Coming up this week on Breaking Badness. Today we discuss: The Long Game, StrelaStealer My Sunshine, and Two Truths and a Lie.
Here are a few highlights from each article we discussed:
The Long Game
- With recent layoffs and a looming recession, cybersecurity has been seen as kind of a “frill” expenditure and personnel is often laid off early on in the cost-cutting process
- It’s probably an understatement to say that the cybersecurity community has been a bit shaken these past few weeks. We open up LinkedIn and layoffs abound. Why is it that in a crisis management plan, cybersecurity is thought of as a ‘nice-to-have’ rather than a ‘need-to-have’ – especially in 2022?
- Business leadership is likely thinking in terms of “keeping the lights on,” if they’re not staring down the barrel of a known breach. It can be a hard decision to lay down cash on security measures when said cash could be allocated toward staffing, or locking in good prices on inventory, or even just salting it away against a rainy day
- A good metaphor is “a lot of people buy their first snow shovel after their first blizzard” and reading stories about what has happened to others doesn’t have the same impact as something that we’re facing ourselves
- But as we deal with the economic uncertainty right now, undoubtedly the most painful choice about discretionary spending, which is how some businesses view beefing up security, is if the only way to do it is to lay off employees. That would be an incredibly tough decision to make, and when it can be hard to tell if cybersecurity programs are working – did it stop attacks, or were there no attacks to begin with – we can see how some leadership would opt to keep the employees on board
- But what are the legalities of cutting cybersecurity teams loose?
- Certainly if there’s a breach and it can be demonstrated that the business was negligent from a compliance or just a fiduciary standpoint, then they could have a significant legal exposure. In many businesses, compliance with data protection regulations is a legal mandate
- Of course, we know compliance does not equal security, but it’s flat out illegal to be noncompliant, that is pretty cut and dry. If somehow you have a business that is exempt from just about any regulation – say you’re Four Seasons Total Landscaping and you work only in cash so you’re not subject even to PCI-DSS, and all your customer records are in Bob’s head because Bob has that kind of mind, well, then the gamble of going without a strong enough infosec program may be one that you’re willing to take on. But most businesses have at least some legal requirements around data protection
- Certainly if there’s a breach and it can be demonstrated that the business was negligent from a compliance or just a fiduciary standpoint, then they could have a significant legal exposure. In many businesses, compliance with data protection regulations is a legal mandate
- What about if cash is really low at a company – where else can cuts be made if not to personnel?
- Whether you have a generous security budget or are right down to the bone, you still should be thinking a lot about priority-ranking your initiatives
- There may be certain ones that make more sense than others and can be cost-effective. Since we’re a DNS-focused company, we’d be remiss if we didn’t mention that there are some security measures that you can take that actually don’t cost you anything other than some minor (and I do mean minor) administrative work: I’m thinking here of protective DNS offerings like IBM’s Quad 9
- Being able to block sketchy domains at the DNS level has a variety of advantages. You can deploy it at any facilities you have, and you can also protect your mobile and remote work force if you’re doing MDM by having all of them use the protective DNS resolver on any work-related devices
- Staying at the network level, one of our old standbys—network segmentation—is another area that we’re fans of
- Think of this like the watertight compartments of a ship, ideally a ship better-designed and more aptly navigated than the Titanic—but if one compartment is breached, with good segmentation, the adjacent ones may not also be breached. This may in some cases also come at a relatively low cost, since most networking devices that any business almost certainly owns can be configured to effectively segment the network. There are a lot of capabilities in those devices that often go underutilized
- Think, too, about things like enabling MFA everywhere. It doesn’t cost anything in terms of CAPEX to have all employees turn on MFA and use OTP authenticator apps on their phones, and we know that MFA has some serious benefits
- So overall, it would make a lot of sense to draw up a list of options that have minimal to zero CAPEX costs and low OPEX costs associated with them, and then put together a roadmap to implement those. These things certainly do not guarantee security nor compliance, but they can absolutely make a meaningful difference
- What if a company is reading this Forbes article and is listening to the podcast, but at the end of the day still believes “a breach will never happen to us, we’re too small for someone to care”?
- Think of the children. I think that’s pretty much the universal bulletproof argument
- No, check that. Tim would say: “Listen up, buckaroos. You know not the day nor the hour, but the horsemen of the data breach are riding into town and it’s going to be a mighty uncomfortable day around here when they show up and not only are your holsters empty, but you’re not wearing pants either, and you left the safe wide open and your whiskey’s all on the bartop and not back on the shelves where it belongs. You’re gonna rue the day you decided that paintin’ up the facade on the storefront was more important than buying some decent padlocks. So go on out into the street and listen. That lonesome wind you’re hearing is bringing a fight you don’t realize you’re in, but make no mistake ladies and gents, you’re in it.” Then he’d tip up the brim of his hat with his six-shooter and stride straight out the door and into the grasp of the security guard that they surely called up while he was telling them all this
- Think of the children. I think that’s pretty much the universal bulletproof argument
StrelaStealer My Sunshine
- A new information-stealing malware named ‘StrelaStealer’ is actively stealing email account credentials from Outlook and Thunderbird, two widely used email clients.
- This malware was discovered by the folks at DSCO CyTec and noted that it’s targeting Spanish-speaking users
- How is this behavior different from other info-stealers?
- Other info-stealers attempt to grab data from multiple data sources (gaming apps, wallet apps, browsers, etc.)
- This one is strictly using email clients
- How does Strelastealer infect a victim’s computer?
- The usual way: via email attachments (ISO files to be specific)
- The researchers also noted that one of the files is of interest because it’s a polyglot file and those types of files can be viewed as different file formats
- The file can act as two things: a DLL program and an HTML file
- After the file is opened and the malware is loaded, a browser opens to an unassuming page, making it seem less suspicious
- StrelaStealer is looking for password data and then exfiltrates back to the C2 server
- It’s likely that these are highly targeted attacks, but at the present time, researchers can’t determine more information
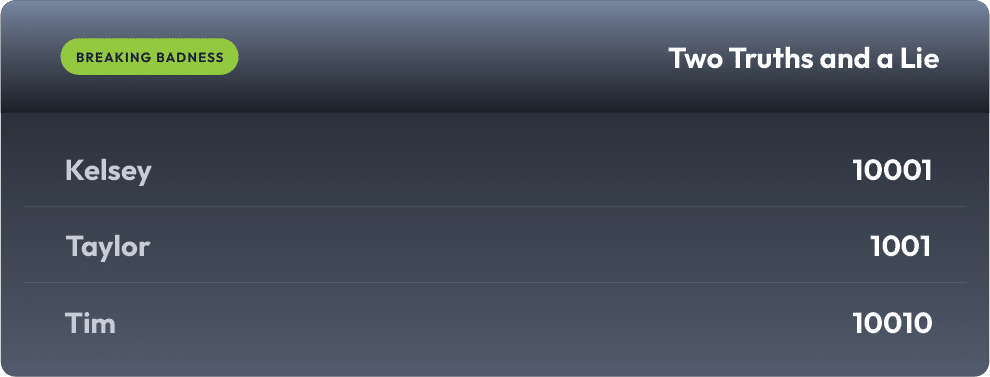
Two Truths and a Lie
Introducing our newest segment on Breaking Badness. We are going to play a game you are all likely familiar with called two truths and a lie, with a fun twist. Each week, one us with come prepared with three article titles, two of which are real, and one is, you guessed it, A LIE.
You’ll have to tune in to find out!
Current Scoreboard
This Week’s Hoodie/Goodie Scale
The Long Game
[Taylor]: 10/10 Hoodies
[Tim]: 9.66/10 Hoodies
StrelaStealer My Sunshine
[Taylor]: 3.14/10 Hoodies
[Tim]: 4/10 Hoodies
That’s about all we have for this week, you can find us on Twitter @domaintools, all of the articles mentioned in our podcast will always be included on our podcast recap. Catch us Wednesdays at 9 AM Pacific time when we publish our next podcast and blog.
*A special thanks to John Roderick for our incredible podcast music!