Warzone 1.0 RAT Analysis Report - Part II
Warzone C2 Infrastructure – 0x5
There has been a lot of big changes to the Warzone commercial and non-commercial infrastructure since my previous write up.
The author of Warzone had provided a free Dynamic DNS service to the internet (‘warzonedns.com’). Warzone’s DDNS service was a free offering by the Warzone author.
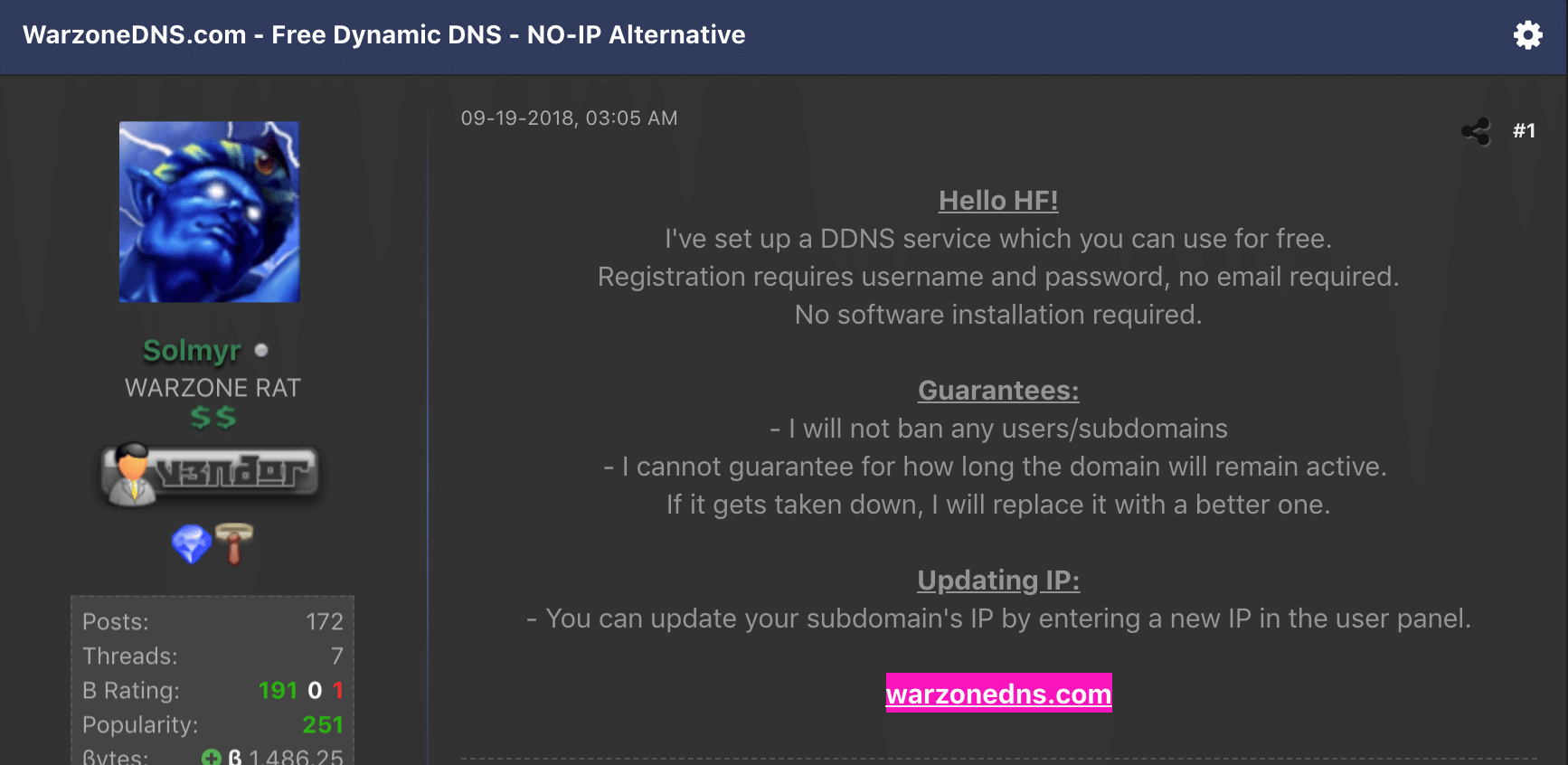
When abused by malicious threat actors, DDNS (Dynamic DNS) services allow for subdomains to have IP addresses that attackers can change generally in real-time. Attackers can then hardcode these subdomains into their malicious payloads to be distributed in their attack campaign. This allows attackers to move their infrastructure quickly in the event they are detected.
As I was monitoring and investigating the known Warzone infrastructure (‘warzone.io’ and ‘warzonedns.com’) on October 9th, I noticed that the DDNS service was taken offline. I was receiving ‘NXDOMAIN’ responses to the ‘warzonedns.com’ domain. This was a strong indicator that the domain registrar (NameSilo LLC) had banned the domain or the author took it down.
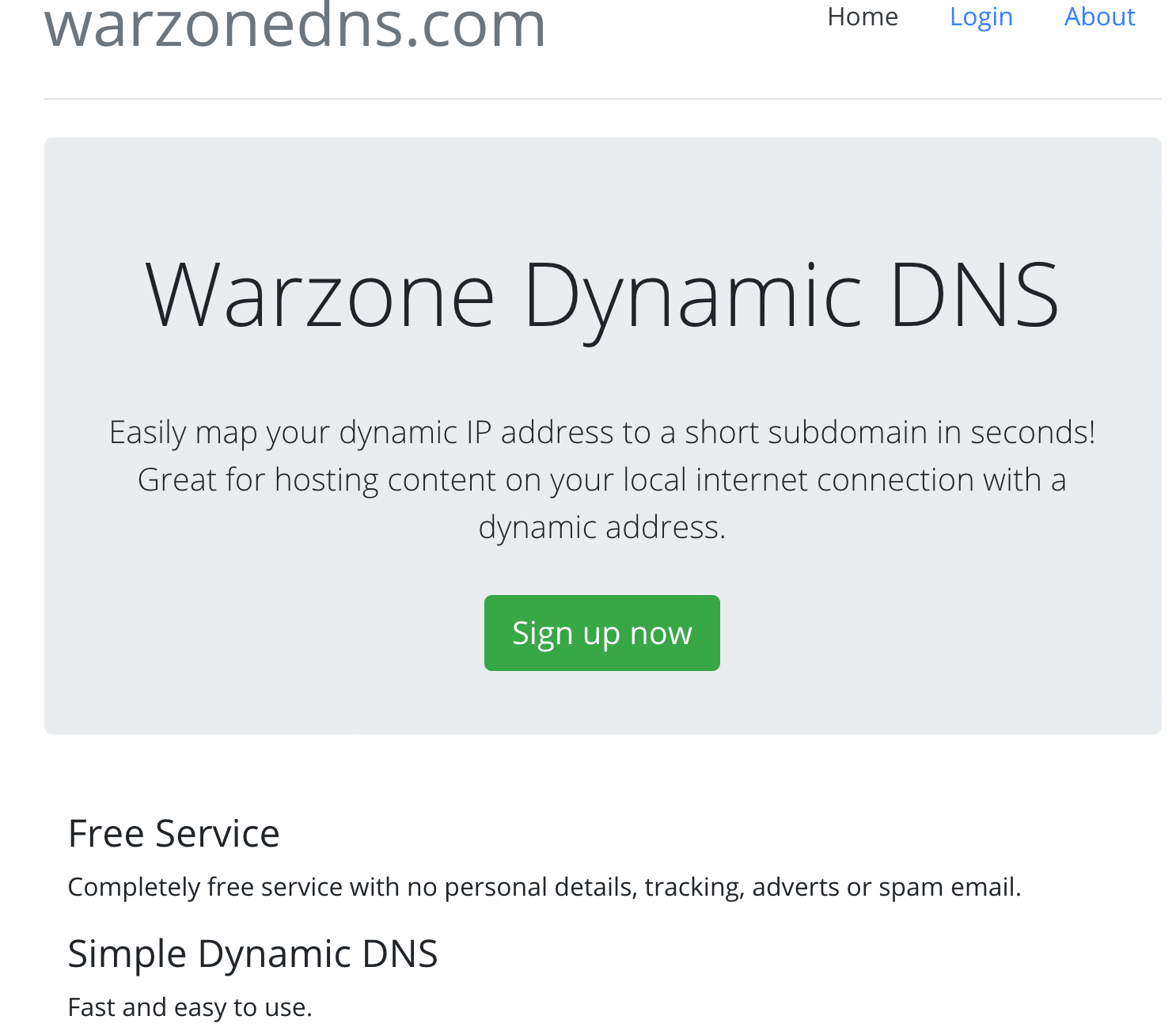
All of the active malware leveraging the Warzone DDNS service as a C2 is no longer effective as of this writing. To be clear, Warzone binaries not leveraging the Warzone DDNS service should still be considered a valid threat to your environment.
‘Warzone.io’ is also down as of October 11th 2019.
Warzone Whack-a-Mole – 0x6
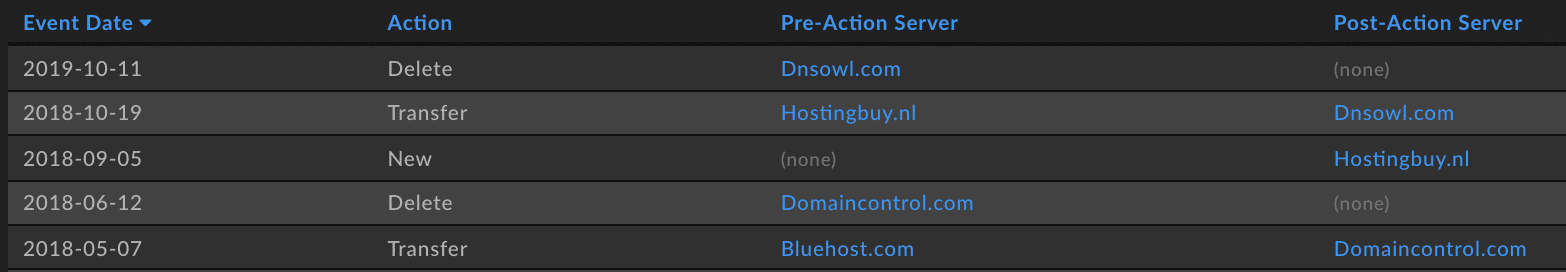
As of October 14th 2019, the Warzone author has spun up new infrastructure to continue selling the commercial RAT. The commercial arm of Warzone lives on under the domain ‘Warzone.pw’ now.
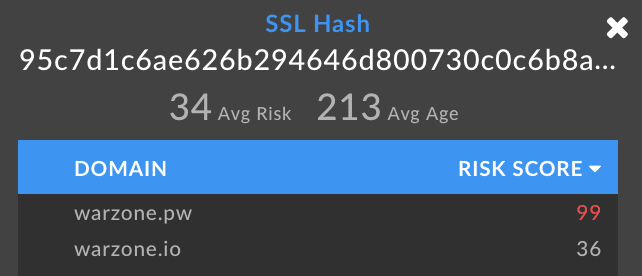
This was detected by monitoring various hacker forum posts as well as leveraging DomainTools Iris platform, which made the connection on the IP address and SSL hash of the previous domain and the new domain.
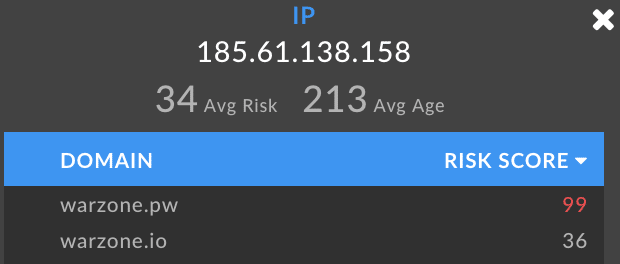
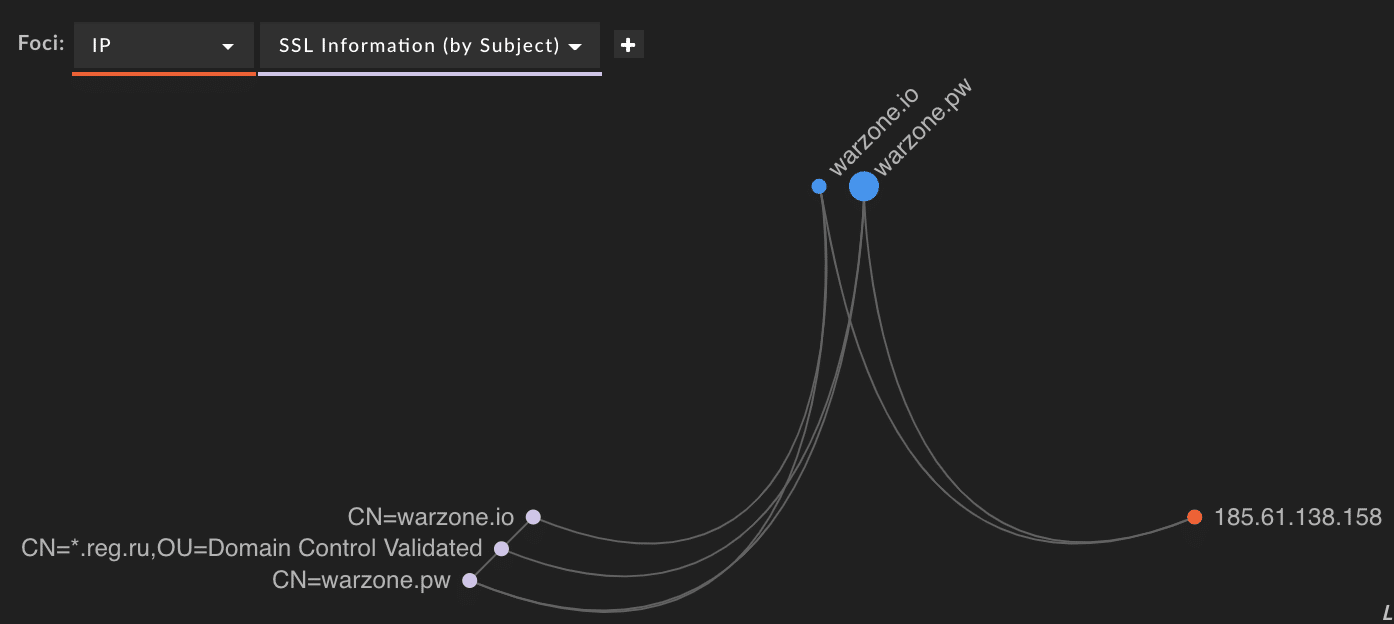
Associated Warzone Domains – 0x7
Diving into historical registrant and WHOIS information, I was able to extract multiple data points that correlated the Warzone domains and others associated with them.
The email registrant information associated with ‘Warzone.pw’ is also associated with the other following domains, each with its own appropriate risk score.
From here, I’m going to obfuscate some of the data that is associated with the Warzone domains and related infrastructure.
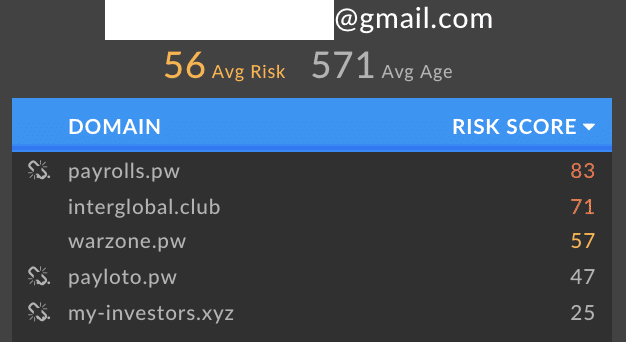
We can visualize these correlations between the historical contact name and email registration data between the newest Warzone domain and other domains, along with risk score for each domain.
Although heavily redacted, I was able to acquire several unique e-mail addresses and full names tying the Warzone infrastructure with other domains. These other associated domains are all stale, but they generally all were associated with sketchy investment avenues.
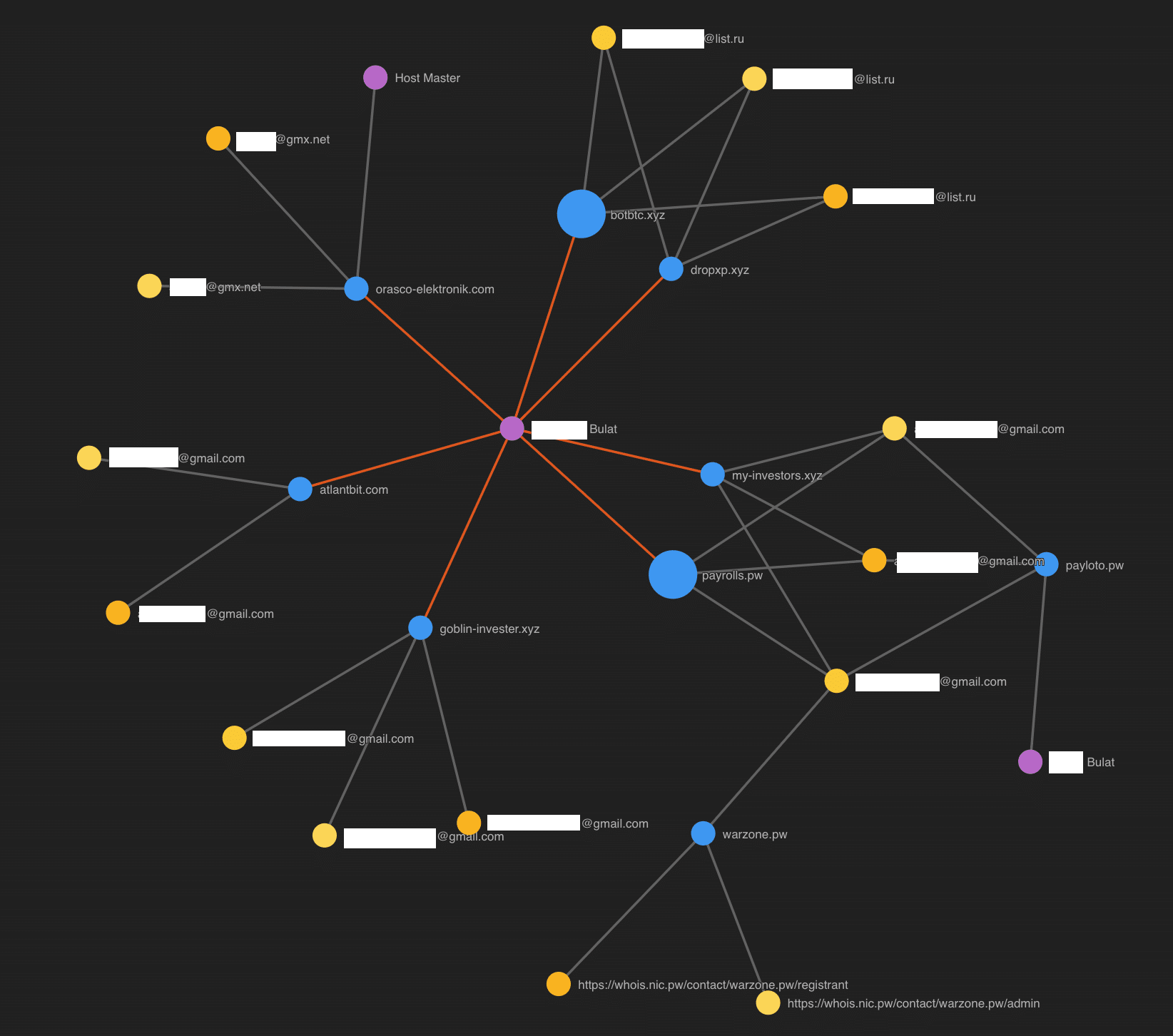
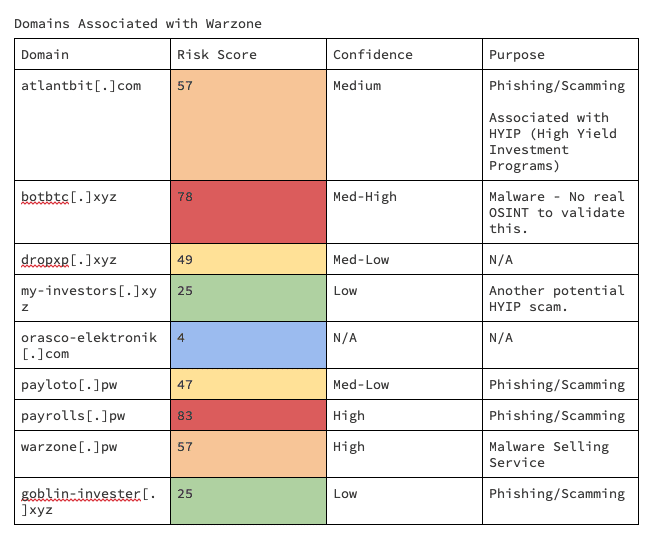
One of the big takeaways we can glean from the associated domains from the Warzone author is the theme of trying to make money, whether scammed or legitimate.
Warzone DDNS Malware Breakdown – 0x8
Malware authors have been evolving their business models into service-based ones, and Warzone is no exception. Warzone offered a dynamic DNS service, both free and subscription-based. This dramatically lowers the technical complexity of managing your own C2 infrastructure.
In my research, not all use cases of the free Warzone DDNS service are actually served for delivering Warzone payloads.
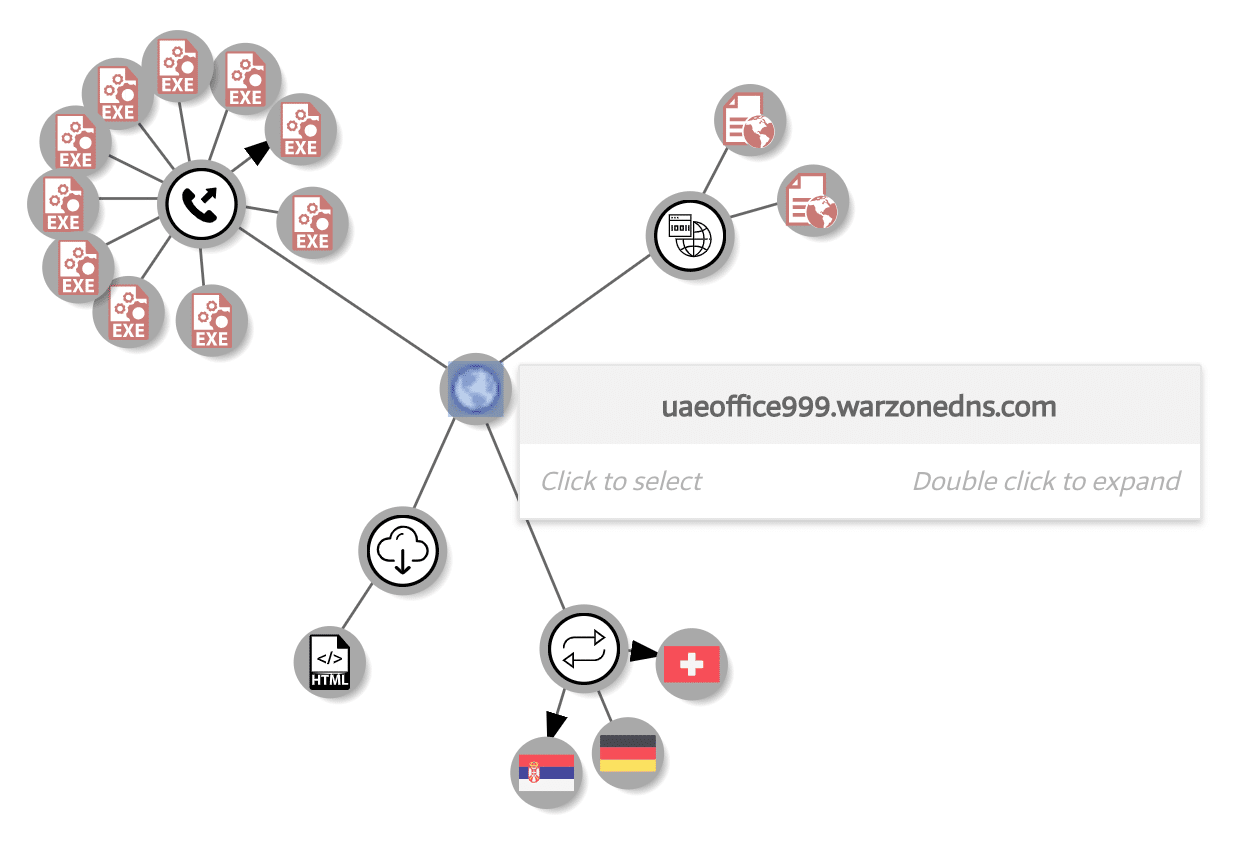
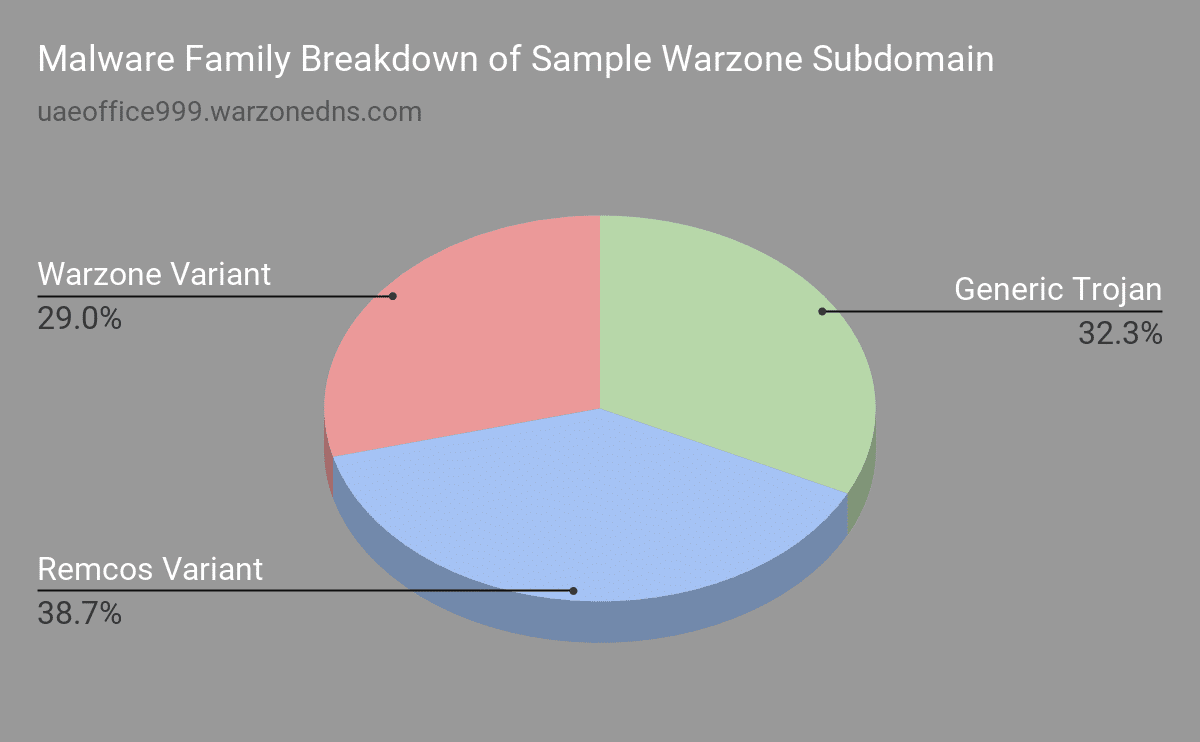
For example, ‘uaeoffice999.warzonedns[.]com’ is associated with other commercial RAT software such as Remcos but leverages Warzone’s DDNS service. In fact, this subdomain has 31 malwares historically associated with it, 39% of which are flagged by AV vendors as Remcos.
Generic Trojans are flagged as having malicious behavior but no overwhelmingly strong signal on malware family. Depending on how the malware is built, it will give various signature definitions by AV vendors. So while this data should not be taken literally, it can still highlight a general trend.
Also, while the Warzone DDNS service was created by the author of Warzone, it was being leveraged by attackers with various malware.
Weaponization & Hunting of Warzone DDNS C2’s – 0x9
According to VirusTotal statistics, there are approximately 7,360 unique malware samples that are associated with the Warzone DDNS C2 service.
One of the upsides (or downsides depending on which side you’re on) of Warzone making its infrastructure management as a service is that it makes it relatively easy to map it out.
Passive DNS data on ‘Warzonedns.com’ bubbles up active and non-active C2 subdomains.
I was able to acquire ‘481’ (As of October 2nd 2019) IPv4 addresses associated with the Warzone dynamic DNS service. As of October 8th 2019, the number of IPv4 addresses associated with Warzone jumped to ‘491’.
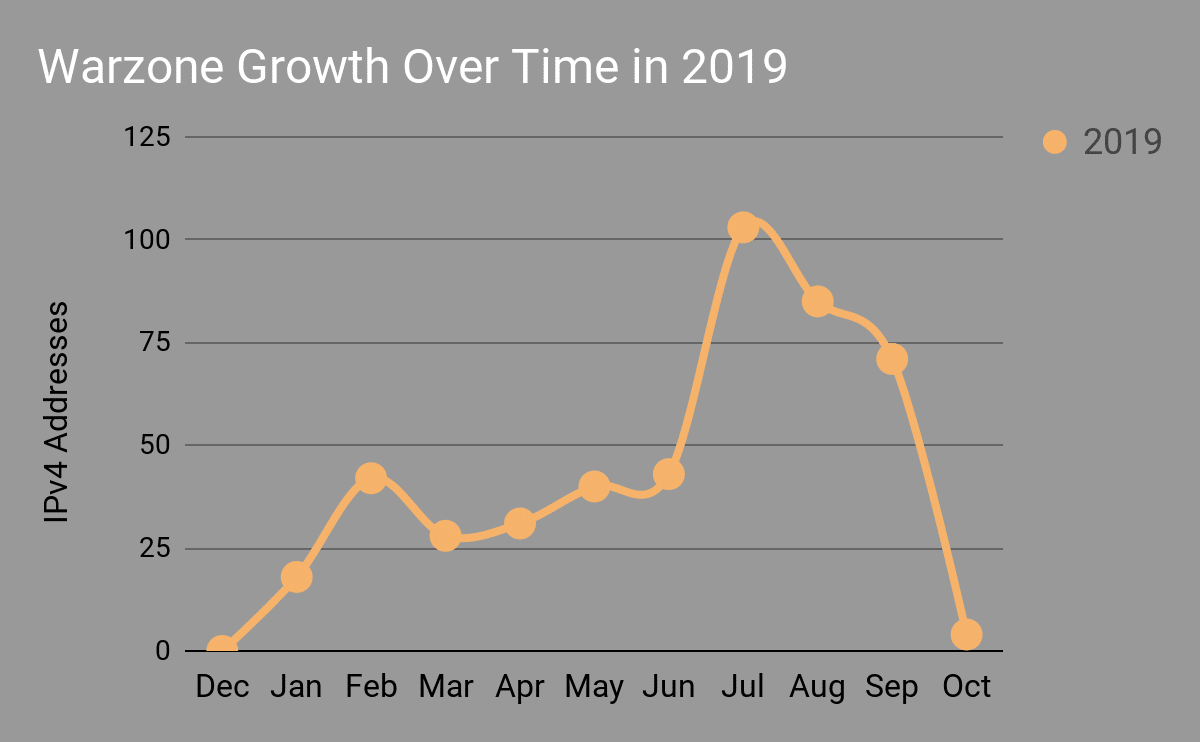
Warzone DDNS C2 Growth Over Time – 0x10
Looking at the pDNS data and filtering on the ‘First Date Seen’, we can glean how the Warzone C2 infrastructure has grown over the past year since the service went public in late 2018. The large downward valley is due to it being early in the month of October as of the time of this writing. One can expect a continual downward trend due to the Warzone DDNS service being taken offline.
An interesting datapoint is the noticeable spike from June 2019 to July 2019, as discovery and submissions of malware samples associated with network behavior to Warzone’s DDNS service on VirusTotal increased.
We can expect the downward trend to flatline for the foreseeable future as the Warzone DDNS service has been taken offline.
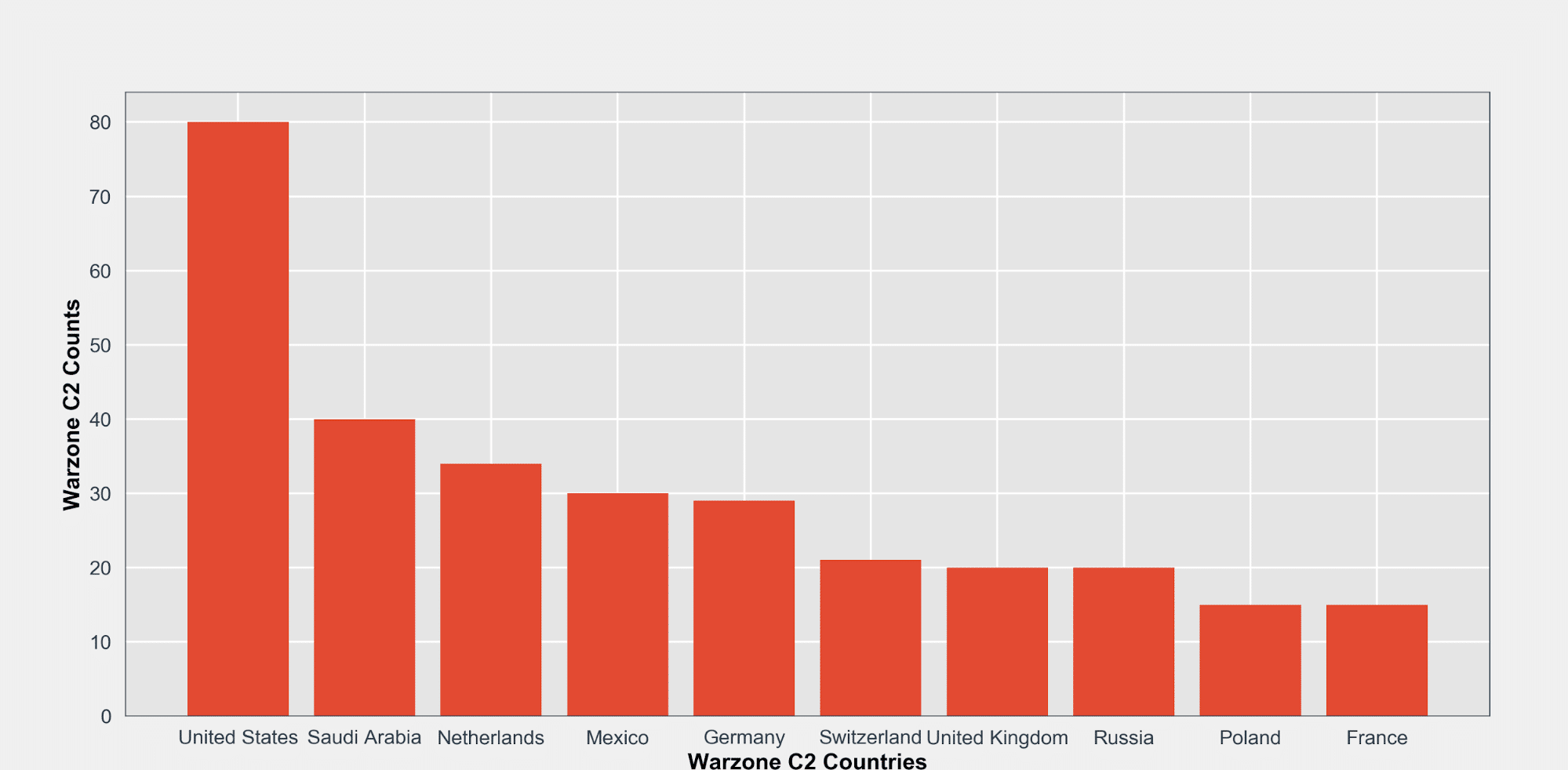
GeoIP Breakdown of Warzone C2’s – 0x11
Leveraging the popular MaxMind GeoIP database and some Python, I was able to quickly glean some interesting statistics on Warzone DDNS C2’s.
Here is a breakdown of the top 10 countries where known Warzone DDNS C2’s are located.
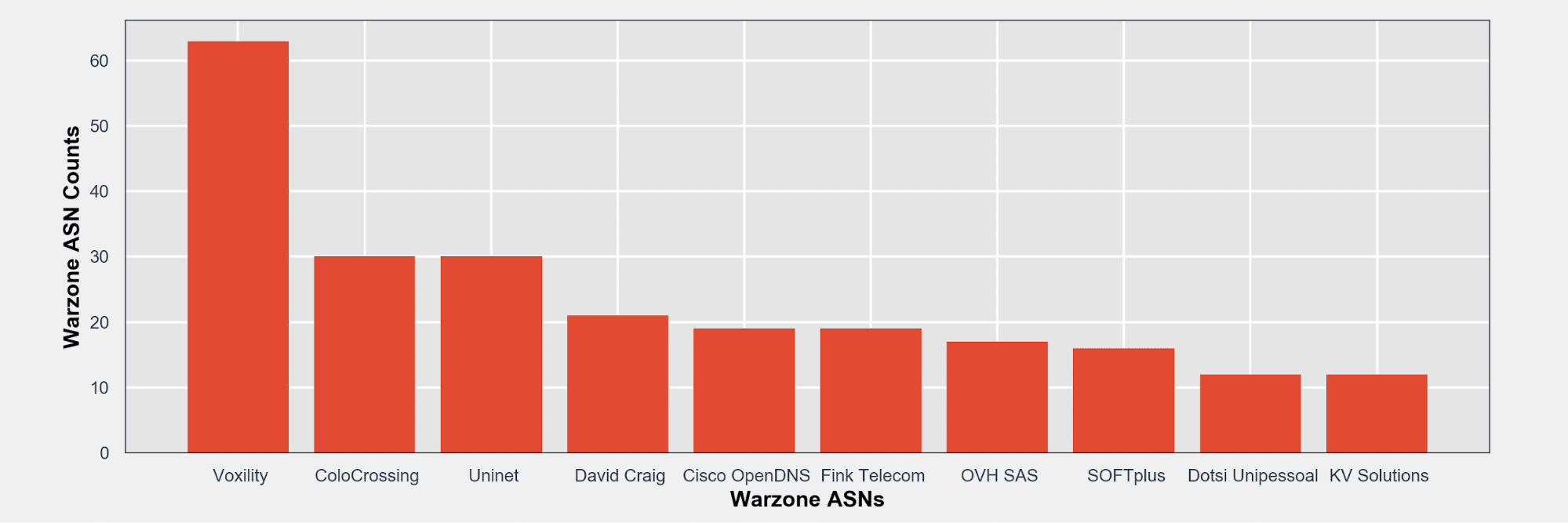
ASN Breakdown of Warzone C2’s – 0x12
Here is a breakdown of the top 10 ASNs associated with known Warzone C2’s.
Detecting Warzone C2 Traffic – 0x13
Although as of October 9th 2019, the Warzone DDNS service (‘Warzonedns.com’) domain appears to be no longer active it still may be worthwhile to hunt across your network for activity associated with the domain, at least from a security hygiene perspective. Keep in mind that the infrastructure behind the domain may come back, in which case the malware C2 would be active again.
Thankfully, it should be relatively trivial to hunt through your DNS or HTTP proxy logs to look for DNS lookups or traffic going to ‘*.warzonedns.com’.
Detecting Warzone Locally – 0x14
A common method used by malware authors to obfuscate their binaries is to compress them using tools called packers (and crypters). Packers essentially take your initial binary, compresseses it and creates a new executable that contains it and a decompression stub file so that when the binary is opened the original executable is decompressed into memory and control transferred to it. This changes the properties of the malware and can bypass some static analysis detection means. A crypter is very similar to packer functionality, however, crypters generally change the behavior of the executable as well for bypassing more sophisticated detection means.
Any sophisticated attacker will leverage different packers or crypters to obfuscate and bypass security detection controls. Each packer or crypter brings their own unique pros and cons but the goal is the same: FUD (Fully UnDetectable).
Analyzing malware statically can have it’s own set of challenges that some say make it more difficult to detect malicious code execution.
For example, ClamAV with the latest signature updates show the Warzone 1.0 unpacked stub binary match with the following:

Packers help, but aren’t always a sure fire bypass. ClamAV can still detect Warzone 1.0 binaries packed with MPRESS.

Sophisticated attackers will leverage crypters to obfuscate their malware from static and even behavioral analysis engines. Leveraging PEUnion to build a compressed (EMPRESS) Warzone 1.0 binary evades ClamAV.

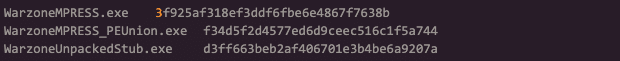
Attempting to use import hashes for various builds of Warzone aren’t going to be effective. We can see the different values that won’t be a match for a signature.
However, let’s keep in mind attackers often times don’t need to be sophisticated to be effective. There are plenty of unpacked malware binaries that are used successfully to bypass security controls and compromise organizations.
Detecting Warzone with YARA – 0x15
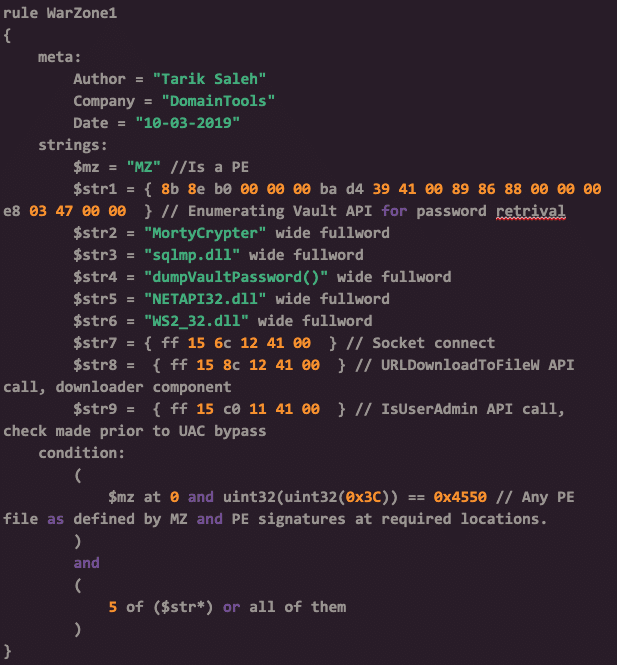
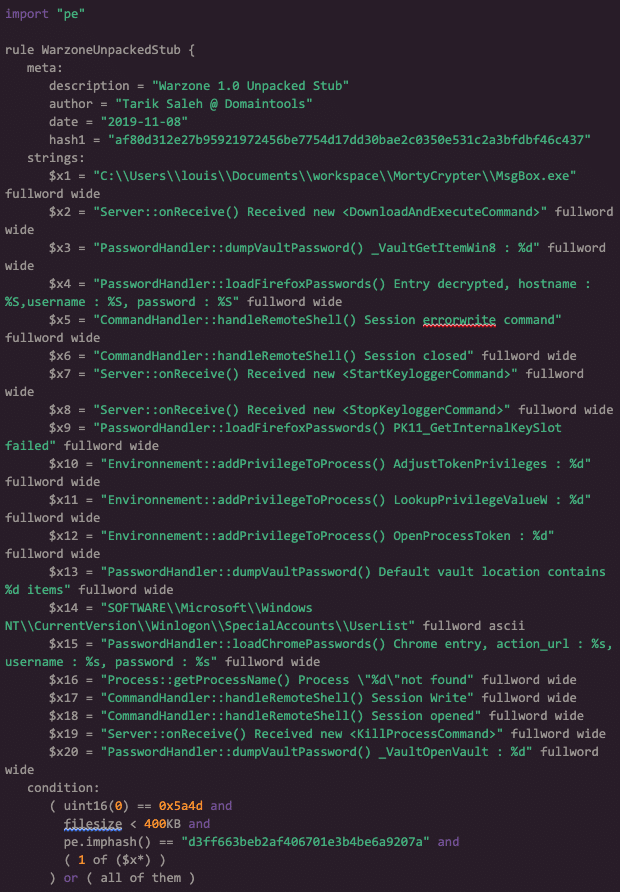
YARA is a tool that can help us statically detect malware, even packed ones. As a starting point, here is a Warzone 1.0 unpacked rule. This rule will only flag binaries that are unpacked and match strings found in Warzone 1.0 executable builds. For more effective matching, I would recommend running these rules while analyzing a sample in your favorite Windows based debugger.
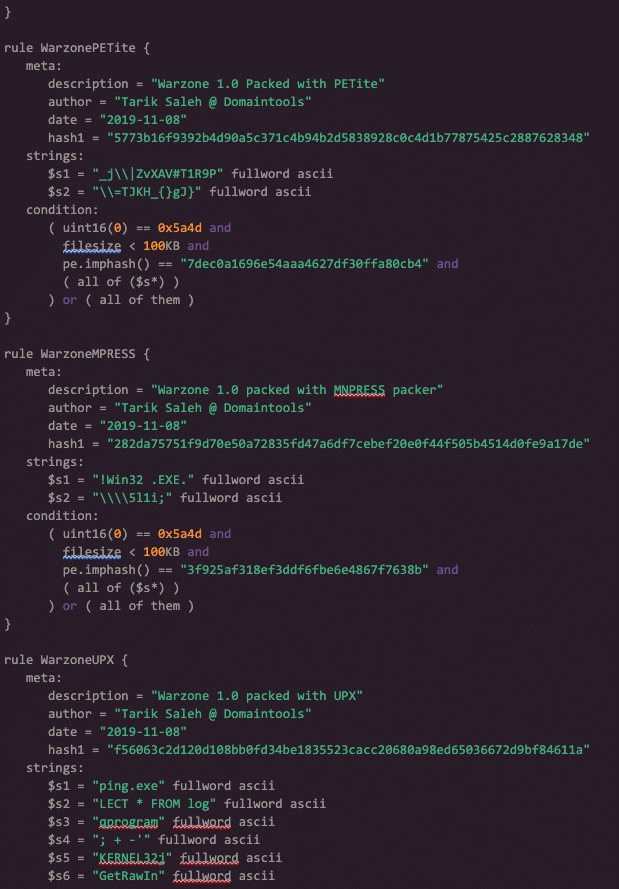
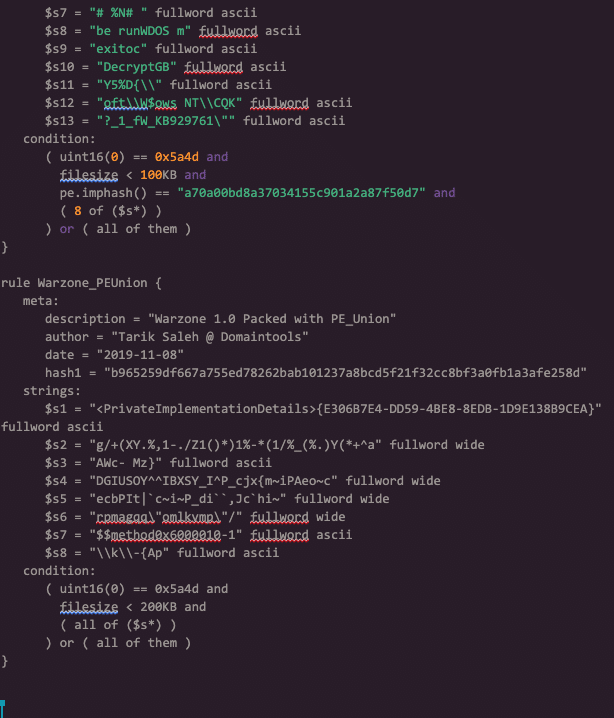
I went ahead and built Warzone 1.0 binaries against popular and most likely to be seen crypter services, and then built a YARA rule accordingly. This rule is one I would use for threat hunting across your environment. Packers such as ‘UPX’, ‘PE_Union’, ‘PETite’ and others were used for this YARA rule.

Warzone Attack Vectors – 0x16
Blue teams can expect to encounter Warzone with the same attack vectors as other common RAT threats: malicious documents & PDFs and trojanized applications. Warzone does not bring any unique or new methods to the table.
As such, it’s critical for security organizations to ensure they have a solid behavioral-based EDR/AntiVirus solutions on their endpoints as well as e-mail filtering appliances that are capable of analyzing attachments.
To hunt for Warzone across your environment, I recommend starting off by searching in your DNS logs for lookups for ‘*.warzonedns.com’. If you have any matches in your DNS logs, you have a great starting point for Warzone infected devices on your network. If you have endpoint instrumentation that allows you to execute YARA rules across your network I would recommend doing so.




