Coming up this week on Breaking Badness. Today we discuss: Summer of TA569, Typosquatter’s Rights, and Two Truths and a Lie.
Here are a few highlights from each article we discussed:
Summer of TA569
- Threat actors are using the compromised infrastructure of an undisclosed media company to deploy the SocGholish JavaScript malware framework (also known as FakeUpdates) on the websites of hundreds of newspapers across the U.S.
- Halloween is over, but we’re still talking about spooky things like SocGholish. Have we seen this malware before?
- We have. Like a vampire out of the coffin again, a lonely ghost returning to its haunts, the proverbial bad penny, this thing has been seen before, is part of this story now, and will undoubtedly show up again in the future
- In a powershell, or actually a nutshell since this malware doesn’t actually use powershell to install, SocGhoulish is basically a piece of first-stage tooling whose purpose in life is really to facilitate later stages of compromise such as the dreaded r-word
- Broadly speaking, this is what you’d consider a supply chain attack, where the key compromise is to a provider that is trusted by a larger network of victim organizations, and then it spreads from there
- The way it happens with SocGhoulish is that it injects malicious code into an otherwise-benign JavaScript file that gets loaded onto the media (newspaper) sites that depend on this unnamed company for video and advertising content
- Once it’s in place, it causes the compromised victim to download later-stage malware disguised as browser updates – in fact, the SocGhoulish JS framework is also known as FakeUpdater. So you see files like chrome.update.zip, firefox.update.zip, and so forth. These file names will slip by unnoticed some of the time, especially if security controls haven’t flagged them and the only hope for detection is human eyes on logs and such
- The attack was discovered by the excellent research team at Proofpoint
- They’ve been tracking this malware and the actors who love it for a few years
- Most recently, they observed injections on a supplier—this aforementioned undisclosed media company that their research alludes to
- As to how they came to be looking for that to begin with, I can only assume that it’s because of the ongoing activities of this group that they’re tracking as TA569 – they must have had some detection hits that matched the TTPs of that group
- The media company is likely unnamed for several reasons
- They could be a potential customer of ProofPoint
- Because of the ongoing investigations, ProofPoint is trying to give them some air cover while they work on it
- The last possibility is they don’t want to invite a further pile-on compromise of that company or the media sites that use it – it could be a containment effort
- How will a victim know they’ve been compromised if they download the fake update?
- There’s nothing that obviously tells them they’ve been pwned, at least not right away. It’s rather ghoulish in that regard
- Instead, they find out when the effects of whatever later-stage tooling this thing downloads occur. So ransomware (typically) or maybe some other kind of infostealer or other nasty
- There are some detections out for this, but it’ll likely be a minute before detections are reliable and widespread
- At this time, we unfortunately don’t know what mitigations are taking place
- We have some thoughts on what we’d put in place, but that’s easy speaking from our ivory podcast tower
- It is a good reminder that when working with third parties, as we all obviously are, the amount of trust we put in those third parties is a risk vector for us. It can be misplaced all the way down
Typosquatter’s Rights
- Phylum researchers have discovered over two dozen Python packages on the PyPI registry that are pushing info-stealing malware
- Phylum, for those who don’t know, is a supply chain auditing company, so this is their bread and butter – they look for these kinds of attacks
- What they found was on PyPI were typosquats of common packages and clones of different common packages with backdoors added to them
- For those who aren’t deep in the Python world, PyPI is a library repository run by the Python Foundation for Python programmers
- If you’re using Python and you want to download a library you don’t already have, there are tools built in Python that will pull these down for you
- The thing is, anyone can sign up to push library supply and you can push things to any name that isn’t already taken
- What happened here is someone signed up, made a copy of a popular package, modified the _INSTALL_ script to include malicious code, and uploaded it to PyPI, then waited for someone to mistype a library they wanted
- What exactly is an _IMPORT_ injection?
- Python lets you import anything you want – you can put imports wherever you want and that’s what these people are taking advantage of
- They’re slipping an _IMPORT_ in where they think you won’t see it – maybe they’ll push it all the way to the right side of the screen
- They’re just adding a little bit that says “import this thing and add that off of the import”
- In the report, the researchers say the malware is “based on an open source project called evil pip published for ‘educational purposes only’” but what exactly do they mean by that phrase?
- Evil pip is up on GitHub – someone put up a proof of concept framework that said “if I want to write a malicious Python package, here’s how I would do it.”
- The idea was “don’t trust things you see on pip because they could look like this giant thing here.”
- But they don’t want to be known for uploading malware, so they said they did it for education and please don’t use this to destroy the world, and of course people do it
- Phylum mentioned this is an ongoing attack, but are there mitigation recommendations?
- The big thing is, the victims have to do something here. They have to have mistyped something. You can’t normally take over a package. So make sure you type dependencies properly and you don’t typo what you meant to pull
- The repositories themselves are starting to take security more seriously
- One thing that has come up is with NPM – the node package manager – they’ve seen people take over well-known libraries using domain names
- NPM has taken a policy to say that any popular libraries need two-factor authentication to be able to upload a new package
- Python is thinking about doing this, but hasn’t yet, so the biggest thing to do now double check you’re not typing stuff
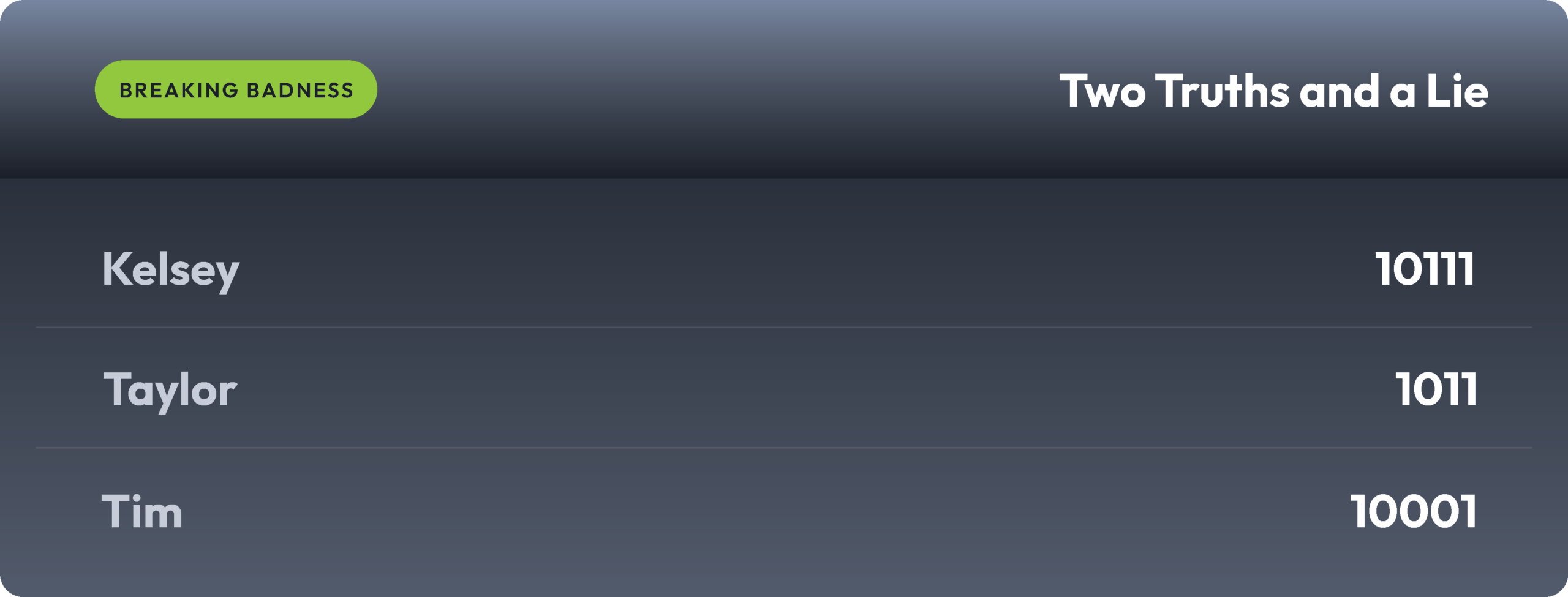
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
Summer of TA569
[Tim]: 5/10 Hoodies
[Aaron]: 5.5/10 Hoodies
Typosquatter’s Rights
[Tim]: 6/10 Hoodies
[Aaron]: 5/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!