Defcon 27 had no shortage of amazing talks, workshops, villages, and events to engage with and learn from, but there was one in particular that really resonated with me: the TraceLabs Missing Persons CTF (Capture the Flag).
To be honest, I had never participated in any type of CTF before and certainly not in an OSINT CTF, so I wasn’t quite sure what to expect. Unlike a traditional CTF, the TraceLabs Missing Persons CTF is purely OSINT-based. Participants are given minimal information about nine real missing persons cases and are tasked with finding as much open source information about those cases as possible. Being fans of OSINT, DomainTools researchers Ryan Weaver, Tim Helming, and myself decided to sign up, as well as one of our friends from a different company.
This CTF was a lot more open-ended than I expected based on my limited knowledge of other CTFs: there were no explicit “flags” to capture other than just “OSINT.” This could be anything about any of the nine missing persons, including social media accounts for them or their families, photos of them, addresses, etc. Each OSINT item submitted was reviewed by a judge and then either accepted or rejected (rejected items included stuff already included in the missing persons report or stuff about the wrong individual). Certain pieces of information were worth more points than others – for example, a social media account belonging to a friend of the missing person was worth 10 points, whereas a photo of the individual taken after their missing date was worth 500.
Our team got started as soon as we could on Saturday morning. We each picked a different missing person and went about our own way of researching them. In many cases, simple googling was enough to find social media accounts, which spawned more and more information. All of the missing persons were minors, which was an interesting lesson for us to learn. I was under the impression that today’s teenagers were social media-obsessed, but their Facebooks and Twitters are all but empty. It seems today’s youth have shifted to more private social media outlets like Snapchat, for better or worse.
Some of the most effective methods of our investigation actually came from searching for the missing persons’ parents. In many cases, looking through friends lists was enough to locate a parent, and parents are way worse about locking down their online presence. Some of the parents posted every single photo, video, and passing thought of their child on Facebook, which was helpful for us from an investigation standpoint.
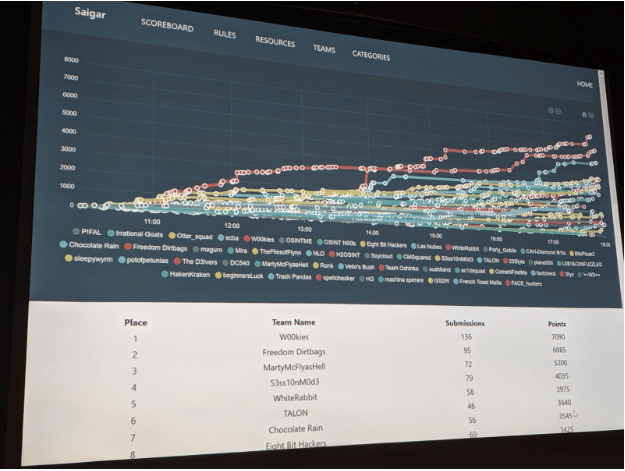
In the end, our team was able to place 5th out of 50 participating teams! For our first OSINT CTF (and my first CTF in general), we were super happy with this result.
Some key takeaways for us were that Google is your OSINT best friend. Kids today use completely different social media platforms than we do and it makes them harder to find, and while we’ve been taught our whole lives that being “too online” can lead to predators finding you, being too offline can make it difficult for authorities to find you in the event of an emergency. As with everything, it’s a balance.
We also learned that we have a lot to learn about OSINT! Do you have a favorite OSINT tool or methodology? If so, send it our way. We’d love to learn!




