Coming up this week on Breaking Badness. Today we discuss: DDoSOS, I Smell a RAT, and our fun new game, two truths and a lie.
Here are a few highlights from each article we discussed:
DDoSOS
- Ukraine’s computer emergency response team (or CERT-UA) has published a warning of ongoing DDoS attacks targeting pro-Ukraine sites and the government web portal.
- This story is a bit of a two-fer because it’s not only DDoS occurring, but that the mechanism of the attack makes use of compromised WordPress sites
- A threat actor who doesn’t like Ukraine is compromising a large number of WordPress sites
- They are injecting malicious Javascript on these pages, and the javascript directs anyone who visits the site (and whose security controls don’t detect the malcode) is conscripted into the DDoS army
- So then their machine starts sending garbage requests to the sites that are the real targets here, a number of pro-Ukraine sites
- As usual with DDoS, it is not a destructive attack, it just means that legitimate visitors to those pro-Ukraine sites are going to have a harder time getting through
- Often when that’s happening, if you do a page refresh or two, you get through okay
- As mentioned above, the top targets are pro-Ukraine sites including at least one official Ukraine government site and private ones that support Ukraine in repelling the Russian invasion
- If you visit the websites listed in the article, they are legitimate sites, but of course you may or may not be able to access them as DDoS wax and wane.
- Currently, there is no information regarding who may be behind these attacks
- At the time of recording, we only know the threat actor is someone sympathetic to Russia
- As we know, attribution is not easy, and I think the folks who can do that will be saving their efforts for the perpetrators of more destructive attacks
- Keep in mind that some of the things that can sometimes tip off an investigator are not going to be present here
- For example, we’ve all heard about malware variants where something in the code itself or in code comments will signal something about the creator or modifier of that code
- In terms of guarding against these types of attacks, there are two categories of security teams involved here
- First, you’ve got the folks whose job it is to keep these WordPress sites from getting popped
- These folks need to keep their WordPress updated
- The secret is you actually can run a pretty secure WordPress site, but you really have to be on top of things
- Then you’ve got the teams that are tasked with keeping the target sites up and running in the face of attacks like DDoS
- These teams have it a bit harder – you would think that it could be as simple as detecting a garbage request and denying it, while admitting the legitimate ones
- The problem is that the only reason the requests in most DDoSes are “garbage” is that there’s no human actually trying to make the connection
- In other respects they look the same as regular Internet traffic—at least the well-designed ones do, but there are some signatures to many DDoS attacks, so the vendors that provide mitigation sometimes have some options for denying that traffic
- They can also do things like sort of fast-flux the IPs for the sites to try to keep the problem traffic from hitting the right server
- For modest DDoSes, these measures can help, but for the bigger attacks, even the best DDoS mitigation is sometimes brought to its knees
- Not all organizations can afford to have DDoS mitigation in place, and not all hosting providers offer it, or offer a very robust version of it. So sometimes, unfortunately, you just have to ride it out
- First, you’ve got the folks whose job it is to keep these WordPress sites from getting popped
I Smell a RAT
-
- The threat group known as TA410 that wields the sophisticated FlowCloud RAT actually has three subgroups operating globally, each with their own toolsets and targets
- A brief background on TA410
- They’re a cyberespionage group with activity dating back to 2018, though they didn’t come up on the radar until 2019
- Proofpoint discovered a phishing campaign using the malware known as LookBack
- From LookBack came the Remote Access Trojan (RAT), FlowCloud
- FlowCloud can access applications like control of the keyboard, mouse, screen, files, services and processes of an infected computer
- They have loose ties to APT10, a group linked to China’s Ministry of State Security
- The group targets US organizations in the utilities sector as well as diplomatic organizations in the Middle East and Africa
- he research group, ESET, found that TA410 is actually comprised of three subgroups called FlowingFrog, LookingFrog, and JollyFrog
- The groups overlap in TTPs, victimology, and network infrastructure
- They also all have global targets
- They’re a cyberespionage group with activity dating back to 2018, though they didn’t come up on the radar until 2019
- FlowingFrog
- Their name comes from the FlowCloud backdoor trojan
- They share network infrastructure with JollyFrog
- Their targets are usually universities, but have also launched attacks against a mining company and the foreign diplomatic mission of a South Asian country
- FlowingFrog also uses the malicious document builder, Royal Road
- LookingFrog
- This group usually targets diplomatic missions, charity organizations, and entities in government and industrial manufacturing
- Their name comes from the LookBack malware, but they also use X4
- JollyFrog
- This team targets education, religious, and military sectors, but has also been found to target diplomatic missions like the previous groups discussed
- They typically use off-the-shelf tools rather than custom built ones (ex. QuasarRAT and Korplug)
- TA410 is now using an updated version of FlowCloud
- FlowCloud is written in C++ and uses many obfuscation techniques
- The new capabilities can control microphones and trigger recordings, monitor clipboard activities and steal content, monitor file systems, and control camera devices to take pictures
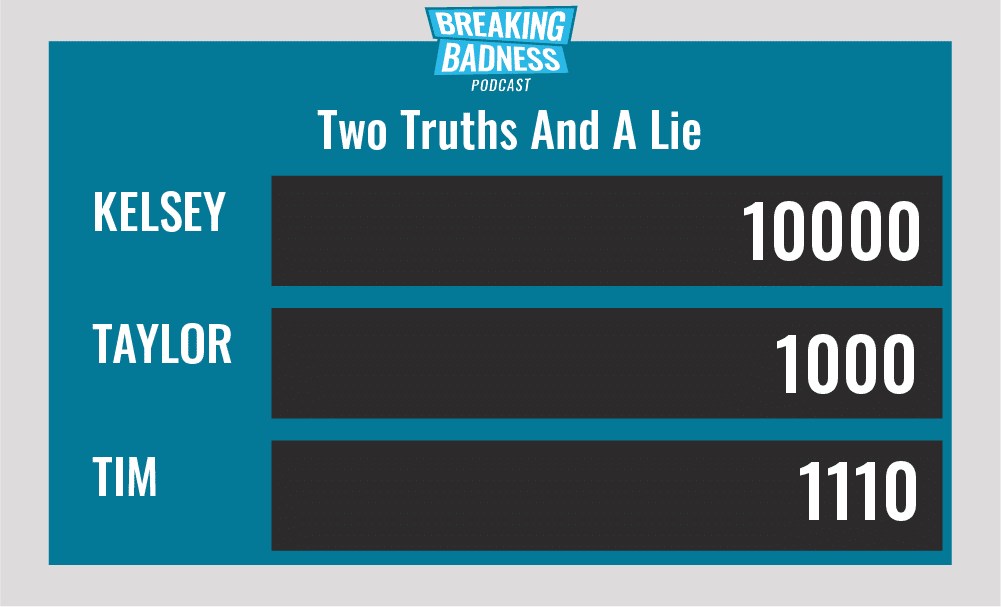
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
DDoSOS
[Taylor]: 3.5/10 Hoodies
[Tim]: 3/10 Hoodies
I Smell a RAT
[Taylor]: 6.5/10 Hoodies
[Tim]: 7/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!