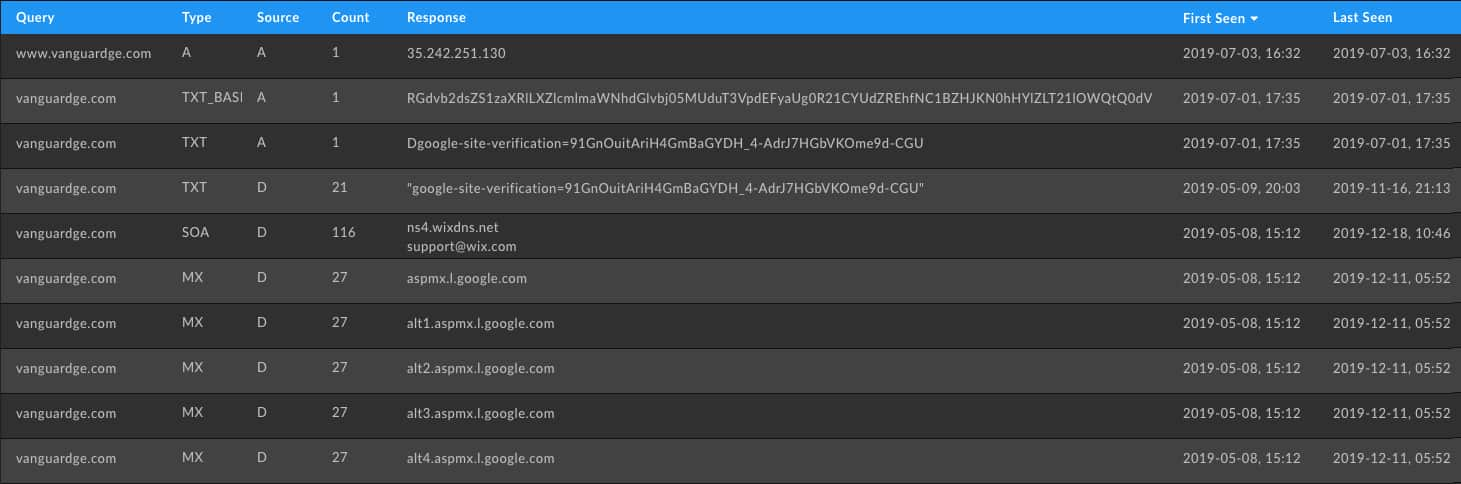
Certain types of attacks require extra setup that can be revealed in pDNS. For instance a business email compromise (BEC) will need to have their email domains verified through Google, ZOHO or another provider. Seeing these manual entered SPF and DKIM records indicates the intention to use a domain to send email. In the event that your team found this domain through proactive hunting using a product like DomainTools PhishEye to reveal typo registrations then these records are a strong indicator for future malicious intent.
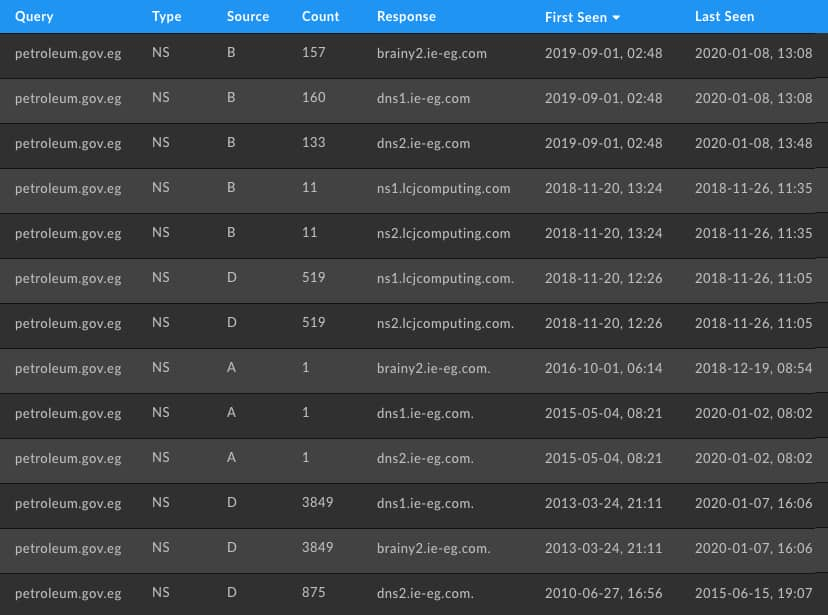
DNS Hijacking
DNS hijacking has become a lot more prevalent in recent years and more common knowledge with the release of Talos’ SeaTurtle paper. DNS hijacking is easy to spot in pDNS because the time of a switch to another nameserver is immediately picked up with the new NS record set. The lcjcomputing[.]com domains below were the actor-controlled nameservers originally reported by Talos.
Many Uses, All Insightful
PDNS is a treasure trove of infrastructure mapping data with a wide swath of use cases. Whether you use it to find more pivot points in your investigations, track actor infrastructure changes, or to monitor your own domains for DNS hijacking: pDNS is an essential tool in every investigator’s toolkit.





