Coming up this week on Breaking Badness. Today we discuss: Okta Breach Party: A Lapsus$ in Judgment, ‘Russian’ Toward Justice, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
Okta Breach Party: A Lapsus$ in Judgment
In January 2022, a security incident at Okta potentially left 366 of its customers affected.
- Okta, for those who may not be aware, is a company that provides two-factor authentication tools for identity and access management
- They provide the means to get a token to use along with your username and password – materials that are quite internal to thwart
- The group identified causing the breach is Lapsus$, also known as Dev0537 by Microsoft
- Lapsus$ has exploded onto the scene recently
- The group has been tracked for a while, and there’s no indication they’ll go away any time soon
- Recently, the BBC reported that the leader of Lapsus$ might be a 16-year-old boy
- However, the age of the bad actor shouldn’t be dismissed because kids can gain coding chops at an early age
- What we know so far regarding the Okta breach is it was reported Lapsus$ had access to their network for a period of 5 days
- The access was obtained through an outsource call center vendor called Sykes (one of their engineers was compromised)
- The controversy is now over what Okta is stating vs. what Lapsus$ is sharing
- If we are to assume Lapsus$ had access to the Okta network for 5 days, they were able to get access to Slack resources and other internal resources within Okta
- They were able to get what’s known as ‘Super User’ access (though Okta maintains that does not entail ‘god-like’ access as their system is built with least privilege in mind.
- We’re hearing statements from Okta, but we’re also hearing a version of the story from Lapsus$ and the truth is likely somewhere in the middle
- It was noted that the attack was in January 2022, but the story didn’t break to the public until March 2022
- It’s a lot longer of a timeframe than the 4-day disclosure window CISA is working toward
- There are issues in not reporting sooner, but to give Okta the benefit of the doubt, it is possible they didn’t know until March
- If they didn’t know, then this information is relatively timely
- For the 366 known customers of Okta who were compromised, if they have been unaware of the breach, then they have been sitting ducks for this whole period of time
- In Okta’s defense, the screenshots Lapsus$ has shared are all from January and there’s nothing at this point to show they’ve been in their network after January
- However, Lapsus$ has stated they’re not interested in Okta – they’re interested in Okta’s customers
- Okta wasn’t the only target of Lapsus$ recently. Microsoft reported they have also been breached and the bad actor involved is Lapsus$
- Microsoft reported a source code breach along with access to signing certificates
- There’s potential for signing certificates: you can write malware, sign it with the certificate, and it will look like legitimate code that came from Microsoft
- There are likely other ramifications we’re not yet aware of, such as obsolete certificates being accepted
‘Russian’ Toward Justice
Last week, The Department of Justice unsealed two indictments charging four defendants, all Russian nationals who worked for the Russian government, with attempting, supporting and conducting computer intrusions that together, in two separate conspiracies, targeted the global energy sector between 2012 and 2018. In total, these hacking campaigns targeted thousands of computers, at hundreds of companies and organizations, in approximately 135 countries.
- These indictments were sealed back in April 2021 and have become unsealed in the past week as the DOJ goes on the offense of publishing names and actions
- In the case of United States v. Evgeny Viktorovich Gladkikh, the alleged crime is an employee of the Russian Ministry of Defense and his co-conspirators damaged critical infrastructure causing two separate emergency shutdowns at a foreign targeted facility
- So this group set their sights on operational technology (OT) targets to cause physical safety systems to stop working
- The conspiracy also attempted to hack computers of a US company that managed similar critical infrastructure entities
- The case of United States v. Pavel Aleksandrovich Akulov, et al., is separate from the above and entails a two-phased campaign by three officers of Russia’s Federal Security Service (FSB) to target and compromise hundreds of entities related to the energy sector worldwide using spear phishing
- Alleged crimes took place between 2012 and 2017 (Phase I being from 2012 to 2014, and Phase II from 2014 to 2017)
- Phase I is known as Dragonfly – supply chain attacks via hiding malware inside legitimate software updates. The malware compromised 17,000 unique devices here and abroad
- Phase II is known as Dragonfly 2.0 and the conspirators transitioned to more targeted compromises focused on the energy sector using spearphishing
- The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) released numerous Tactical Alerts, ICS Alerts, and Malware Analysis Reports
- Because these indictments are from about a year ago, and maybe up to a decade ago, in terms of where we are currently with Ukraine, everyone is on high alert for more of the same
- It’s important to note that this are indictments and not convictions (and really they’re more indictments in absentia)
- No one expects these people to be handed over to the US from the Russian government and in all likelihood, they won’t see the inside of a courtroom
- However, it’s still helpful to share this information so we’re all in the know, have ideas of what to look for, and how to best prepare
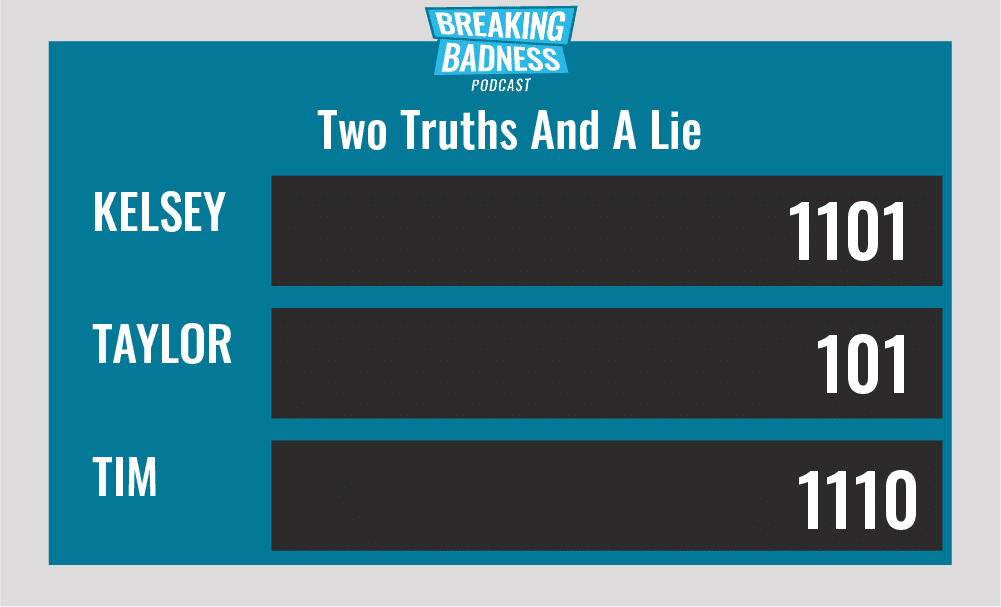
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Okta Breach Party: A Lapsus$ in Judgment
[Taylor]: 6.75/10 Hoodies
[Tim]: 7/10 Hoodies
‘Russian’ Toward Justice
[Taylor]: 2.5/10 Goodies
[Tim]: 4/10 Goodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!