Touched by an IDN: Farsight Security shines a light on the Internet's oft-ignored and undetected security problem
Executive Summary
Committed to making online interactions safer for all users, Farsight Security regularly investigates systemic threats to the Internet. The design and implementation of the DNS Internationalized Domain Name (IDN) system poses such a threat — one well known by DNS industry insiders and security professionals but not known or well understood by the wider public. The purpose of this research is to bridge that knowledge gap — to offer a keyhole glimpse into the shadowy world of brand lookalike abuse via IDN homographs.
Registration of confusing Internet DNS names for the purpose of misleading consumers is not news. Every user of the Internet learns — often the hard way — that much of the email they receive is forged, and many of the World Wide Web links they are prompted to click on are malicious. Yet IDN, a DNS standard representing non-English domain names, allows forgeries to be nearly undetectable by either human eyes or human judgement, or by traditional Internet user interface tools such as email clients and web browsers.
Using its real-time DNS network, Farsight Security conducted new research to determine the prevalence and reach of homographs, in the form of IDN lookalike domains, across the Internet. Specifically, Farsight examined 125 top brand domain names, including large content providers, social networking giants, financial websites, luxury brands, cryptocurrency exchanges and other popular websites. Our findings underscore that the potential security risk posed by IDN homographs is significant. Any ultimate defense against this variant of Internet forgery will rely on Internet governance and security automation. It is to inform the need for such solutions that we offer the findings below.
IDNs, Unicode, Punycode: What you need to know if you don’t know
Internationalized Domain Names in Applications (abbreviated as simply IDNA, or instances thereof referred to as “IDNs”) is a system to represent characters other than those found in Latin script/ASCII.
For example:
Chinese: 百度.中国 Farsi: تهران.ایران Russian: яндекс.рф
This system was implemented in part to bridge the digital divide between English-speaking and non-English speaking users of the Internet. It enables the registration of domain names utilizing character sets of users’ native languages.
IDNs solve the problem of how to express domain names in languages that cannot be represented in ASCII. So how are they encoded?
Unicode
Unicode is the standard for digital representation of the characters used in writing all of the world’s languages.
It provides a unique number for every character. This numerical value representing a Unicode character (i.e.: U+03B1) is
called a code point. The latest version of the Unicode standard contains
136,755 characters covering 139 modern and historic scripts.
Shown below are some Unicode characters and their respective code points (note that for ASCII values, the code points are identical to their common ASCII counterparts).
F: U+0046 A: U+0041 R: U+0052 S: U+0053 I: U+0049 G: U+0047 H: U+0048 T: U+0054 ♥: U+2665 ✪: U+272A
IDNs are bound in form and structure to Unicode. An important distinction to make is that Unicode itself is technically not an actual encoding format; it is just a massive lookup table. How characters are actually encoded into bits is handled by mechanisms like the Unicode Transformation Format (UTF)).
Punycode
By now you may be ruminating on the fact that valid DNS names are (usually) limited to the case insensitive Letters, Digits, Hyphen (LDH) namespace, which in and of itself is completely unsuitable for representing anything other than ASCII names. It certainly
cannot represent the often multi-byte Unicode character encodings, at least not without some serious help. Rather than attempting to expand the DNS alphabet,
Internet engineers decided to use an ASCII Compatible Encoding (ACE) scheme to encode the Unicode data. This ACE
is Punycode, a lossless method for converting Unicode into LDH ASCII.
By convention, Punycode encoded IDNs will contain the xn-- prefix to herald the beginning of a Punycode encoded label.
Note that, as per section 3 of RFC 1034, “the DNS specification attempts to be as general as possible in the rules for constructing domain names”. As such, technically, they can consist of octets of any value. However, it is generally “accepted” (and in many places, enforced), that only the LDH syntax is allowed.
Example Unicode to Punycode conversion:
αβγδεζηθικλμνξοπρστυφχψω --> xn--mxacdefghijklmnopqr0btuvwxy
IDNs ultimately represent Unicode labels and may appear as such to the end user, but over the wire, they are sent encoded using Punycode.
IDN Homographs
It’s no secret that different letters or characters might look very much alike. Sometimes this comes about with changes in case or font when rendering text in the same language or script. Perhaps best known is the resemblance of lowercase “l” to uppercase “I” or the visual similarity between the letter “O” and the digit “0” – which gave way to the “slashed zero.” The slashed zero is an instance of homoglyphic confusion being resolved earlier than the invention of the printing press. Characters from different alphabets or scripts may also appear indistinguishable from one another to the human eye. Individually, these “confusables” are known as homoglyphs, but in the context of the words that contain them, they constitute homographs. In this document we refer to them as “homographs,” a less popular but more precise term for our purposes.
For example, consider the following domain names:
xn--frsightsecurity-ulm.com --> fаrsightsecurity.com
^
This "CYRILLIC SMALL LETTER A" (U+0430)
xn--farsghtsecurity-xng.com --> farsɩghtsecurity.com
^
This is a "LATIN SMALL LETTER IOTA" (U+0269)
xn--farsghtsecurity-blc.com --> farsıghtsecurity.com
^
This is "LATIN SMALL LETTER DOTLESS I" (U+131)
xn--80ak6aa92e.com --> аррӏе.com
^^^^^
These are all Cyrillic characters (see the link below for more on this one)
When displayed as Unicode, these look “normal” to the casual observer. While all of the above examples of homographic domains are benign, many others are out there, and they may not be.
It should be noted that these are not new attacks. As a matter of fact, they have been known about for a long time. They have been a hazard on the Internet in the past, returning to the news recently.
New Farsight Security Research on IDNs
Our research into imposter domains that rely on IDN homograph attacks sheds light on the potential security risks posed by these bad actors to organizations and consumers. By leveraging IDN homographs, cybercriminals can easily lure users to phishing websites that are pixel-perfect renditions of the brands they’re impersonating — often completely undetected by today’s defender solutions.
Farsight Security recently engineered its infrastructure to monitor and watch for IDN homographs in real-time. In the appendix below you will find samples from an observational period of approximately three months from 2017-10-17 23:41 UTC to 2018-01-10 19:00 UTC. Specifically, we observed IDN homographs mimicking 125 top “phish-worthy” domains including large content providers, social networking giants, financial websites, luxury brands, cryptocurrency exchanges, and other popular websites. During this time period we observed a number of homographs — 116,113 to be exact.
Appendix B contains a small, manually curated dataset containing organized lists of IDN homographs. Next are three specific samples from this dataset that appear to be live phishing sites, presumably stood up with the intent of hoodwinking unsuspecting users.
Except where noted, Farsight Security makes no assumption of intent against any of the following domains or domain owners. Also except where noted, no attempt was made to verify that the owner of a domain was illegitimate or that any possible content was malicious. Indictment and take down are not within our purview. Also, please note that in all cases, attempts were made to contact each organization in advance of this publication. Finally, the following domains, while not hyperlinked in the original release of this article, are not de-fanged. Please take care not to inadvertently load one in a browser.
Appendix A: Suspected Phishing Sites
To add timeliness and relevance to this article and demonstrate that the threat of IDN homograph impersonation is both real and actively being exploited, we present two examples of what appear to be phishing websites. On the dates listed below, the following IDNs were observed to be serving content that looked suspiciously similar to the mainstream brands they were (allegedly) impersonating. While we can’t comment on the ownership or the intent of the following websites, should you decide to visit these websites, please take extreme care.
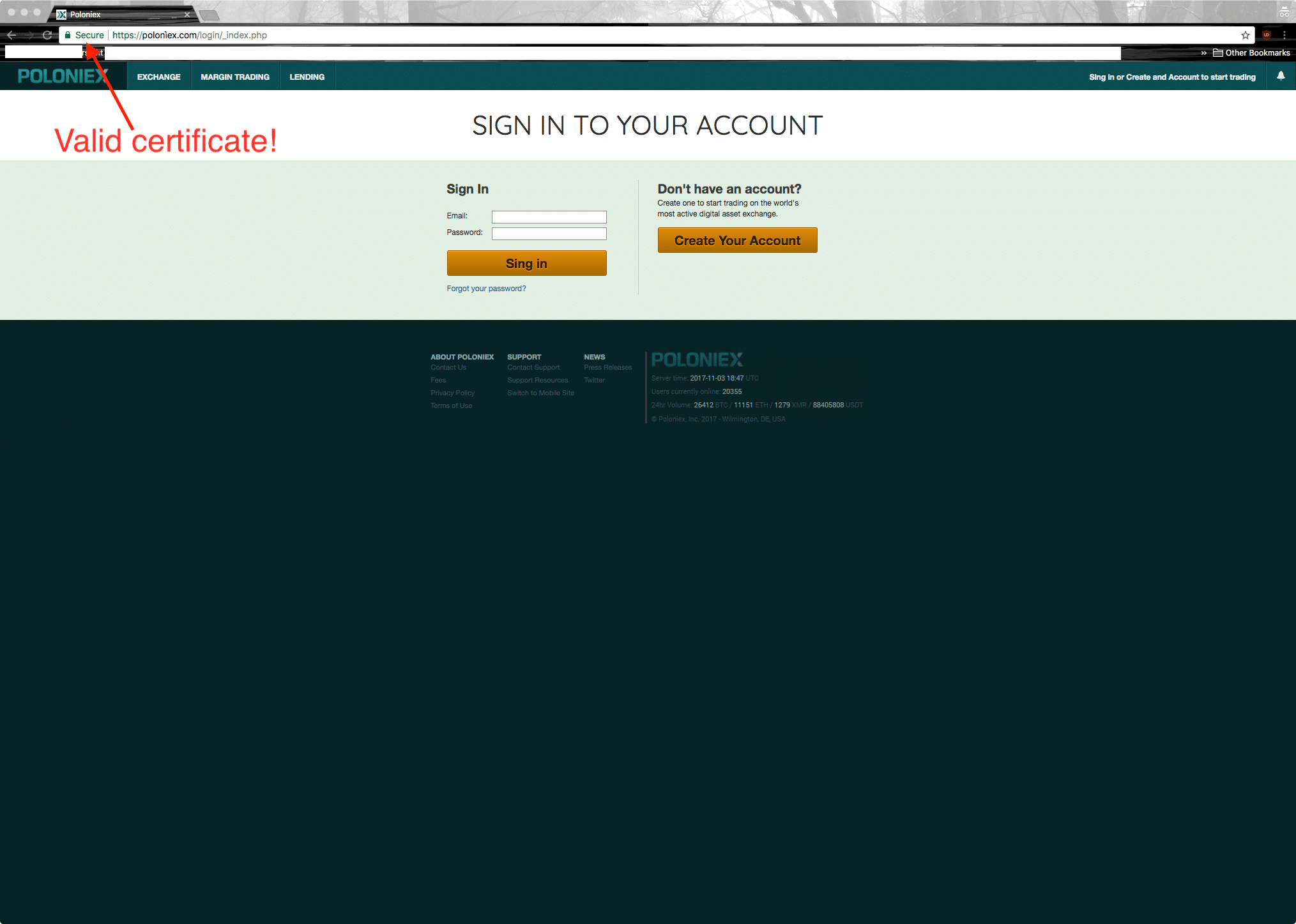
Poloniex
Poloniex is a large cryptocurrency exchange with $1.5B USD in daily transaction volume. On
2018-01-09, we observed an IDN (xn--polonex-3ya.com. --> polonìex.com) that was serving content that looked very similar to the real Poloniex website (Figure 1).
Figure 1: Screenshot of a suspected Poloniex phishing website
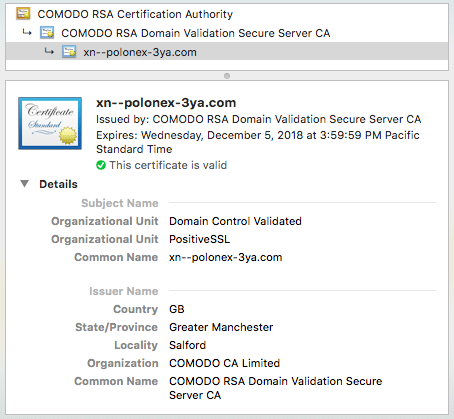
 The website also featured a valid Comodo SSL certificate (Figure 2).
The website also featured a valid Comodo SSL certificate (Figure 2).
Figure 2: The SSL certificate of the suspected Poloniex phishing website
Ignoring the fact that this is an IDN homograph of a well-known US-based website, a user’s first clue that something may be fishy here is the presumed misspelling of the phrase “Sign in” as “Sing in” (curiously, this typo occurs five times throughout the page). Additionally, frequent Poloniex users might recognize that the real Poloniex website does not immediately confront users with a “Sign in” or a “Sing in” page (it initially offers a welcome page encouraging new user sign-ups). Otherwise, the site is a reasonably good facsimile of the real Poloniex website that could easily bilk a user after deceiving them into making a login attempt.
No further attempt was made to investigate.
Facebook is the world’s largest social networking platform, with over two billion monthly users. On 2018-01-09, we observed another IDN (www.ғасеьоок.com. --> www.xn--80akppap2f62a.com.) that was also serving
content apparently intended to misdirect users into attempting to log in (Figure 3). Perhaps fortuitously, this website’s Let’s Encrypt SSL certificate (not pictured) expired in November 2017 so it did not have a green padlock connoting “safety”.
At the same time, we also found that a mobile-optimized version of the website had been deployed (m.ғасеьоок.com. --> m.xn--80akppap2f62a.com.) (Figure 4).
Figure 3: Screenshot of a suspected Facebook phishing website
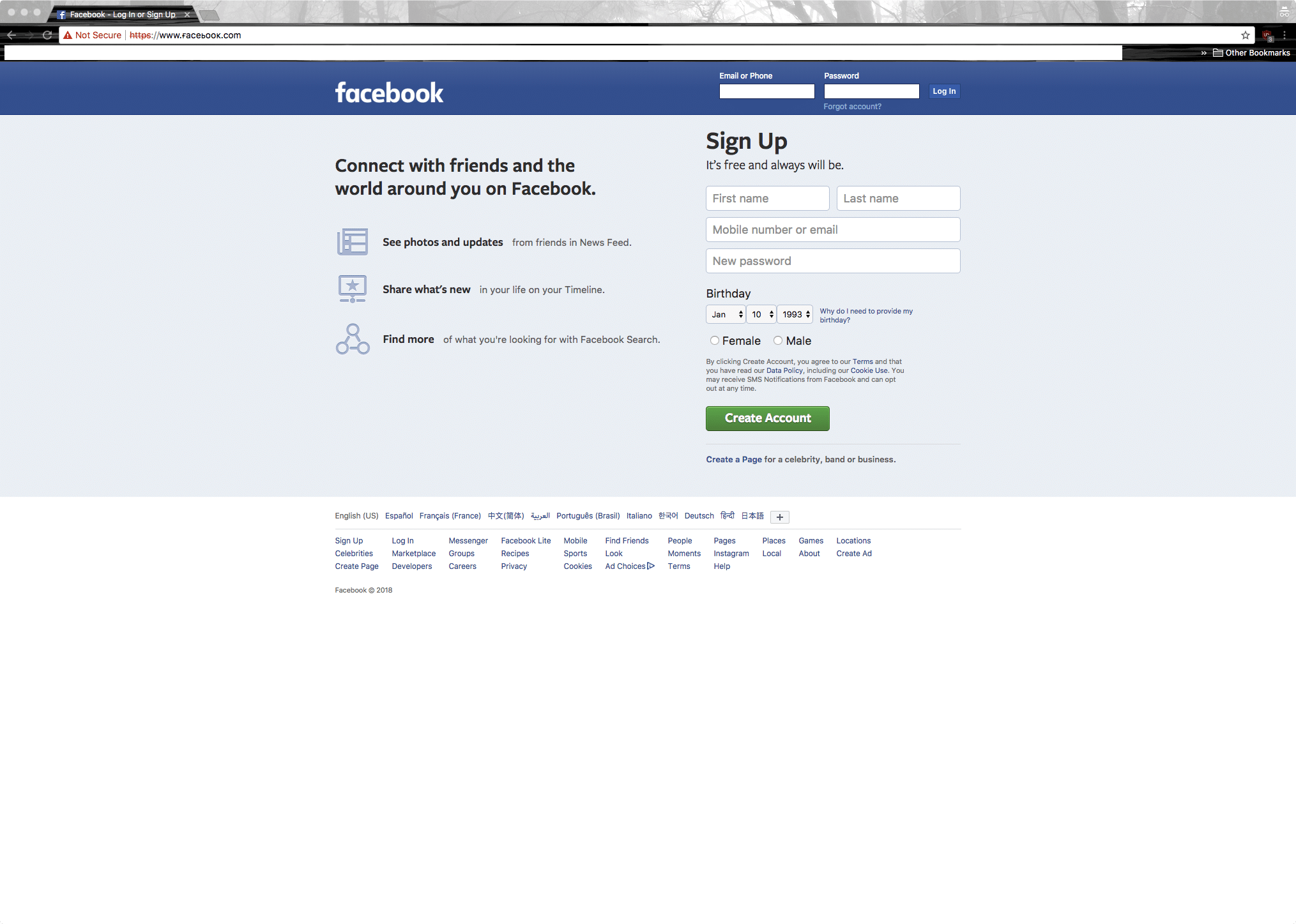
Figure 4: Screenshot of a suspected Facebook mobile phishing website

No further attempt was made to investigate either website.
Appendix B: Suspicious IDNs
The following are a subset of the IDNs we observed.
ADOBE
ns1.xn--aobe-l6b.com. --> ns1.aɗobe.com. ns2.xn--aobe-l6b.com. --> ns2.aɗobe.com. mail.xn--adoe-x34a.com. --> mail.adoḅe.com. xn--adob-yva.com. --> adobė.com. xn--adoe-x34a.com. --> adoḅe.com. xn--aobe-qua.com. --> aďobe.com. xn--dobe-p5b.com. --> ɑdobe.com.
APPLE
mail.xn--pple-zna.com. --> mail.àpple.com. ns1.xn--appl-ou5a.com. --> ns1.applẹ.com. ns2.xn--appl-ou5a.com. --> ns2.applẹ.com. www.xn--le-m1aa24e.com. --> www.ɑƿƿle.com. www.xn--pple-9na.cf. --> www.âpple.cf. www.xn--ppl-hla7b.cf. --> www.âpplê.cf. xn--ppl-hla7b.cf. --> âpplê.cf. www.xn--app-mra30o.com. --> www.appɩė.com. xn--aple-csa.com. --> apþle.com. xn--appl-8va.com. --> applę.com. xn--appl-yva.com. --> applė.com. www.xn--le-m1aa24e.com. --> www.ɑƿƿle.com.
AMAZON
www.xn--amazo-7l1b.com. --> www.amazoṇ.com. www.xn--amazo-vl1b.com. --> www.amazoṅ.com. www.xn--amzon-ucc.com. --> www.amȧzon.com. www.xn--mazon-2qa.de. --> www.âmazon.de. www.xn--mazon-2qa.eu. --> www.âmazon.eu. www.xn--mazon-wqa.com. --> www.ámazon.com. www.xn--mzn-plab3i.com. --> www.ämäzön.com. xn--amaon-6y1b.com. --> amaẓon.com. xn--amaon-7hb.com. --> amaźon.com. xn--amazo-sta.com. --> amazoñ.com. xn--amazo-vl1b.com. --> amazoṅ.com. xn--amzon-sqa.com. --> amàzon.com. xn--amzon-ucc.com. --> amȧzon.com.
BANK OF AMERICA
www.xn--bakofamerica-qfc.com. --> www.baŋkofamerica.com. mail.xn--bnkofmeric-q5aef.com. --> mail.bänkofämericä.com. secure.xn--bakofamerica-qfc.com. --> secure.baŋkofamerica.com. www.xn--ankofamerica-70c.com. --> www.ƅankofamerica.com. www.xn--bakofamerica-qfc.com. --> www.baŋkofamerica.com. www.xn--banofamerica-p7b.com. --> www.banĸofamerica.com. www.xn--bnkofamerica-pob.com. --> www.bąnkofamerica.com. www.xn--bnkofmeric-ggeef.com. --> www.bɑnkofɑmericɑ.com. www.xn--bnkofmeric-q5aef.com. --> www.bänkofämericä.com. xn--ankofamerica-70c.com. --> ƅankofamerica.com. xn--bakofamerica-qfc.com. --> baŋkofamerica.com. xn--banofamerica-p7b.com. --> banĸofamerica.com. xn--bnkofamerica-pob.com. --> bąnkofamerica.com. xn--bnkofmeric-ggeef.com. --> bɑnkofɑmericɑ.com. xn--bnkofmeric-q5aef.com. --> bänkofämericä.com.
BITTREX
xn--bitrex-rkb.com. --> bitţrex.com. xn--bittex-zx7b.com. --> bittṛex.com. xn--bittrx-7ua.com. --> bittrèx.com. www.xn--bitrex-rkb.com. --> www.bitţrex.com. www.xn--bittrx-7ua.com. --> www.bittrèx.com. xn--ittrex-hrb.com. --> ƅittrex.com. www.xn--ittrex-hrb.com. --> www.ƅittrex.com. xn--bttx-vpa4unq.com --> bíttŕēx.com
CISCO
xn--csco-lza.com. --> cısco.com. xn--csco-qpa.com. --> cìsco.com. xn--csco-vpa.com. --> císco.com. xn--n1afa3fe.net. --> сіѕсо.net.
COINBASE
xn--cinbase-10a.com. --> cõinbase.com. xn--cinbase-90a.com. --> cöinbase.com. xn--cinbase-d0a.com. --> còinbase.com. xn--cinbase-t0a.com. --> côinbase.com. xn--coibase-6za.com. --> coiñbase.com. xn--coibase-r13c.com. --> coiṇbase.com. xn--coinbae-fqb.com. --> coinbaşe.com. xn--coinbas-8xa.com. --> coinbasè.com. xn--coinbas-pya.com. --> coinbasê.com. xn--coinbas-z8a.com. --> coinbasė.com. xn--coinbse-9wa.com. --> coinbäse.com. xn--coinbse-lwa.com. --> coinbáse.com. xn--conbase-0ya.com. --> coìnbase.com. xn--conbase-feb.com. --> coīnbase.com. xn--conbase-hza.com. --> coînbase.com. xn--conbase-pza.com. --> coïnbase.com. xn--conbase-sfb.com. --> coınbase.com. xn--oinbase-l5a.com. --> ĉoinbase.com. xn--oinbase-txa.com. --> çoinbase.com.
CREDIT SUISSE
xn--crditsuisse-cbb.at. --> créditsuisse.at. xn--crditsuisse-cbb.ch. --> créditsuisse.ch. xn--crditsuisse-cbb.com. --> créditsuisse.com. xn--crditsuisse-cbb.de. --> créditsuisse.de. xn--crditsuisse-cbb.dk. --> créditsuisse.dk. xn--crditsuisse-cbb.eu. --> créditsuisse.eu. xn--crditsuisse-cbb.net. --> créditsuisse.net. xn--crdit-suisse-ceb.at. --> crédit-suisse.at. xn--crdit-suisse-ceb.ch. --> crédit-suisse.ch. xn--crdit-suisse-ceb.com. --> crédit-suisse.com. xn--crdit-suisse-ceb.de. --> crédit-suisse.de. xn--crdit-suisse-ceb.dk. --> crédit-suisse.dk. xn--crdit-suisse-ceb.net. --> crédit-suisse.net. xn--credit-sisse-klb.com. --> credit-süisse.com.
EBAY
xn--bay-ema.com. --> êbay.com. xn--eby-fla.com. --> ebáy.com. xn--eby-bla.com. --> ebày.com. xn--eby-hsb.com. --> ebɑy.com. xn--eby-jla.com. --> ebây.com. xn--80aj7b8a.com. --> еьау.com.
www.xn--acebook-js3c.com. --> www.ḟacebook.com. www.xn--acebook-w1b.net. --> www.ƒacebook.net. www.xn--aceook-dg7b2i.com. --> www.ḟaceḃook.com. xn--acebook-js3c.com. --> ḟacebook.com. xn--aceook-dg7b2i.com. --> ḟaceḃook.com. xn--faboo-5xa8ftm.eu. --> faċėbooķ.eu. xn--fabook-qva9w.eu. --> faċëbook.eu. xn--facboo-k4a3x.eu. --> facėbooķ.eu. xn--facbook-4xa.com. --> facèbook.com. xn--facbook-lya.fr. --> facêbook.fr. xn--facbook-v8a.eu. --> facėbook.eu. xn--facebok-50a.fr. --> facebõok.fr. xn--facebok-60a.tk. --> faceboõk.tk. xn--facebok-h0a.eu. --> facebòok.eu. xn--facebok-x0a.fr. --> facebôok.fr. xn--faceboo-jhb.com. --> facebooĸ.com. xn--faceboo-jhb.net. --> facebooĸ.net. xn--faceook-pm3c.com. --> faceḅook.com. xn--faebok-xua7j.fr. --> façeboök.fr. xn--faebook-35a.com. --> faċebook.com. xn--fcbook-w0a9l.eu. --> fącėbook.eu. xn--fcebook-8va.com. --> fàcebook.com. xn--fceboo-w0a91b.eu. --> fącebooķ.eu. www.xn--fabook-41a0h.eu. --> www.faċėbook.eu. www.xn--fabook-xua89a.eu. --> www.façėbook.eu. www.xn--facebok-60a.tk. --> www.faceboõk.tk. www.xn--facebok-e1a.com. --> www.faceböok.com. www.xn--facebok-h0a.fr. --> www.facebòok.fr. www.xn--facebok-i0a.eu. --> www.faceboòk.eu. www.xn--faceok-sg7bq0e.com. --> www.faceḅọok.com. www.xn--faceook-1yb.com. --> www.faceƅook.com. www.xn--faebook-35a.com. --> www.faċebook.com. www.xn--faebook-64a.eu. --> www.faćebook.eu. www.xn--fcebook-s3a.tk. --> www.fācebook.tk. m.xn--80akppap2f62a.com. --> m.ғасеьоок.com. xn--80akppap2f62a.com. --> ғасеьоок.com.
www.xn--oole-9pb06e.com. --> www.ǥooɡle.com. ww25.xn--gogle-uob.com. --> ww25.gơogle.com. xn--ggle-lqaa.com. --> gòògle.com. xn--gogl-1nd42e.com. --> goοglе.com. xn--gogle-7ta.com. --> goôgle.com. xn--gogle-jua.com. --> göogle.com. xn--gogle-kua.com. --> goögle.com. xn--gogle-uta.com. --> gòogle.com. xn--gogle-vob.com. --> goơgle.com. xn--googl-n0a.com. --> googlę.com. xn--oogl-epa71n.com. --> ǵooglé.com. xn--oogle-v1a.xyz. --> ġoogle.xyz. xn--oole-9pb06e.com. --> ǥooɡle.com. www.xn--ggl-8la1ca.com. --> www.gòòglè.com. www.xn--ggle-lqaa.com. --> www.gòògle.com. www.xn--gogle-uta.com. --> www.gòogle.com. www.xn--googl-n0a.com. --> www.googlę.com.
KRAKEN
xn--80afhrc5a.com. --> кгакеп.com. xn--krken-nra.com. --> kråken.com. xn--raken-gnb.com. --> ƙraken.com. xn--raken-n5a.com. --> ķraken.com.
MICROSOFT
ww8.xn--mcrosoft-tkb.com. --> ww8.mıcrosoft.com. www.xn--mcrosoft-c2a.es. --> www.mícrosoft.es. windows.xn--mcrosoft-c2a.com. --> windows.mícrosoft.com. ww8.xn--mcrosoft-tkb.com. --> ww8.mıcrosoft.com. www.xn--icrosoft-g89c.com. --> www.ṃicrosoft.com. www.xn--mcosoft-rfb211a.com. --> www.mıcɾosoft.com. www.xn--mcrosof-7ya00i.com. --> www.mícrosofť.com. www.xn--mcrosoft-21a.ch. --> www.mìcrosoft.ch. www.xn--mcrosoft-21a.com. --> www.mìcrosoft.com. www.xn--mcrosoft-21a.eu. --> www.mìcrosoft.eu. www.xn--mcrosoft-21a.fr. --> www.mìcrosoft.fr. www.xn--mcrosoft-9ib.com. --> www.mīcrosoft.com. www.xn--mcrosoft-c2a.com. --> www.mícrosoft.com. www.xn--mcrosoft-c2a.de. --> www.mícrosoft.de. www.xn--mcrosoft-c2a.es. --> www.mícrosoft.es. www.xn--mcrosoft-c2a.eu. --> www.mícrosoft.eu. www.xn--mcrosoft-g80d.com. --> www.mịcrosoft.com. www.xn--mcrosoft-l2a.com. --> www.mîcrosoft.com. www.xn--mcrosoft-tkb.com. --> www.mıcrosoft.com. www.xn--mcrosoft-tkb.de. --> www.mıcrosoft.de. www.xn--mcrosoft-u2a.com. --> www.mïcrosoft.com. www.xn--microsft-03a.com. --> www.microsóft.com. www.xn--microsft-9fd.com. --> www.microsȯft.com. www.xn--microsot-ez9c.com. --> www.microsoḟt.com. www.xn--microsot-x9b.com. --> www.microsoƒt.com. www.xn--micrsoft-y3a.com. --> www.micrósoft.com. xn--icrosoft-g89c.com. --> ṃicrosoft.com. xn--mcosoft-rfb211a.com. --> mıcɾosoft.com. xn--mcrosof-7ya00i.com. --> mícrosofť.com. xn--mcrosoft-21a.ch. --> mìcrosoft.ch. xn--mcrosoft-21a.com. --> mìcrosoft.com. xn--mcrosoft-21a.eu. --> mìcrosoft.eu. xn--mcrosoft-21a.fr. --> mìcrosoft.fr. xn--mcrosoft-9ib.com. --> mīcrosoft.com. xn--mcrosoft-c2a.com. --> mícrosoft.com. xn--mcrosoft-c2a.de. --> mícrosoft.de. xn--mcrosoft-c2a.es. --> mícrosoft.es. xn--mcrosoft-g80d.com. --> mịcrosoft.com. xn--mcrosoft-l2a.com. --> mîcrosoft.com. xn--mcrosoft-tkb.com. --> mıcrosoft.com. xn--mcrosoft-tkb.de. --> mıcrosoft.de. xn--mcrosoft-u2a.com. --> mïcrosoft.com. xn--micosoft-i0d.com. --> micɾosoft.com. xn--microoft-l9c.com. --> microșoft.com. xn--microsft-03a.com. --> microsóft.com. xn--microsft-9fd.com. --> microsȯft.com. xn--microsof-eyb.com. --> microsofť.com. xn--microsof-hk0d.com. --> microsofṭ.com. xn--microsot-ez9c.com. --> microsoḟt.com. xn--microsot-x9b.com. --> microsoƒt.com. xn--micrsoft-y3a.com. --> micrósoft.com.
NETFLIX
xn--etflix-vwa.com. --> ñetflix.com. www.xn--netflx-0va.com. --> www.netflìx.com. ns1.xn--ntflix-iva.com. --> ns1.nêtflix.com. ns2.xn--ntflix-iva.com. --> ns2.nêtflix.com. ww1.xn--etflix-vwa.com. --> ww1.ñetflix.com. ww35.xn--etflix-vwa.com. --> ww35.ñetflix.com. ww8.xn--etflix-vwa.com. --> ww8.ñetflix.com. www.xn--etflix-vwa.com. --> www.ñetflix.com. www.xn--netflx-0va.com. --> www.netflìx.com. www.xn--netflx-7va.com. --> www.netflíx.com. www.xn--netflx-7va.eu. --> www.netflíx.eu. www.xn--netflx-f9a.com. --> www.netflįx.com. www.xn--netflx-mwa.com. --> www.netflïx.com. www.xn--netflx-t9a.com. --> www.netflıx.com. www.xn--netlix-5tb.com. --> www.netƒlix.com. www.xn--ntflix-bva.com. --> www.nétflix.com. www.xn--ntflix-i4a.com. --> www.nėtflix.com. www.xn--ntflix-iva.com. --> www.nêtflix.com. xn--etflix-vwa.com. --> ñetflix.com. xn--netflx-0va.com. --> netflìx.com. xn--netflx-7va.com. --> netflíx.com. xn--netflx-7va.eu. --> netflíx.eu. xn--netflx-f9a.com. --> netflįx.com. xn--netflx-mwa.com. --> netflïx.com. xn--netflx-t9a.com. --> netflıx.com. xn--netlix-5tb.com. --> netƒlix.com. xn--ntflix-bva.com. --> nétflix.com. xn--ntflix-i4a.com. --> nėtflix.com. xn--ntflix-iva.com. --> nêtflix.com.
NEW YORK TIMES
xn--nytmes-5va.com. --> nytímes.com. xn--nytmes-dwa.com. --> nytîmes.com. xn--nytmes-yk8b.com. --> nytỉmes.com. xn--nytmes-yva.com. --> nytìmes.com. xn--ytimes-vwa.com. --> ñytimes.com.
POLONIEX
xn--polonex-3ya.com. --> polonìex.com. xn--oloiex-yt7b2e.com. --> ṗoloṇiex.com. xn--oloniex-c53c.com. --> ṗoloniex.com. xn--plonex-6va6c.com. --> pôloníex.com. xn--ploniex-l0a.com. --> póloniex.com. xn--polniex-ex4c.com. --> polọniex.com. xn--polniex-n0a.com. --> polóniex.com. xn--poloiex-s13c.com. --> poloṇiex.com. xn--polonex-cza.com. --> poloníex.com. xn--polonex-ffb.com. --> polonįex.com. xn--polonex-ieb.com. --> polonīex.com. xn--polonex-kza.com. --> polonîex.com. xn--polonex-sza.com. --> polonïex.com. xn--polonex-vfb.com. --> polonıex.com. xn--polonex-zw4c.com. --> polonịex.com. xn--polonix-ws4c.com. --> poloniẹx.com. xn--polonix-y8a.com. --> poloniėx.com. xn--pooniex-ojb.com. --> połoniex.com.
www.xn--twittr-7ua.tv. --> www.twittèr.tv. www.xn--twittr-mva.tv. --> www.twittêr.tv. www.xn--twittr-tva.net. --> www.twittër.net. www.xn--twtter-4va.net. --> www.twítter.net. xn--twtter-cwa.com. --> twîtter.com. xn--twtter-q9a.net. --> twıtter.net. xn--twttr-7raz.com. --> twìttèr.com. xn--e1azaa2a9b5b.com. --> тшіттея.com.
WALMART
xn--wlmart-ita.com. --> wàlmart.com. xn--walmrt-lta.com. --> walmàrt.com. xn--wlmart-bua.com. --> wälmart.com. xn--wlmart-ita.com. --> wàlmart.com. xn--wlmart-pta.com. --> wálmart.com.
WELLSFARGO
xn--wellsfarg-3mc.com. --> wellsfargơ.com. xn--wellsfarg-e7a.com. --> wellsfargó.com. xn--wellsfarg-tl7d.com. --> wellsfargọ.com. xn--wellsfrgo-51a.com. --> wellsfárgo.com.
YAHOO
news.xn--yah-inaa.es. --> news.yahóó.es. news.xn--yaho-7qa.biz. --> news.yahöo.biz. news.xn--yaho-7qa.info. --> news.yahöo.info. news.xn--yaho-8qa.biz. --> news.yahoö.biz. news.xn--yaho-nqa.com. --> news.yahòo.com. news.xn--yaho-sqa.es. --> news.yahóo.es. news.xn--yaho-tqa.es. --> news.yahoó.es. news.xn--yaho-tqa.org. --> news.yahoó.org. news.xn--yah-unaa.biz. --> news.yahöö.biz. news.xn--yah-unaa.info. --> news.yahöö.info. test.xn--yaho-7qa.biz. --> test.yahöo.biz. test.xn--yaho-7qa.de. --> test.yahöo.de. test.xn--yaho-8qa.biz. --> test.yahoö.biz. test.xn--yaho-8qa.info. --> test.yahoö.info. test.xn--yaho-sqa.org. --> test.yahóo.org. test.xn--yaho-tqa.com. --> test.yahoó.com. test.xn--yaho-tqa.es. --> test.yahoó.es. test.xn--yaho-tqa.org. --> test.yahoó.org. test.xn--yaho-yqa.com. --> test.yahoô.com. test.xn--yah-unaa.info. --> test.yahöö.info. wp.xn--yah-inaa.org. --> wp.yahóó.org. wp.xn--yaho-7qa.biz. --> wp.yahöo.biz. wp.xn--yaho-7qa.de. --> wp.yahöo.de. wp.xn--yaho-8qa.biz. --> wp.yahoö.biz. wp.xn--yaho-8qa.de. --> wp.yahoö.de. wp.xn--yaho-8qa.info. --> wp.yahoö.info. wp.xn--yaho-nqa.com. --> wp.yahòo.com. wp.xn--yaho-tqa.org. --> wp.yahoó.org. wp.xn--yaho-yqa.com. --> wp.yahoô.com. ww8.xn--yaho-yqa.com. --> ww8.yahoô.com. www.xn--yah-inaa.es. --> www.yahóó.es. www.xn--yah-inaa.org. --> www.yahóó.org. www.xn--yaho-7qa.biz. --> www.yahöo.biz. www.xn--yaho-7qa.de. --> www.yahöo.de. www.xn--yaho-7qa.info. --> www.yahöo.info. www.xn--yaho-8qa.biz. --> www.yahoö.biz. www.xn--yaho-8qa.info. --> www.yahoö.info. www.xn--yaho-nqa.com. --> www.yahòo.com. www.xn--yaho-ogb.com. --> www.yahoơ.com. www.xn--yaho-tqa.com. --> www.yahoó.com. www.xn--yaho-tqa.es. --> www.yahoó.es. www.xn--yaho-x0b.com. --> www.yahȯo.com. www.xn--yah-unaa.biz. --> www.yahöö.biz. www.xn--yah-unaa.info. --> www.yahöö.info. www.xn--yaoo-674a.com. --> www.yaḣoo.com. www.xn--yaoo-6xa.com. --> www.yaħoo.com. xn--ahoo-4ra.com. --> ýahoo.com. xn--yah-inaa.es. --> yahóó.es. xn--yaho-7qa.biz. --> yahöo.biz. xn--yaho-7qa.info. --> yahöo.info. xn--yaho-8qa.info. --> yahoö.info. xn--yaho-nqa.com. --> yahòo.com. xn--yaho-ogb.com. --> yahoơ.com. xn--yaho-sqa.org. --> yahóo.org. xn--yaho-tqa.es. --> yahoó.es. xn--yaho-tqa.org. --> yahoó.org. xn--yaho-x0b.com. --> yahȯo.com. xn--yaho-yqa.com. --> yahoô.com. xn--yah-unaa.biz. --> yahöö.biz. xn--yah-unaa.info. --> yahöö.info. xn--yhoo-0na.com. --> yàhoo.com. xn--yhoo-loa.info. --> yähoo.info. xn--yho-qla5g.info. --> yähöo.info. xn--yho-qla6g.info. --> yähoö.info.
WIKIPEDIA
xn--wiipedia-nmb.com. --> wiĸipedia.com. xn--wikipdia-50a.cat. --> wikipèdia.cat. xn--wikipdia-f1a.com. --> wikipédia.com. xn--wikipdia-f1a.net. --> wikipédia.net. xn--wikipdia-f1a.org. --> wikipédia.org. xn--wikipeda-81a.com. --> wikipedìa.com. xn--wikipeda-i2a.org. --> wikipedía.org. xn--wikpedia-e2a.org. --> wikípedia.org. xn--wkipeda-rfbf.com. --> wıkipedıa.com. xn--wkipedia-c2a.org. --> wíkipedia.org. xn--wkipedia-u2a.com. --> wïkipedia.com. xn--wkpedia-7yab.org. --> wíkípedia.org. xn--wkpedia-rfbb.com. --> wıkıpedia.com. xn--wkpedia-zyab.com. --> wìkìpedia.com.
YANDEX
www.xn--yande-vx1b.com. --> www.yandeẋ.com. www.xn--yanex-vb1b.com. --> www.yanḋex.com. www.xn--yndex-0jc.com. --> www.yɑndex.com. xn--yande-uze.ru.ru. --> yandeх.ru.ru. xn--yndex-3wa.com. --> yąndex.com.
YOUTUBE
xn--yotube-jnb.com. --> yoűtube.com. xn--youtub-nva.com. --> youtubê.com. xn--youtue-7g7b.com. --> youtuḇe.com. ww11.xn--yotube-jya.com. --> ww11.yoùtube.com. ww43.xn--yotube-4ya.com. --> ww43.yoütube.com. www.xn--yotube-4ya.com. --> www.yoütube.com. www.xn--youtue-7g7b.com. --> www.youtuḇe.com. www.xn--youube-kmc.com. --> www.youțube.com. xn--outube-9ya.com. --> ýoutube.com. www.xn--outube-9s8b.com. --> www.ỳoutube.com. www.xn--outube-9ya.de. --> www.ýoutube.de.
MISC: LUXURY BRANDS
www.xn--gucc-tpa.com. --> www.guccì.com. xn--gucc-tpa.com. --> guccì.com. xn--herms-7ra.com. --> hermès.com. www.xn--herms-7ra.fr. --> www.hermès.fr. www.xn--lousvuitton-qcb.com. --> www.louísvuitton.com.
MISC: SOCIAL PLATFORMS
xn--nstagram-11a.com. --> ìnstagram.com. xn--nstagram-skb.com. --> ınstagram.com. www.xn--nstagram-skb.com. --> www.ınstagram.com. xn--istagram-7pb.com. --> iņstagram.com. www.xn--imgu-t4a.com. --> www.imguŕ.com. xn--imgr-sra.com. --> imgúr.com. xn--whatspp-lwa.com. --> whatsápp.com. xn--whtspp-cxcc.com. --> whɑtsɑpp.com.
Appendix C: Protections
The following sections discuss some measures you can take as an indivdual or an organization to address the threats posed by IDN homographs.
How Can I Protect Myself?
As with many threats targeting users on the Internet, there is no silver bullet to help protect yourself. Vigilance is key, and all the rules for spotting traditional phishing sites still apply to IDN phishing sites as well.
Some web browsers support add-ons or extensions geared toward flagging or outright blocking IDNs. If the majority of your web browsing keeps you within the realm of traditional LDH ASCII domain names, this may be an acceptable security mechanism for you.
The majority of phishing attempts still reach users via email. Regardless of the apparent sender, be extremely suspicious of any emails that include:
Distressing or enticing statements to provoke an immediate reaction, or statements that threaten consequences if you fail to respond.
Account login links, especially when combined with requests or demands to update or confirm your information.
Of course many legitimate emails contain links to additional information. Instead of clicking on these links, try copying and pasting them into your browser. This can limit the exposure to embedded links with malicious URLs.
When using a web browser, enable phishing filters or the safe browsing feature if available, and keep an eye on the browser address bar:
Any site that requests you enter a password nowadays should utilize encryption. This means the URL should begin with “https://” instead of “http://”, and most browsers will display some type of green padlock symbol or green highlighting of the address bar.
If the “s” at the end of “https://” is missing, or the address bar shows some type of red or orange warning, do not enter your password; further investigation is needed.
Be cautious if the address changes unexpectedly or if after clicking on a link, you are taken to an unfamiliar address.
Be familiar with how your browser handles IDNs. Chrome has an official page here, with links to related information for other popular browsers at the bottom of that page.
Finally, for all of the websites that support it, make sure you enable two-factor authentication (2FA). If your credentials do get phished, having 2FA enabled can provide an extra layer of security that can both alert you to a compromise of your credentials and prevent an attacker from logging in to your account. Note that even with 2FA enabled your cellphone may become the weakest link in the security chain. If your phone is used as a back-up device for resetting passwords, make sure you protect your cellular account with a strong pin-code (and hope the customer service agents are well trained enough to enforce its use for sensitive customer requests).
How Can I Protect My Organization?
If you operate a popular website that allows users to interact with one another, log in, purchase and/or download things, chances are your brand (and therefore your users!) will be on some target list for phishers and other Internet criminals.
You will want to pay attention to the IDN space, and either try to register IDN domain names proactively that could be used to impersonate your brand, or subscribe to a service that allows you to monitor recent IDN homograph registration and use in an attempt to impersonate your brand.
Updated: Thu Mar 15 16:13:12 UTC 2018, Special thanks to John C. Klensin for pointing out my colloquial misnomer about “rendering Unicode” (fonts are rendered, Unicode is displayed) and the clarification that technically any octet is allowed in a DNS label.
Technical credit for the research and development underlying the data referenced in this blog post is also shared with Stephen Watt.
Mike Schiffman is a Board Certified Vim Syntax Highlight Color Specialist for Farsight Security, Inc.