Coming up this week on Breaking Badness. Today we discuss: A Good Ransomware Day, A One Trickbot Pony, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
A Good Ransomware Day
- This particular dirty dozen did do dastardly deeds dependent on deployment of Dharma and definitely deputized the deadly duo LockerGoga and MegaCortex as well. Digging deeper, the dorks displayed dependence on Trickbot, followed by usual suspects Cobalt Strike and PowerShell Empire for lateral movement.
- Dharma ransomware, also known as CrySiS, is a fairly nasty “trojanized” virus targeting Windows used by threat actors to extort home computer users, but also small and medium-sized organizations. Cute factoid about it: in the typical Dharma phish, the user is requested to download a password-protected attachment named Defender.exe.
- Then you got LockerGoga, which was famous among other things for being the warez behind the Norsk Hydro attack in 2019. Once installed, LockerGoga modifies the user accounts in the infected system by changing their passwords. It also tries to log off users logged in to the system. It then relocates itself into a temp folder and rename itself using the command line (cmd). But here’s maybe the cutest thing about it: since LG neither gives the victims a chance to recover the files nor specifically asks for payment, its distribution was most likely targeted and intended to disrupt operations.
- Now how about MegaCortex? Here, the Windows Domain Controller is key. Once a vulnerable domain controller is compromised, the attacker configures it to drop a batch file, PsExec, and winnit.exe, which is the core malware file component to other machines. PsExec is like the advance team that neutralizes the environment so the bad guys can do their deeds–in this case, it will terminate Windows processes and any other services that can halt or prevent the ransomware’s execution flow. Then it spins up that –winnit.exe which searches for files that can be encrypted, and then a DLL with a random-generated filename is also extracted and run with rundll32.exe, doing the encryption. Pretty routine stuff, and keep in mind that these arrests are the culmination of a fairly lengthy effort, so when we’re looking at the malware involved, we’re sort of looking back in time to around 2019. So these aren’t necessarily the latest warez, and there are a lot of detections for them out there.
- Twas the 26th of October, in the far-off lands of Ukraine and Switzerland, that these arrests were made. This was quite the constabulary cooperation, with a total of ten different nations or groups involved, and if you go a layer deeper into those countries and the organizations involved, you’ve got a total of fifteen entities and a total of 50 investigators that worked together on getting these arrests. But how did all this start? Well, with the French. A joint investigation team, which strangely enough has nothing to do with cannabis, was set up in September 2019 between Norway, France, the United Kingdom and Ukraine with financial support from Eurojust. The partners in the JIT have since been working closely together, in parallel with the independent investigations of the Dutch and U.S. authorities, to uncover the actual magnitude and complexity of the criminal activities of these cyber actors to establish a joint strategy. (See, nothing to do with Snoop’s and Willie Nelson’s biggest shared interest.)
- As to where they go from here, any time you’ve got arrests, you’ve got a potential gold mine of sources to potentially make further arrests down the road. And of course there’ll be a lot of forensics they’re going to do on any assets they’ve seized (and I don’t mean just test driving the lambos, though of course that’s always a possibility too).
- We know they suffered from the cyber crime Achilles heel: automotive vanity. But yeah, let’s talk a bit about what they were up to besides lighting cigars with $1,000 Euro bills. The targeted suspects had varying roles in these organizations. Some of them were on the pure tech side, working for example on the penetration phase, using different mechanisms to compromise the victim environments, including brute force attacks, SQL injections, stolen credentials and phishing emails with malicious attachments. Then you had some of them that were more in charge of laundering the ransom payments: they would funnel the Bitcoin ransom payments through mixing services, before cashing out.
- For the dastardly dozen who are now residing behind bars, I can tell you that they are going to have to completely recalibrate both their fashion regimes and their diets. As for the rest of us, I think there are really two ways to look at it. From one point of view, it’s a drop in the bucket…even though the activities represented by the groups that are compromised by these arrests were far-ranging, and thus these are kind of big fish, we know that in the grand scheme of things, it’s not likely that the pace of ransomware is going to slow noticeably, at least not for long. But the other perspective, and the one that I think is more interesting, deals with the question of what we are going to learn from this operation in terms of looking at ways to disrupt the business model, to get even better and more extensive international cooperation, and potentially beneficial changes at the policy level and so forth. Or put simply: can what we learned here help us do more of these, and at increasingly high levels of effectiveness?
A One Trickbot Pony
- I can’t read TrickBot without hearing the intro to Mystery Science Theater 3000. [Horrible Singing] So you’re welcome for that. In any case, TrickBot is a piece of malware that goes back to 2016. Spread through a ton of different methods, it’s evolved over the years originally as a banking trojan, then shifting to stealing keys, propagating through a network, AD credentials, and eventually on to infecting LInux systems as well. On top of that, it is known to install both the Ryuk and Conti families of ransomware. It’s seen now as an initial infection that often leads to the next set of trouble whether that be ransomware or otherwise on your network. TrickBot has been both creative in its mutation and prolific.
- You may remember a few months back that the USDOJ picked up Alla Witte AKA Max, a Latvian national who was accused of writing chunks of the TrickBot code. The research community kind of knew that multiple developers worked on these things, but as the case has progressed it’s kind of appeared that maybe she worked on only individual components, perhaps didn’t know the extent of what she was working on or that this was somehow siloed. I doubt that, but that’s some of the murmur and arguments we’ve seen and certainly other crime groups have done that before, hiring developers to work on a specific component and not telling them about the larger project. Anyways, this new extradition is of Vladimir Dunaev, another person tied to TrickBot, is further showing what the FBI stated in their press release: “Pursuing cyber criminals requires considerable patience, expertise, and resources, but the FBI has a long memory and will ensure that these malicious actors cannot evade detection or avoid the full weight of law enforcement actions.” Great line if you ask me. Anyways, they grabbed Dunaev in Southeast Asia, extraditing him through South Korea, and to the Northern District of Ohio for this case.
- Some key takeaways from the indictment: First is that TrickBot began in 2015 according to the indictment so they must have some intelligence on that I had not seen in the past. On top of that it speaks to there being a much larger TrickBot Group that has used freelance programmers, like Alla Witte it sounds like, to create, deploy, and manage the malware. This indictment carries everything under the sun since Dunaev apparently participated in not just the deployment of the malware, but also wire fraud and bank fraud amongst other things. If all goes according to the DOJ’s prosecution plans then Dunaev will face 60 years in prison.
- Dunaev was involved from the actual computer fraud portion to identity theft to wire and bank fraud. According to documents he was also involved in money laundering. It looks like there are enough counts here that some if not all of them will be proven by the prosecution. As the FBI said, they have a long memory, and one of the horrible things about committing crimes with a computer is that they record everything and leave traces everywhere. Any attack, as we like to say, has a requirement and that’s usually a network component that someone else has tapped.
- I think if the FBI has someone this involved with TrickBot they likely know all the other operators as well. I’d guess that Dunaev wouldn’t have much he could reveal operator wise that they wouldn’t know. Once they have this many counts to charge someone with and are extraditing them they’ve just been twiddling their thumbs waiting for the operator to make a misstep. We know many of these groups are based in Russia and that we can’t extradite from there so I don’t think this will stop the rest of those affiliated with the TrickBot Group from continuing. Might keep them from going on vacation overseas for certain. I doubt this will hamper TrickBot much, but that’s how these big groups will be taken down. Slowly, one at a time, through patience and when their operational security lapses the USDOJ will be waiting at some airport in a country that extradites.
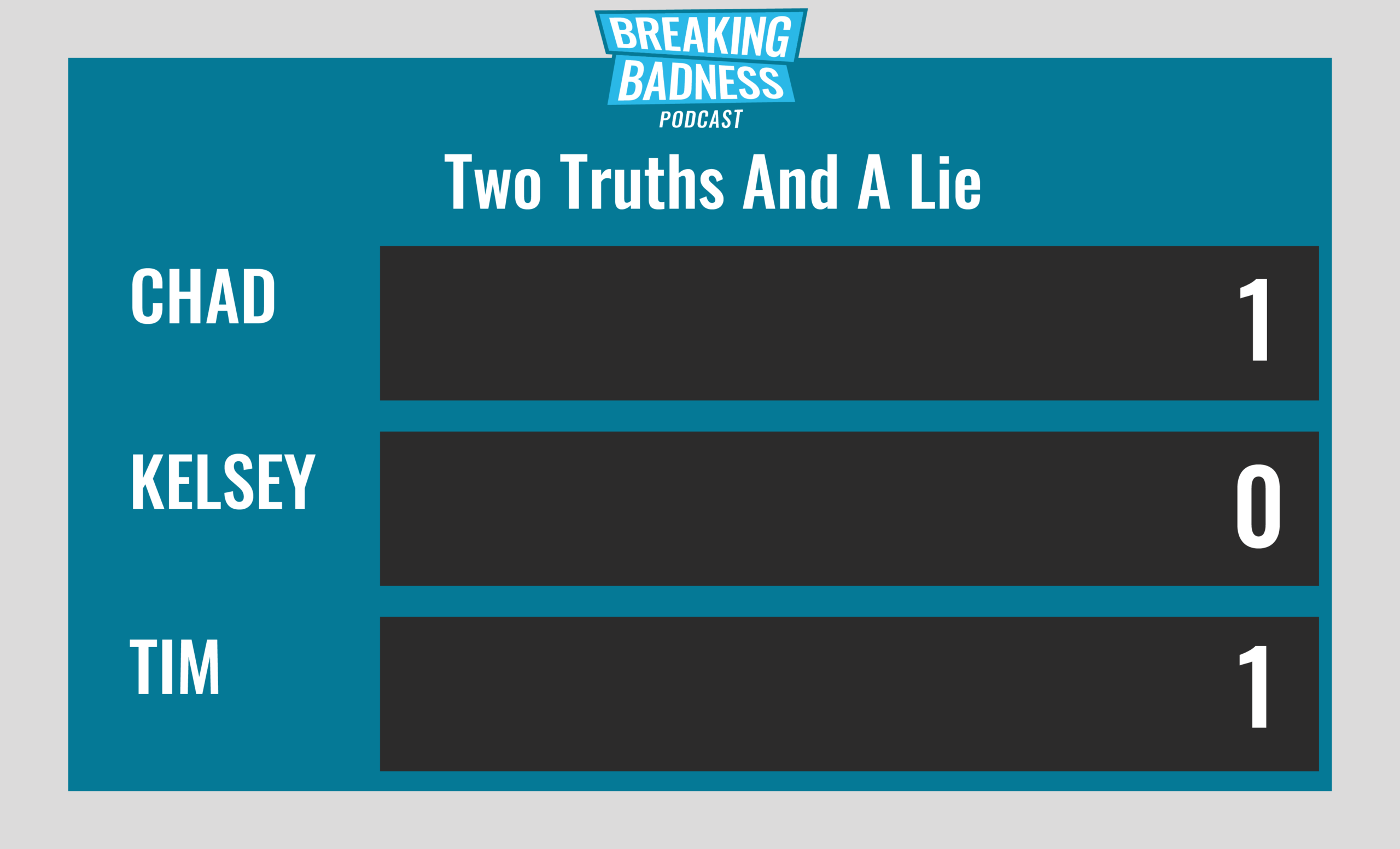
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
A Good Ransomware Day
[Chad]: 9/10 Goodies
[Tim]: 9/10 Goodies
A One Trickbot Pony
[Chad]: 8/10 Goodies
[Tim]: 8/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!