Threat Hunting Using Farsight Historical Passive DNS observations via the Malware Information Sharing Platform (MISP)

The Malware Information Sharing Platform (MISP) recently updated Farsight DNSDB Passive DNS, a hover-and-expansion module used by security professionals to expand hostname and IP addresses for threat hunting and other cyberinvestigations.
Today we are excited to announce a three-part webinar series – CRAWL, WALK, RUN – that will explore this newly updated module and teach you many things including: the fundamentals of passive DNS, the reasons it is so important to have objective historical observation, typical use cases you may face in your everyday activities defending your organisations, and how passive DNS observations will help you, both, using Farsight interface, but most importantly, using MISP platform for investigation and data sharing.
You do not need to have any special prior knowledge to attend – we can take the journey together, from covering the very basics to a full investigation of a compromise. You are encouraged to attend all three webinars, but also can easily attend only the one or two events that most interest you. The webinars are scheduled for Tuesday April 20th, 2021, Tuesday May 4th, 2021 and Tuesday May 11th, 2021.
In the first part – CRAWL – you will learn the basics about passive DNS and popular use cases for threat hunting, brand protection and other cybersecurity-related activities, as well as an overview of MISP – a powerful open-source threat sharing platform for sharing, storing and correlating Indicators of compromise of targeted attacks, threat intelligence, financial fraud information, vulnerability information or even counter-terrorism information. We will also show how Farsight DNSDB is integrated with MISP to advance your cyberinvestigations, as well as our future plans to improve the integration and the feature set of the module.
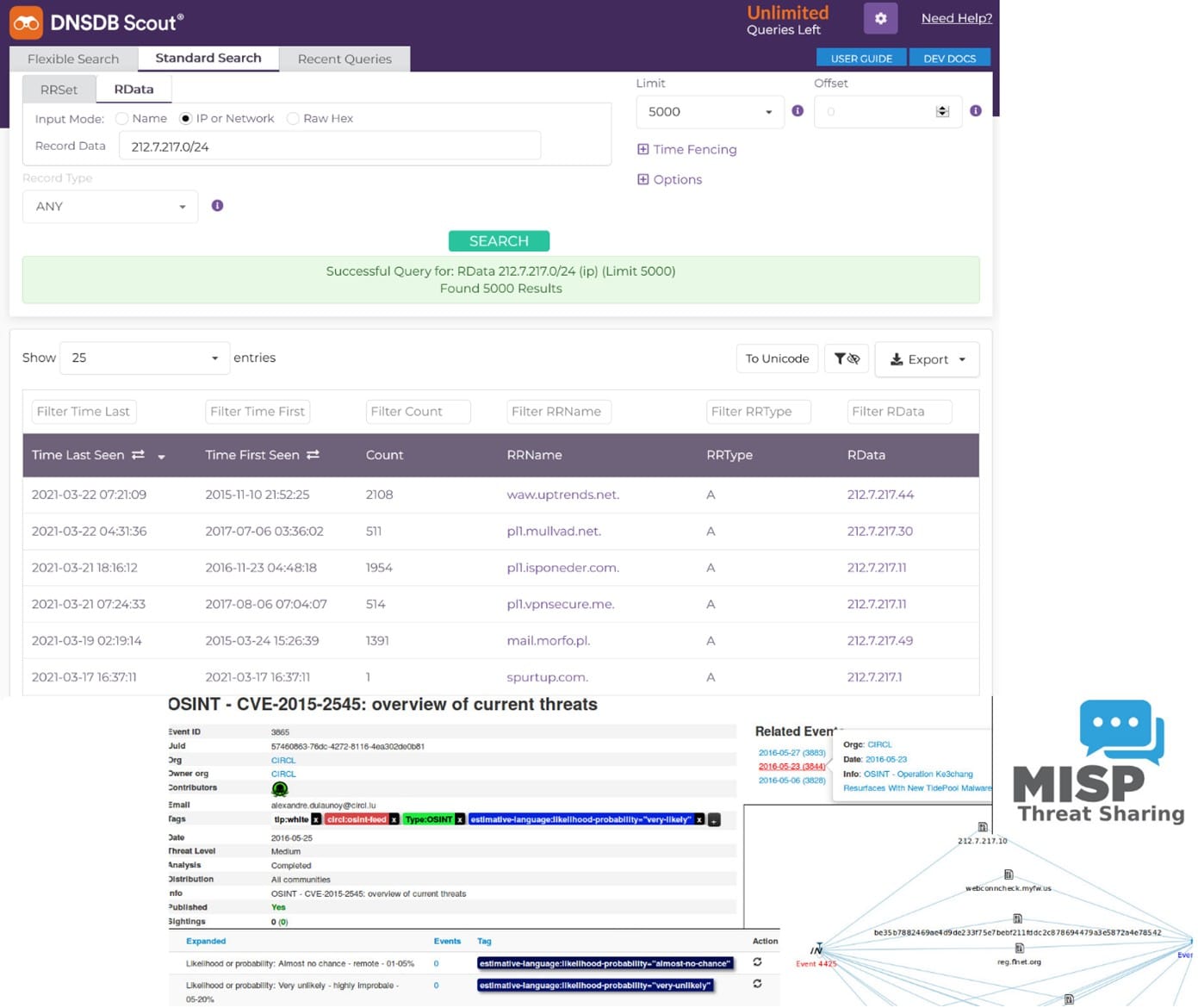
In the second of the three-part series, – WALK – we will focus on demonstrating several real-world examples using both Farsight DNSDB and MISP in your investigations. Those examples will span across different disciplines that can effectively use MISP platform for investigations, collaboration, and data sharing, to improve your efficiency, response times, and inter-team workflow.
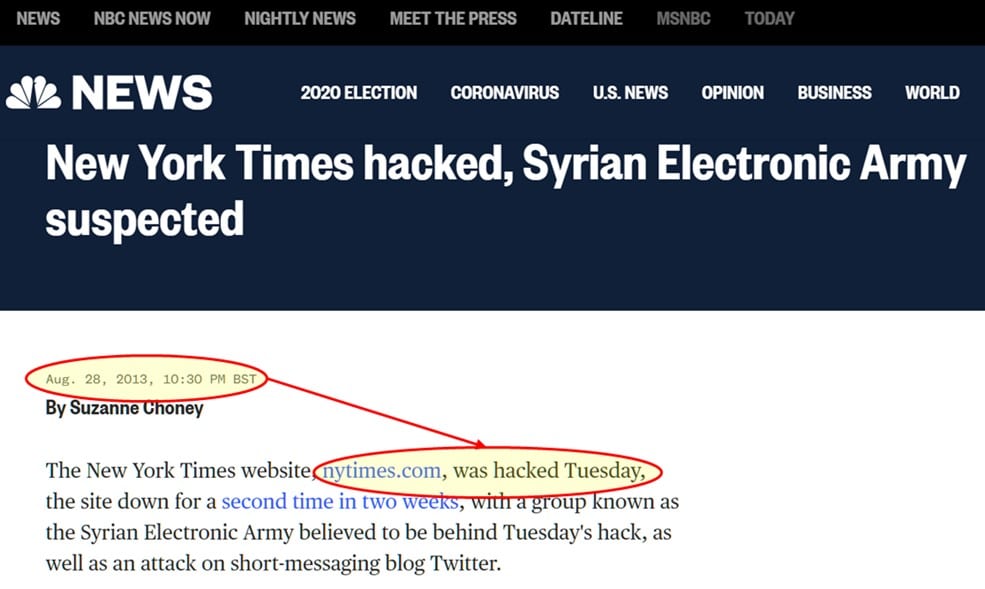
In the last part of the webinar series – RUN – we will take a deep dive into a well-known incident of the past, the 2013 New York Times compromise using the combined power of Farsight DNSDB and MISP. We will show how you can use passive DNS data to investigate events that have occurred long time ago, even if for a short period of time. We’ll show you how to look for common patterns to identify similarities in Tactics, Techniques and Procedures (TTPs) of the malicious actors.
Let’s together make the internet a safer place for everyone.
Farsight DNSDB is the world’s largest historical passive DNS database, with more than 100 Billion DNS records dating back to 2010.
The MISP threat sharing platform is a free and open-source software, helping information sharing of threat intelligence including cybersecurity indicators. MISP modules are autonomous modules that can be used for expansion and other services in MISP.
To learn more about the webinar series and register for the upcoming events, please visit the registration page here.
Boris Taratine is a Principal Architect for Farsight Security, Inc.. Alexandre Dulaunoy is a Core Team Member for the MISP Project and a Security Researcher for CIRCL.

